Category: Post Exploitation
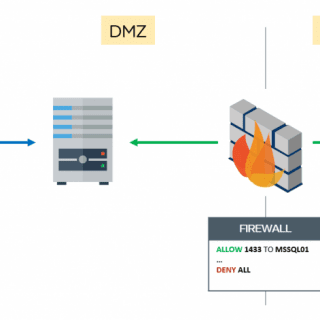
mssqlproxy mssqlproxy is a toolkit aimed to perform a lateral movement in restricted environments through a compromised Microsoft SQL Server via socket reuse. The client requires impacket and sysadmin privileges on the SQL server. Please read this article carefully before...
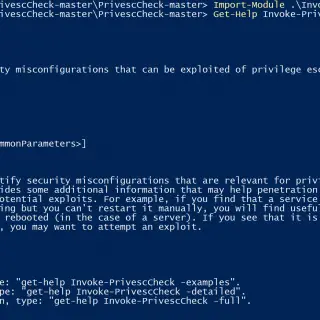
PrivescCheck – Privilege Escalation Enumeration Script for Windows This script aims to enumerate common Windows security misconfigurations which can be leveraged for privilege escalation and gather various information that might be useful for exploitation and/or post-exploitation. Features Current User Invoke-UserCheck...
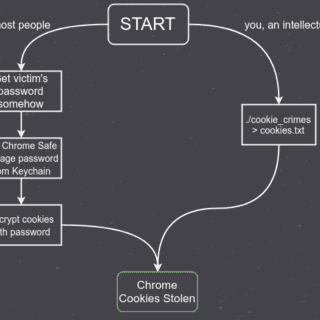
cookie_crimes – Chrome Cookie Extraction Without Root This will print out a user’s Chrome cookies. You don’t need to have their password or be root to use it. nice nice nice nice nice. If...
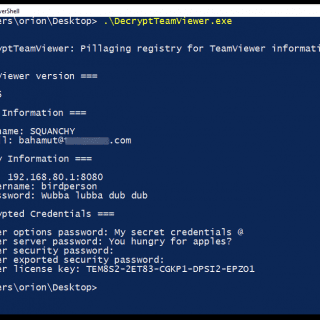
Decrypt TeamViewer Enumerate and decrypt TeamViewer settings from the registry. It’s a little C# tool that uses @Blurbdust‘s kickass work (CVE-2019-18988) to enumerate and decrypt TeamViewer credentials from the Windows registry. Tested on Windows...
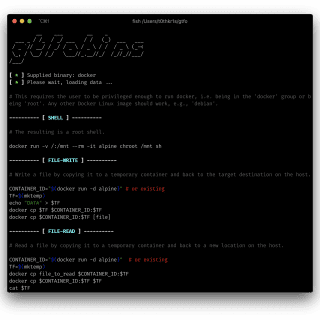
gtfo This is a standalone script written in Python 3 for GTFOBins. You can search for Unix binaries that can be exploited to bypass system security restrictions. These binaries can be abused to break out...
Invoke-CleverSpray Password Spraying Script detecting current and previous passwords of Active Directory User by @flelievre Behavior: Retrieves default or specified domain (to specify a domain, use the -Domain parameter) using Get-NetDomain from PowerView (@harmj0y) and...
What is it for? Grouper2 is a tool for pentesters to help find security-related misconfigurations in Active Directory Group Policy. It might also be useful for other people doing other stuff, but it is explicitly NOT...
lsassy Python library to remotely extract credentials. This library uses impacket projects to remotely read necessary bytes in lsass dump and pypykatz to extract credentials. Changelog v3.1.7 Fix table output Compatible with python < 3.11 Handle –no-color parameter Install python3...
harpoon A collection post-exploitation scripts for determining if that shell you just got is in a container, what kind, and ways to escape. Download go get github.com/ProfessionallyEvil/harpoon Use Options: -c, –check_for_docker_sock try and find...
Stowaway Stowaway is a Multi-hop proxy tool for security researchers and pentesters Users can easily proxy their network traffic to intranet nodes (multi-layer) PS: The files under the demo folder are Stowaway’s beta version,...
BetterBackdoor A backdoor is a tool used to gain remote access to a machine. Typically, backdoor utilities such as NetCat have 2 main functions: to pipe remote input into cmd or bash and output...
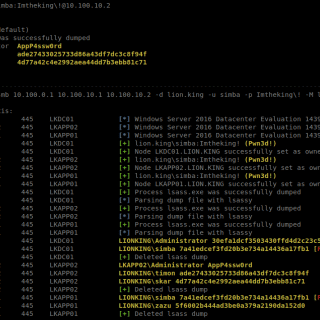
Spraykatz is a tool without any pretension able to retrieve credentials on Windows machines and large Active Directory environments. It simply tries to procdump machines and parses dumps locally in order to avoid detections by antivirus software as much as...
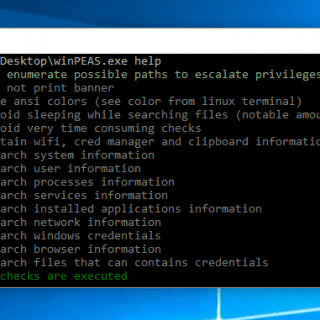
Here you will find privilege escalation tools for Windows and Linux/Unix* (in some near future also for Mac). These tools search for possible local privilege escalation paths that you could exploit and print them to you with nice colors so...
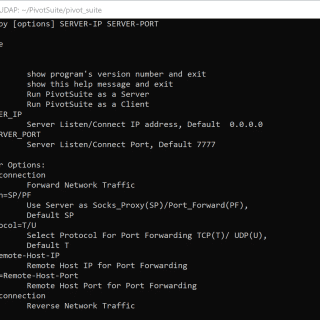
PivotSuite PivotSuite: Hack The Hidden Network – A Network Pivoting Toolkit It is a portable, platform-independent and powerful network pivoting toolkit, Which helps Red Teamers / Penetration Testers to use a compromised system to...
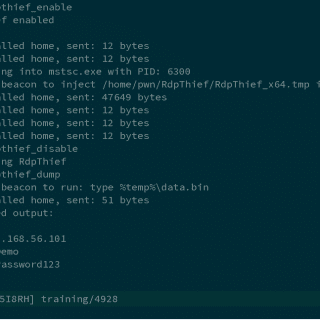
RdpThief RdpThief by itself is a standalone DLL that when injected in the mstsc.exe process, will perform API hooking, extract the clear-text credentials and save them to a file. An aggressor script accompanies it,...