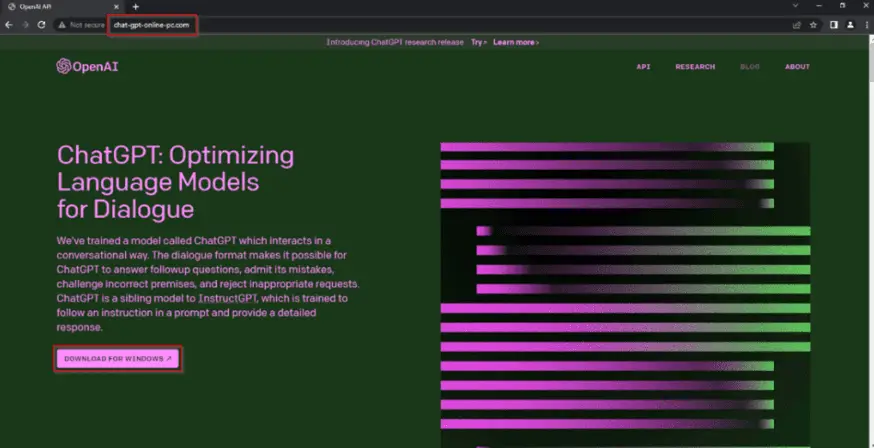
OpenAI Services Hit by Major Outage Due to Telemetry Service Deployment
OpenAI experienced a significant service disruption on December 11, 2024, impacting all its services, including ChatGPT, the API, and Sora. The outage, lasting over four hours, was caused by a...