Category: Network PenTest
GraphGenie GraphGenie is a bug-finding tool to detect logic bugs and performance issues (we also find internal errors) in graph database management systems. Specifically, unlike most existing testing works mutating query predicates, GraphGenie leverages...
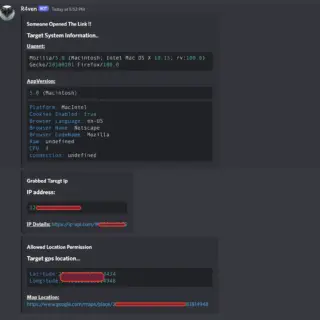
r4ven The tool hosts a fake website that uses an iframe to display a legit website and, if the target allows it, it will fetch the Gps location (latitude and longitude) of the target,...
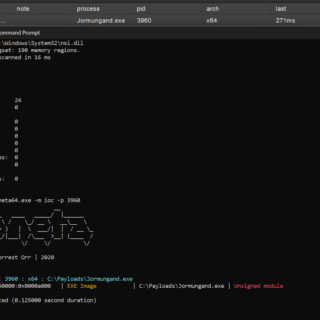
Jomungand Shellcode Loader with memory evasion by @DallasFR How does it work? I use HWBP to hook VirtualAlloc, Sleep, and LoadLibraryA. Why do I hook this function? VirtualAlloc: CobaltStrike & Meterprter is reflective dll...
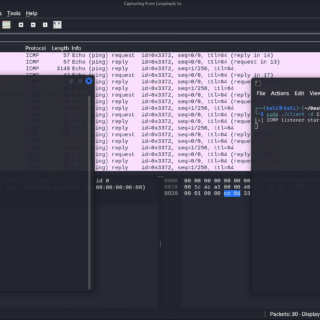
PingRAT PingRAT secretly passes C2 traffic through firewalls using ICMP payloads. Features: Uses ICMP for Command and Control Undetectable by most AV/EDR solutions Written in Go Use Server Client Download Copyright (C) 2023
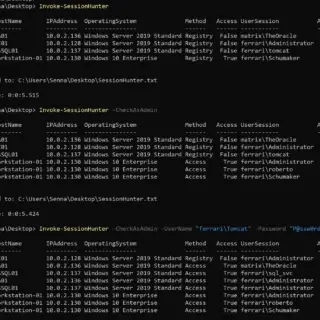
Invoke-SessionHunter Retrieve and display information about active user sessions on remote computers. No admin privileges are required. The tool leverages the remote registry service to query the HKEY_USERS registry hive on the remote computers....
Above Invisible protocol sniffer for finding vulnerabilities in the network. Designed for pentesters and security professionals. Mechanics Above is an invisible network sniffer for finding vulnerabilities in network equipment. It is based entirely on...
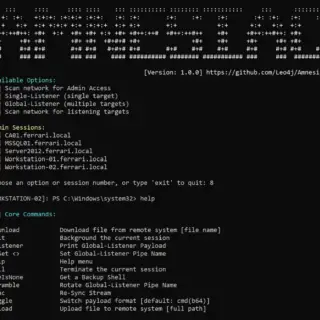
Amnesiac Amnesiac is a post-exploitation framework designed to assist with lateral movement within active directory environments. Amnesiac is being developed to bridge a gap on Windows OS, where post-exploitation frameworks are not readily available...
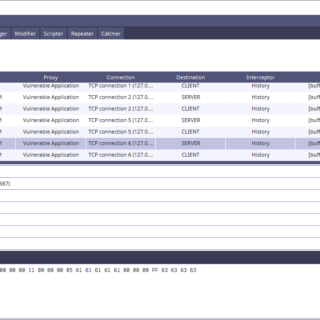
PEnetration TEsting Proxy PETEP (PEnetration TEsting Proxy) is an open-source Java application for creating proxies for traffic analysis & modification. The main goal of PETEP is to provide a useful tool for performing penetration tests...
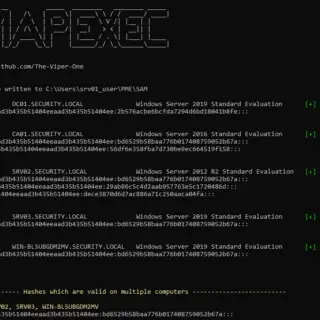
What is PsMapExec A PowerShell tool heavily inspired by the popular tool CrackMapExec. Far too often I find myself on engagements without access to Linux in order to make use of CrackMapExec. PsMapExec is...
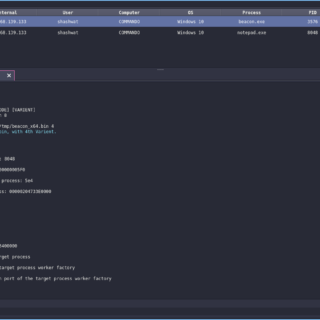
PoolParty A collection of fully-undetectable process injection techniques abusing Windows Thread Pools. Presented at Black Hat EU 2023 Briefings under the title – The Pool Party You Will Never Forget: New Process Injection Techniques Using...
BadZure BadZure is a PowerShell script that leverages the Microsoft Graph SDK to orchestrate the setup of Azure Active Directory tenants, populating them with diverse entities while also introducing common security misconfigurations to create...
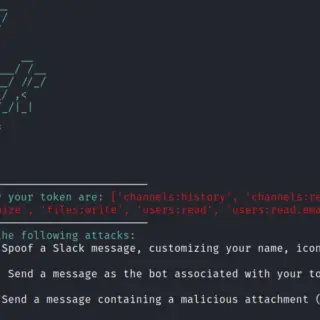
EvilSlackbot A Slack Attack Framework for conducting Red Team and phishing exercises within Slack workspaces. Background Thousands of organizations utilize Slack to help their employees communicate, collaborate, and interact. Many of these Slack workspaces...
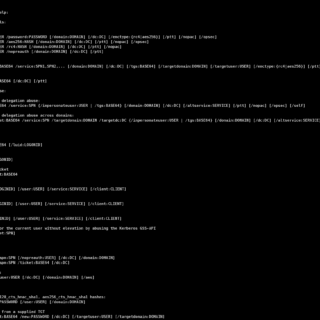
Kerbeus-BOF Beacon Object Files for Kerberos abuse. This is an implementation of some important features of the Rubeus project, written in C. The project features integration with the C2 frameworks Cobalt Strike and Havoc. Download git clone https://github.com/RalfHacker/Kerbeus-BOF.git Use...
RTI-Toolkit RTI-Toolkit is an open-source PowerShell toolkit for Remote Template Injection attacks. This toolkit includes a PowerShell script named PS-Templator.ps1 which can be used from both an attacking and defensive perspective. The following tables present...
LDAPWordlistHarvester A tool to generate a wordlist from the information present in LDAP, in order to crack non-random passwords of domain accounts. Features The bigger the domain is, the better the wordlist will be....