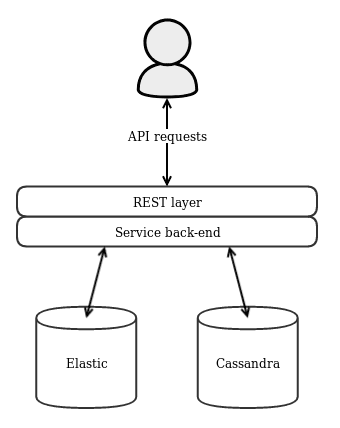
EventList EventList is a tool to help to improve your Audit capabilities and to help to build...
Defense
Semi-Automated Cyber Threat Intelligence – ACT Platform Semi-Automated Cyber Threat Intelligence (ACT) is a research project led by...
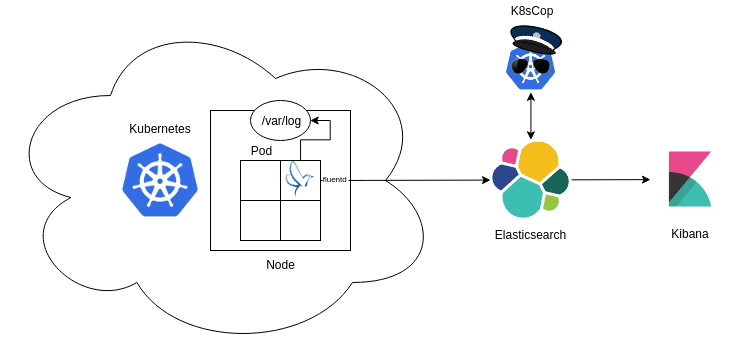
Kubernetes Security Dashboard This guide assists in configuring a logging architecture for Kubernetes meant to store and...
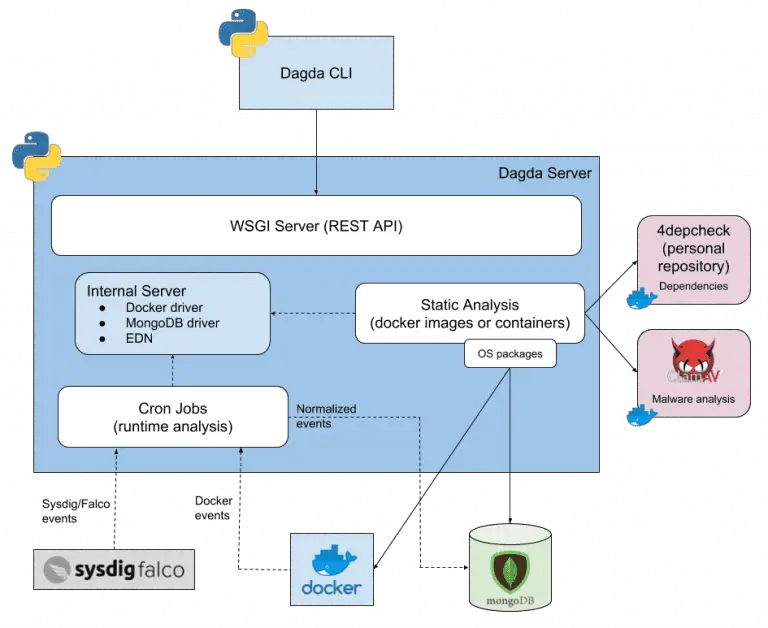
Dagda is a tool to perform static analysis of known vulnerabilities, trojans, viruses, malware & other malicious threats...
Anti-DDOS | BASH SCRIPT Anti-DDOS project is an open source software project developed to protect against DOS...
Tylium Primary data pipelines for intrusion detection, security analytics, and threat hunting These files contain configuration for...
CloudMapper CloudMapper generates network diagrams of Amazon Web Services (AWS) environments and displays them via your browser....
Adama Searches For Threat Hunting and Security Analytics A collection of known log and/or event data searches...
