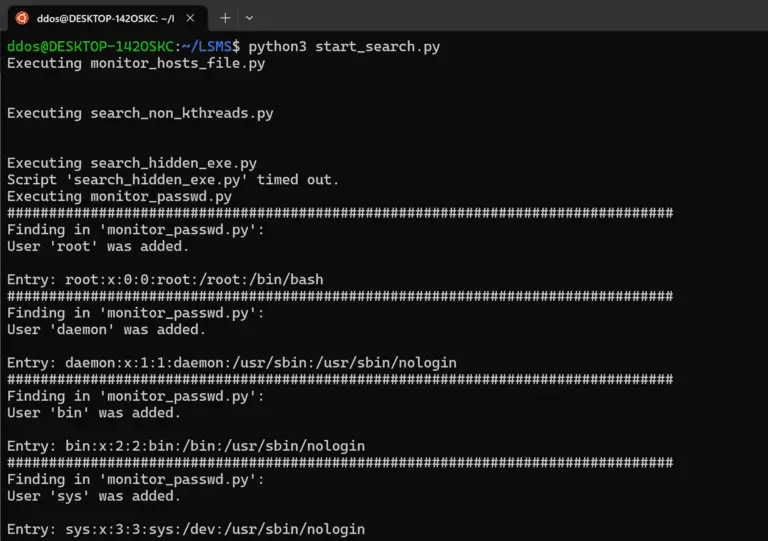
Linux Security and Monitoring Scripts These are a collection of security and monitoring scripts you can use...
Forensics
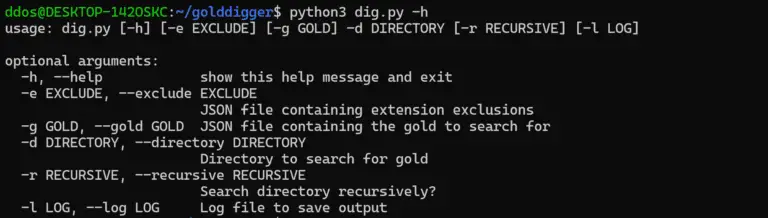
Gold Digger Search files for gold Gold Digger is a simple tool used to help quickly discover...
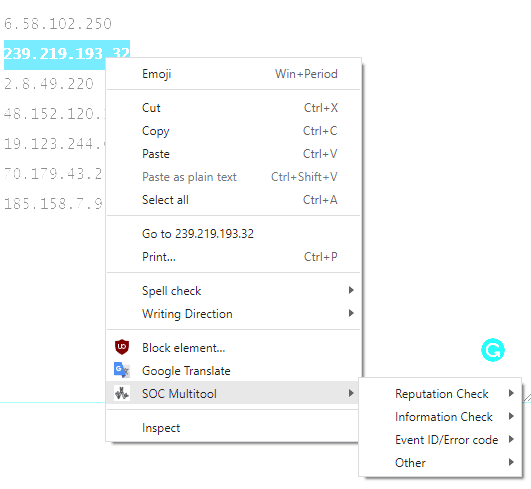
SOC Multi-tool Introducing SOC Multi-tool, a free and open-source browser extension that makes investigations faster and more...
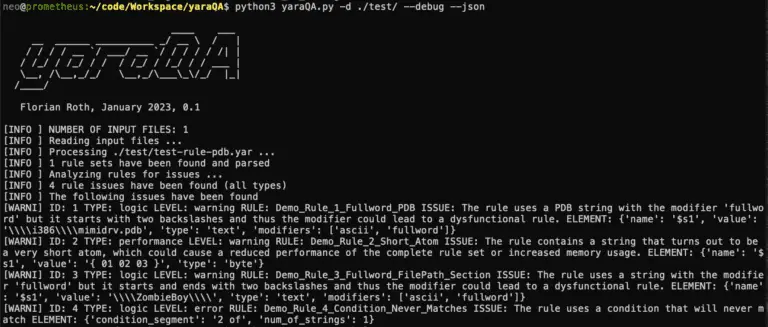
yaraQA YARA rule Analyzer to improve rule quality and performance Why? YARA rules can be syntactically correct...
