Category: Penetration Testing
cypherhound A Python3 terminal application that contains 260+ Neo4j cyphers for BloodHound data sets. Why? BloodHound is a staple tool for every red teamer. However, there are some negative side effects based on its...
Patchy Automated lateral movement and persistence by abusing GCP OS patch management based on my blog post. OS patch management is a service provided by Google Cloud Platform (GCP) to enable users...
SilentHound Quietly enumerate an Active Directory Domain via LDAP parsing users, admins, groups, etc. Created by Nick Swink from Layer 8 Security. A lightweight tool to quickly and quietly enumerate an Active Directory...
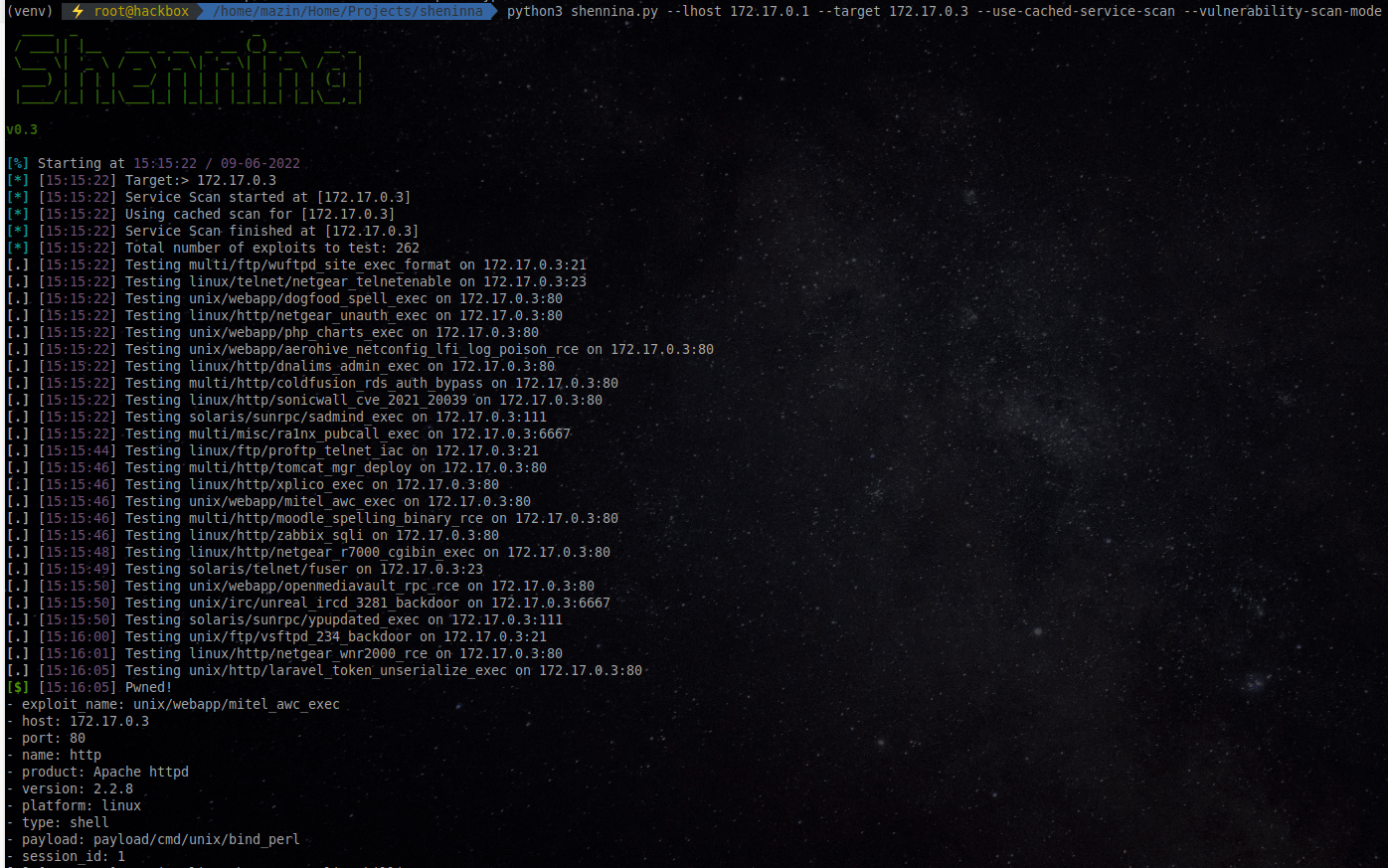
shennina Shennina is an automated host exploitation framework. The mission of the project is to fully automate the scanning, vulnerability scanning/analysis, and exploitation using Artificial Intelligence. Shennina is integrated with...