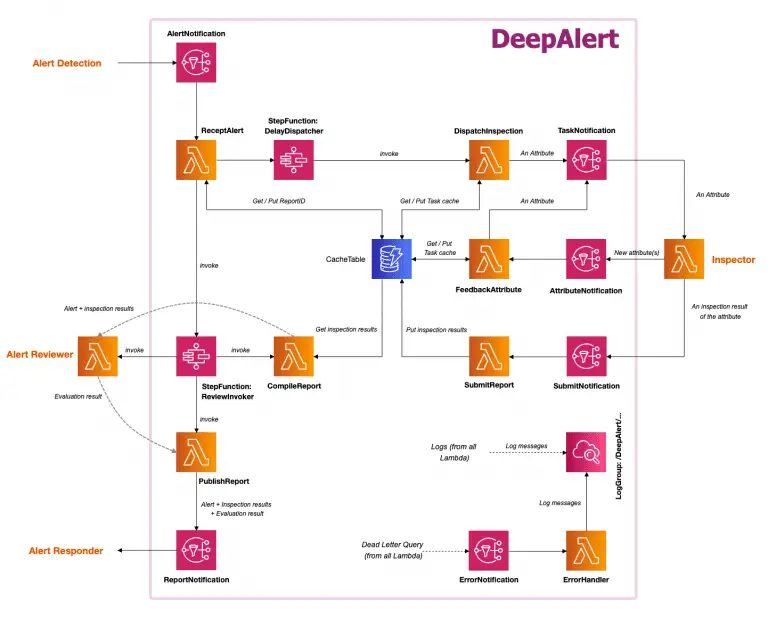
DeepAlert Serverless application framework for automatic inspection and evaluation of security alert Architecture Install Prerequisite (deployment and...
BLUESPAWN What it does BLUESPAWN helps blue teams monitor Windows systems in real-time against active attackers by...
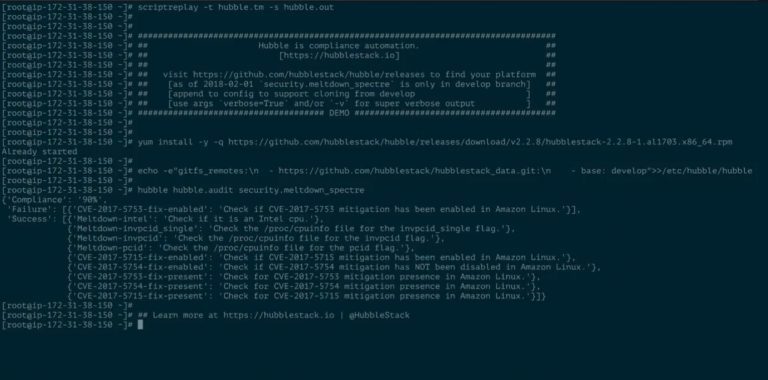
HubbleStack (Hubble for short) is a modular, open-source, security & compliance auditing framework which is built in...
The Cyberprobe project is an open-source distributed architecture for real-time monitoring of networks against attack. The software...
Wireshark Analyzer is a fantastic multi-platform open-source network protocol analyzer. It can be used to check the...
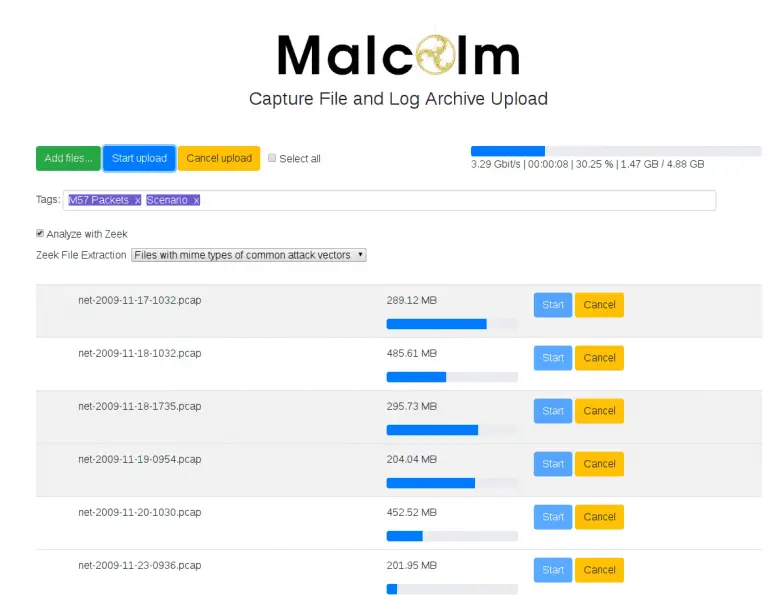
Malcolm is a powerful network traffic analysis tool suite designed with the following goals in mind: Easy to...
terraform-aws-secure-baseline A terraform module to set up your AWS account with the reasonably secure configuration baseline. Most...