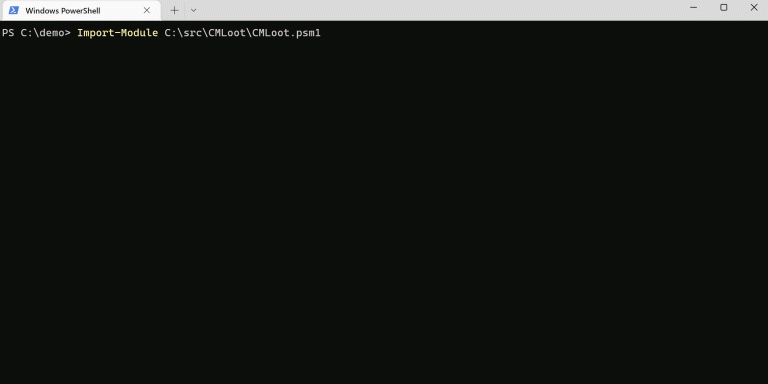
CMLoot CMLoot was created to easily find interesting files stored on System Center Configuration Manager (SCCM/CM) SMB...
reportly Reportly is an AzureAD user activity report tool. This is a tool that will help blue...
Indicator-of-Compromise (IOC) Matching IOC matching for incident responders, threat hunters, detection engineers, and security engineers. Use Cases...
FarsightAD FarsightAD is a PowerShell script that aims to help uncovering (eventual) persistence mechanisms deployed by a...
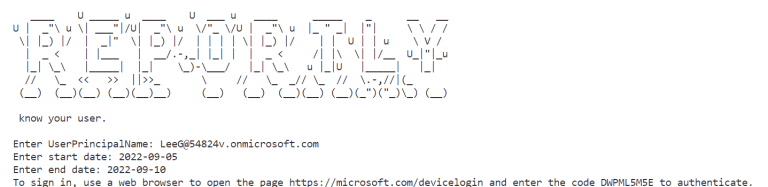
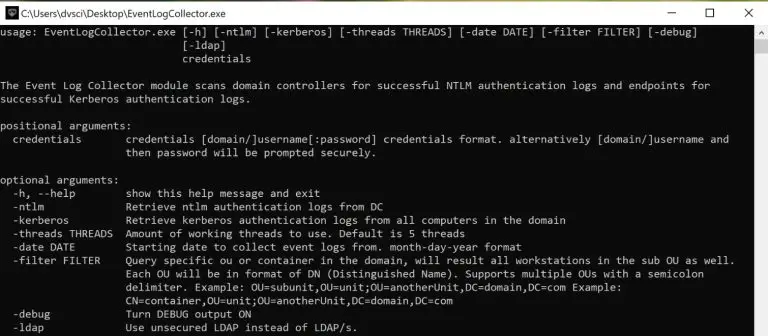
Lateral movement analyzer tool Lateral movement analyzer (LATMA) collects authentication logs from the domain and searches for...
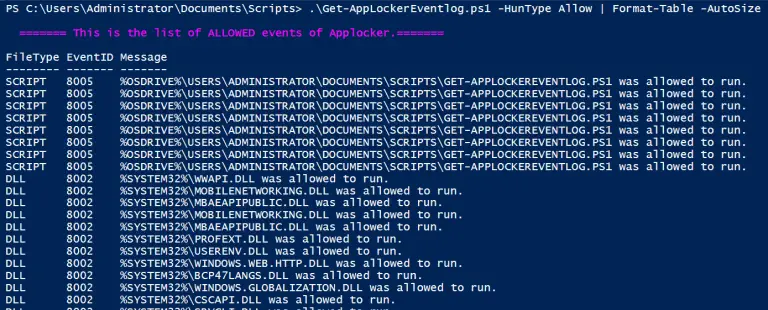
Get-AppLockerEventlog This script will parse all the channels of events from the win-event log to extract all...
Aftermath Aftermath is a Swift-based, open-source incident response framework. Aftermath can be leveraged by defenders in order...
