Category: Network PenTest
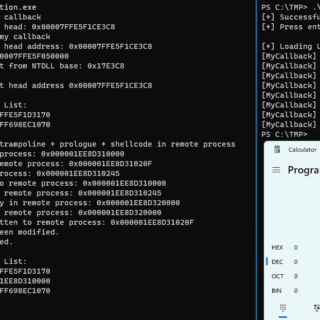
Process Stomping A variation of ProcessOverwriting to execute shellcode on an executable’s section What is it Process Stomping, is a variation of hasherezade’s Process Overwriting and it has the advantage of writing a shellcode payload on...
PySQLRecon PySQLRecon is a Python port of the awesome SQLRecon project by @sanjivkawa. See the commands section for a list of capabilities. Commands All of the main modules from SQLRecon have equivalent commands. Commands noted with [PRIV] require elevated...
EDRSandblast-GodFault Integrates GodFault into EDR Sandblast, achieving the same result without the use of any vulnerable drivers. EDRSandBlast is a tool written in C that weaponizes a vulnerable signed driver to bypass EDR detections (Notify Routine callbacks, Object...
PPLBlade Protected Process Dumper Tool that supports obfuscating memory dump and transferring it on remote workstations without dropping it onto the disk. Key functionalities: Bypassing PPL protection Obfuscating memory dump files to evade Defender...
nysm: A stealth post-exploitation container With the rise in popularity of offensive tools based on eBPF, going from credential stealers to rootkits hiding their own PID, a question came to our mind: Would it...
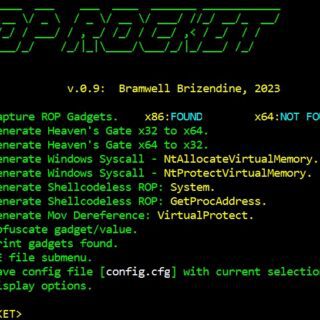
Introducing the ROP ROCKET This new, advanced ROP framework made its debut at DEF CON 31 with some unprecedented capabilities. ROCKET generates several types of chains, and it provides new patterns or techniques. Please...
Mavoc C2 Framework Mavoc is a tool used to pentest Windows and Linux machines. This tool mainly Focuses on Pentesting Windows. Made with using C++, and Powershell, and the server is made with Python...
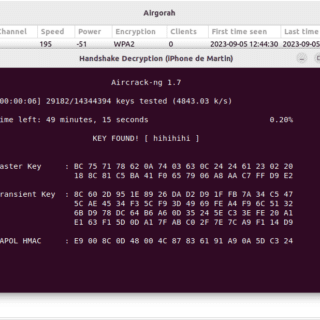
airgorah Airgorah is a WiFi auditing software that can discover the clients connected to an access point, perform deauthentication attacks against specific clients or all the clients connected to it, capture WPA handshakes, and crack...
DllNotificationInjection DllNotificationInection is a POC of a new “threadless” process injection technique that works by utilizing the concept of DLL Notification Callbacks in local and remote processes. An accompanying blog post with more details...
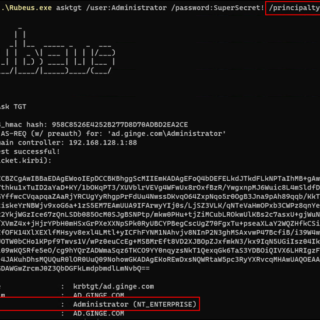
gssapi-abuse gssapi-abuse was released as part of my DEF CON 31 talk. A full write-up on the abuse vector can be found here: A Broken Marriage: Abusing Mixed Vendor Kerberos Stacks The tool has...
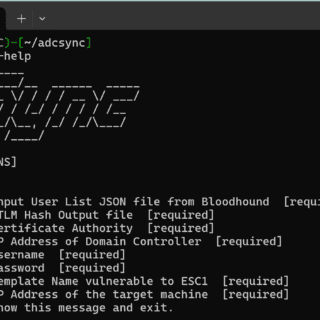
ADCSync ADCSync uses the ESC1 exploit to dump NTLM hashes from user accounts in an Active Directory environment. The tool will first grab every user and domain in the Bloodhound dump file passed in....
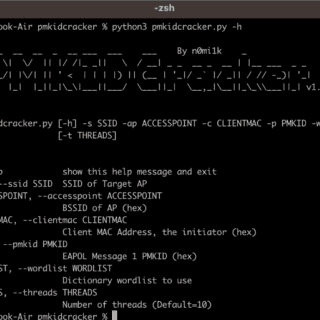
pmkidcracker This program is a tool written in Python to recover the pre-shared key of a WPA2 WiFi network without any de-authentication or requiring any clients to be on the network. It targets the...
EmploLeaks This is a tool designed for Open Source Intelligence (OSINT) purposes, which helps to gather information about employees of a company. 🚀 How it Works The tool starts by searching through LinkedIn to...
legba Legba is a multiprotocol credentials bruteforcer / password sprayer and enumerator built with Rust and the Tokio asynchronous runtime in order to achieve better performances and stability while consuming fewer resources than similar...
unshackle – Password Bypass Tool Unshackle is an open-source tool to bypass Windows and Linux user passwords from a bootable USB based on Linux. Feature Easy to use Support Windows Simple CLI Support Linux To...