Category: Post Exploitation
OneLogicalMyth_Shell This HTA shell was created to assist in breakout assessments. Features File Explorer List Drives – Lists all local drives on the host. You can then click a drive letter to start navigating...
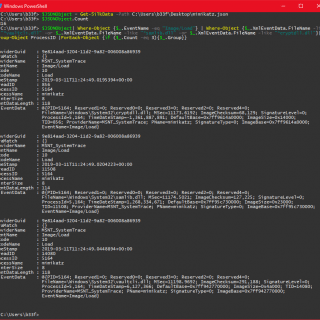
Cypheroth An automated, extensible toolset that runs cipher queries against Bloodhound’s Neo4j backend and saves the output to csv. The list of cipher queries to run is fully extensible. The formatting example below shows...
acCOMplice Your COM hijacking accomplice This repository contains code samples and proofs-of-concept for exploring COM hijacking. COM hijacking is a Windows post-exploitation technique, which can be used for persistence or defense evasion. For more...
KatzKatz KatzKatz is a python tool to parse text files containing output from Mimikatz sekurlsa::logonpasswords module. When performing an internal network pentest sometimes you found yourself gathering many lsass.exe process dumps, open them using...
Pivoting into VPC networks This tool automates the creation of a VPN between the attacker’s workstation and an AWS resource in the target VPC with the objective of connecting to other AWS services, such...
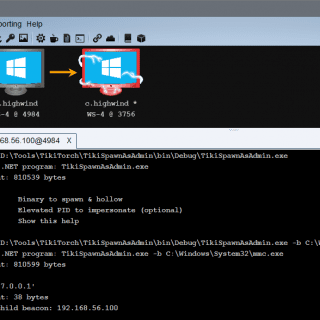
TikiTorch was named in homage to CACTUSTORCH by Vincent Yiu. The basic concept of CACTUSTORCH is that it spawns a new process, then uses CreateRemoteThread to run the desired shellcode within that target process. Both the process and...
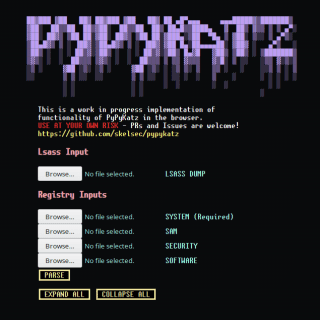
pypykatz_wasm The pypykatz project’s LSASS and Registry HIVE parsing capability is now in your web browser! How does it work There is an awesome project called pyodide which aims to have a fully working python3 interpreter...
Orc is a simple post-exploitation for Linux written in bash It takes the form of an ENV script, so load orc into a shell by running ENV=o.rc sh -i (it does need an interactive...
Azure AD Connect password extraction This toolkit offers several ways to extract and decrypt stored Azure AD and Active Directory credentials from Azure AD Connect servers. These credentials have high privileges in both the...
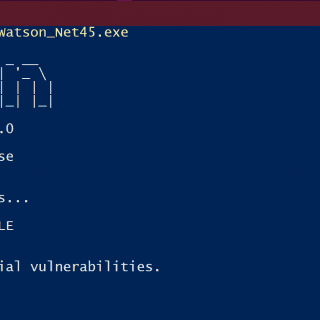
Watson Watson is a .NET tool designed to enumerate missing KBs and suggest exploits for useful Privilege Escalation vulnerabilities. My focus is on the latest priv esc’s for the mainstream Operating Systems, to help...
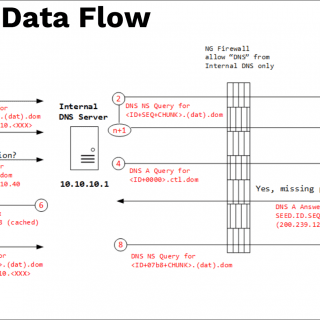
DNS File EXfiltration Data exfiltration is a common technique used for post-exploitation, DNS is one of the most common protocols through firewalls. We take the opportunity to build a unique protocol for transferring files...
PostShell PostShell is a post-exploitation shell that includes both a bind and a back connect shell. It creates a fully interactive TTY which allows for job control. The stub size is around 14kb and...
CIRCO Cisco Implant Raspberry Controlled Operations Designed under Raspberry Pi and aimed for Red Team Ops, we take advantage of “Sec/Net/Dev/Ops” enterprise tools to capture network credentials in a stealth mode. Using low profile...
Juicy Potato (abusing the golden privileges) A sugared version of RottenPotatoNG, with a bit of juice, i.e. another Local Privilege Escalation tool, from a Windows Service Accounts to NT AUTHORITY\SYSTEM JuicyPotato allows you to: Target CLSID...
RACE RACE is a PowerShell module for executing ACL attacks against Windows targets and Active Directory. RACE can be used for persistence and on-demand privilege escalation on Windows machines. Functions Set-RemotePSRemoting Use this function...