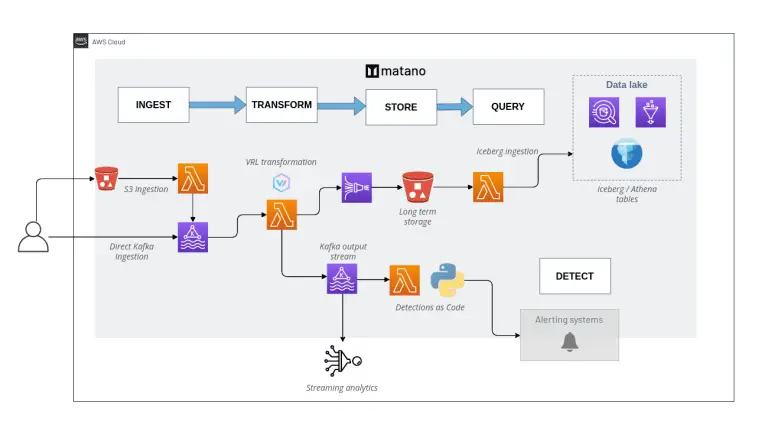
What is Matano? Matano is an open-source security lake platform for AWS. It lets you ingest petabytes...
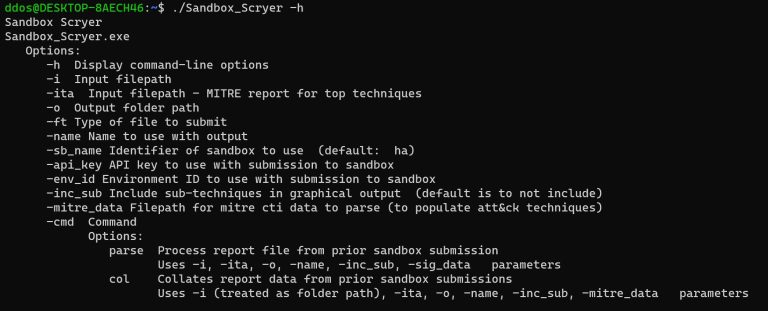
Sandbox Scryer The Sandbox Scryer is an open-source tool for producing threat hunting and intelligence data from...
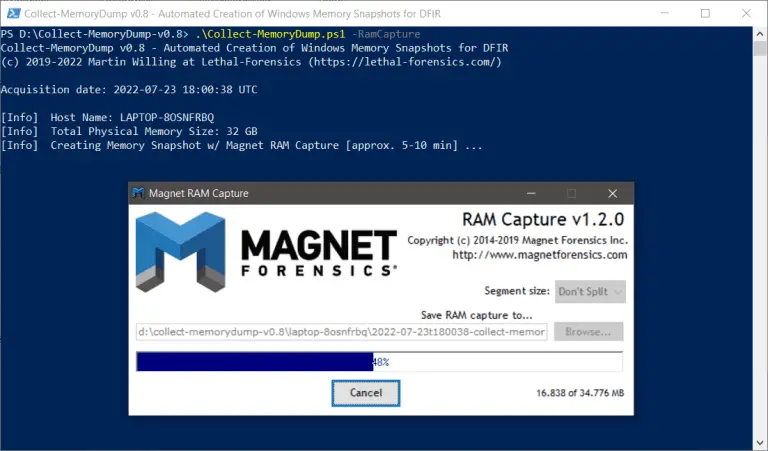
Collect-MemoryDump Collect-MemoryDump – Automated Creation of Windows Memory Snapshots for DFIR Collect-MemoryDump.ps1 is a PowerShell script utilized...
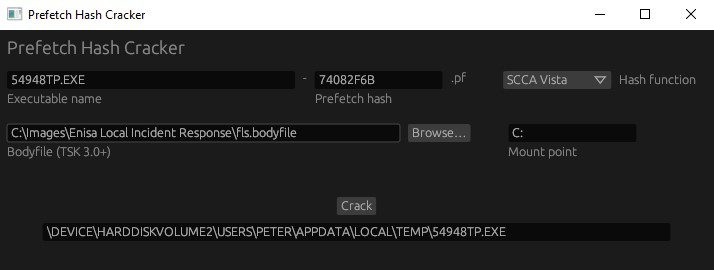
Prefetch Hash Cracker During the forensic analysis of a Windows machine, you may find the name of...