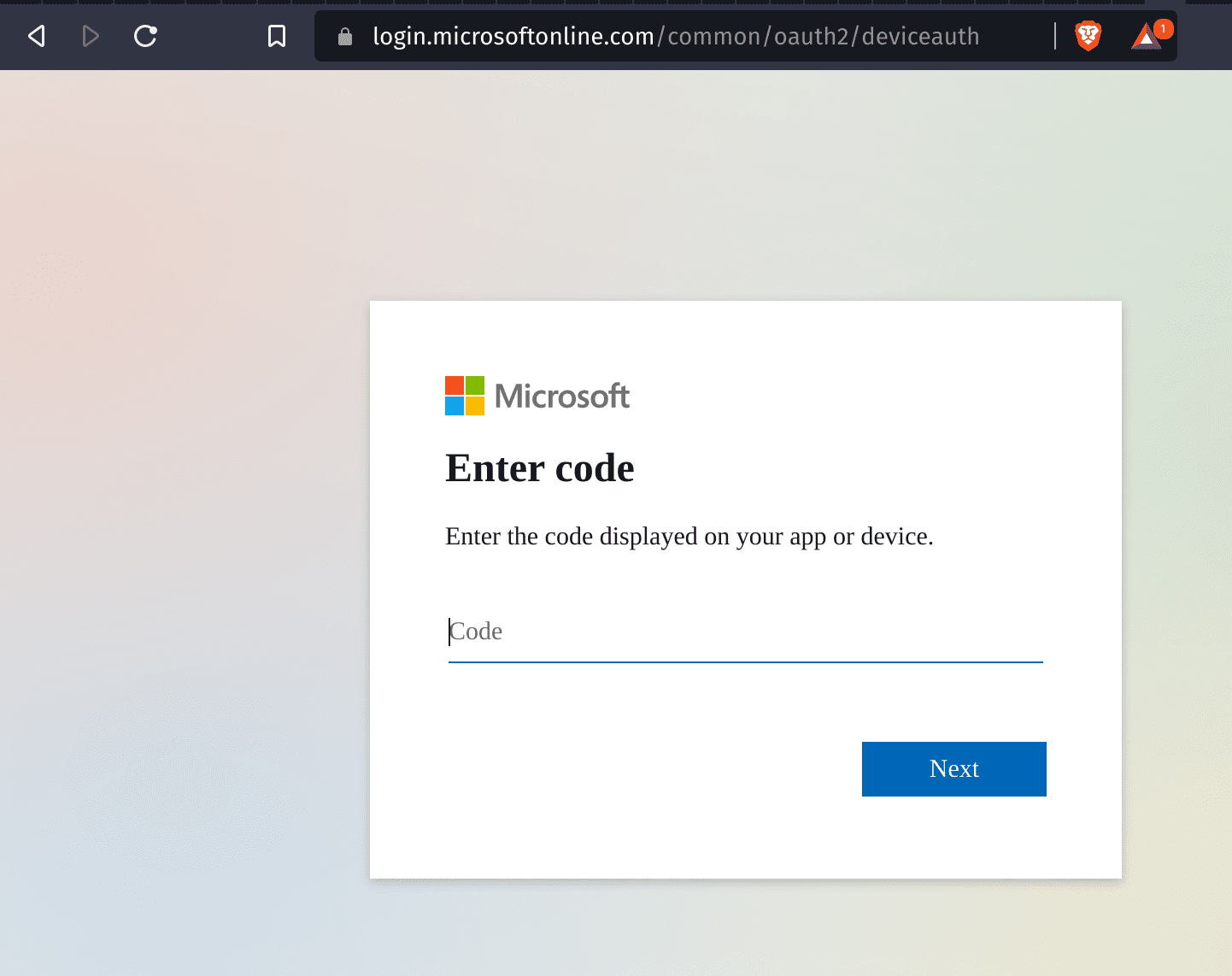
SquarePhish SquarePhish is an advanced phishing tool that uses a technique combining the OAuth Device code authentication flow and QR codes. See PhishInSuits for more details on using OAuth Device Code flow...
AceLdr – Avoid Memory Scanners A position-independent reflective loader for Cobalt Strike. Zero results from Hunt-Sleeping-Beacons, BeaconHunter, BeaconEye, Patriot, Moneta, PE-sieve, or MalMemDetect. Features Easy to Use Import a single CNA script before generating shellcode. Dynamic Memory...
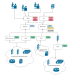
REST-Attacker REST-Attacker is an automated penetration testing framework for APIs following the REST architecture style. The tool’s focus is on streamlining the analysis of generic REST API implementations by completely...
bkcrack Crack legacy zip encryption with Biham and Kocher’s known-plaintext attack. Overview A ZIP archive may contain many entries whose content can be compressed and/or encrypted. In particular, entries can...
TerraLdr: A Payload Loader Designed With Advanced Evasion Features no crt functions imported syscall unhooking using KnownDllUnhook api hashing using Rotr32 hashing algo payload encryption using rc4 – payload is saved...
AV|Ator AV|Ator is a backdoor generator utility, which uses cryptographic and injection techniques in order to bypass AV detection. More specifically: It uses AES encryption in order to encrypt a given...
AzureGoat: A Damn Vulnerable Azure Infrastructure Compromising an organization’s cloud infrastructure is like sitting on a gold mine for attackers. And sometimes, a simple misconfiguration or a vulnerability in web...
DragonCastle A PoC that combines AutodialDLL lateral movement technique and SSP to scrape NTLM hashes from the LSASS process. Description Upload a DLL to the target machine. Then it enables...
Kscan – Simple Asset Mapping Tool kscan is an asset mapping tool that can perform port scanning, TCP fingerprinting, and banner capture for specified assets, and obtain as much port...
AWSGoat: A Damn Vulnerable AWS Infrastructure Compromising an organization’s cloud infrastructure is like sitting on a gold mine for attackers. And sometimes, a simple misconfiguration or a vulnerability in web...
BloodHound Attack Research Kit BARK stands for BloodHound Attack Research Kit. It is a PowerShell script built to assist the BloodHound Enterprise team with researching and continuously validating abuse primitives....