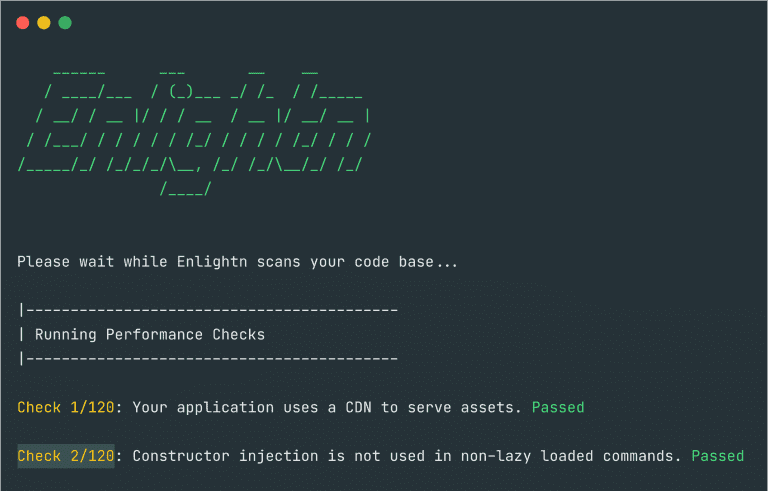
enlightn Think of Enlightn as your performance and security consultant. Enlightn will “review” your code and server...
Defense
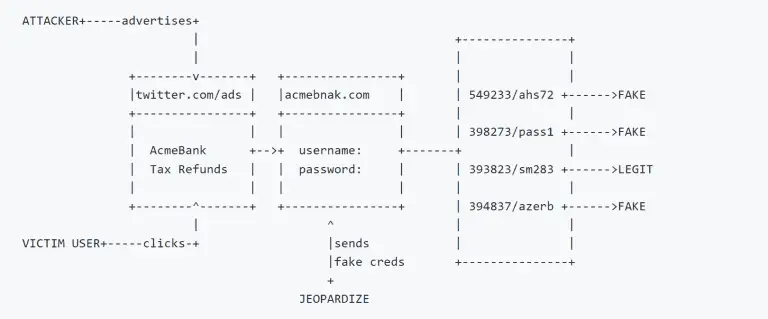
Jeopardize Jeopardize tool is developed to provide basic threat intelligence&response capabilities against phishing domains at the minimum...
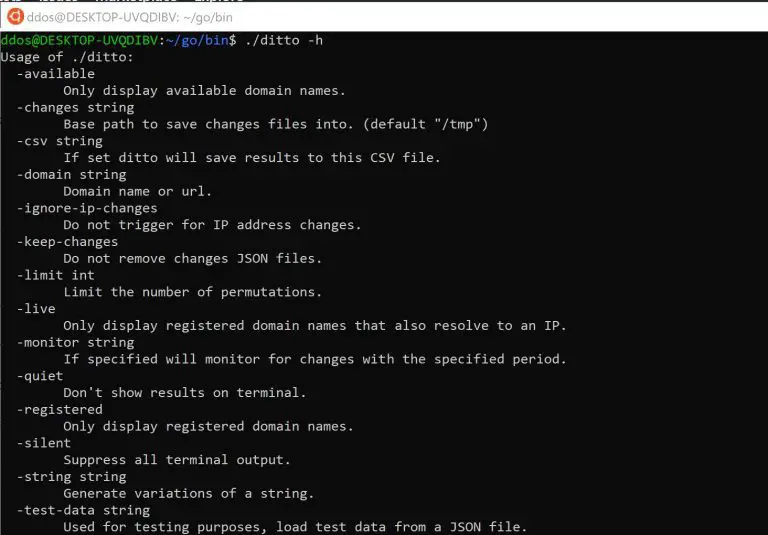
Ditto Ditto is a small tool that accepts a domain name as input and generates all its...
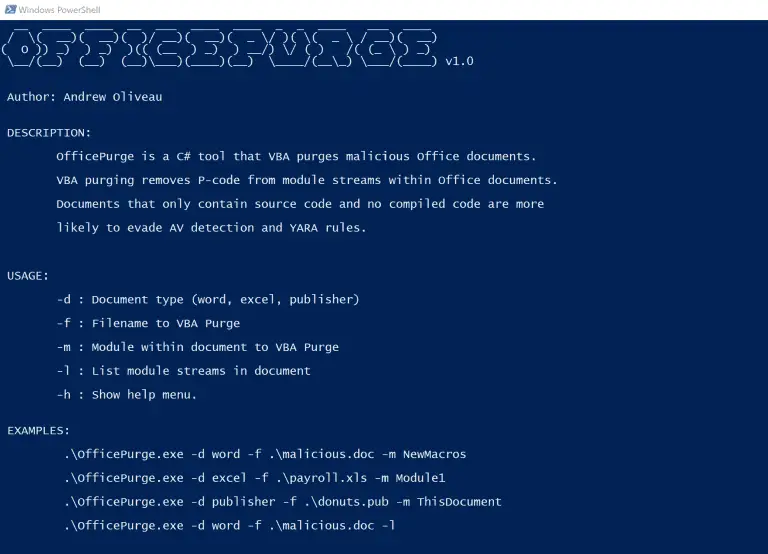
OfficePurge VBA purge your Office documents with OfficePurge. VBA purging removes P-code from module streams within Office...
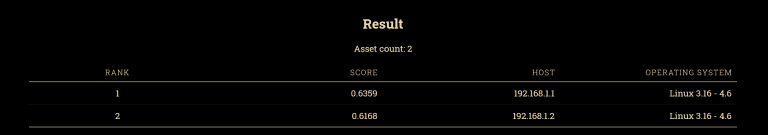
Batea A batea is a large shallow pan of wood or iron traditionally used by gold prospectors...
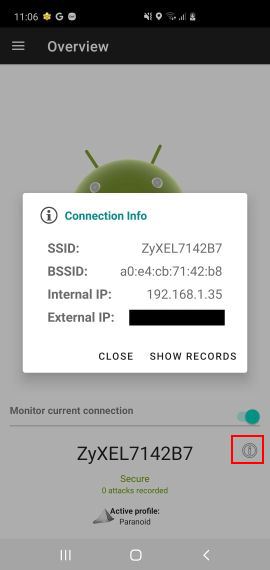
HosTaGe – Honeypot-To-Go HosTaGe is a lightweight, low-interaction, portable, and generic honeypot for mobile devices that aims...
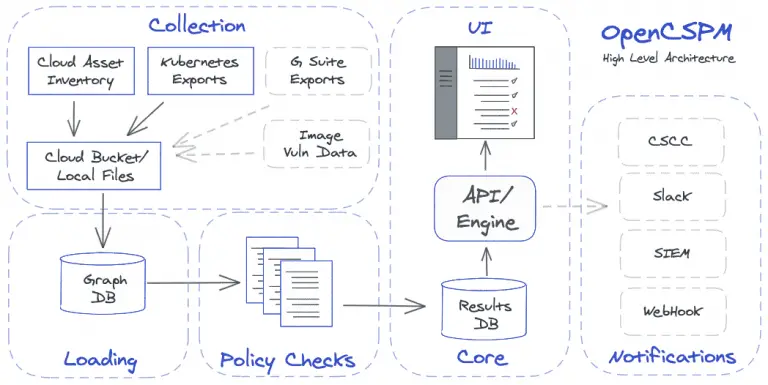
OpenCSPM Open Cloud Security Posture Management, OpenCSPM, is an open-source platform for gaining deeper insight into your...
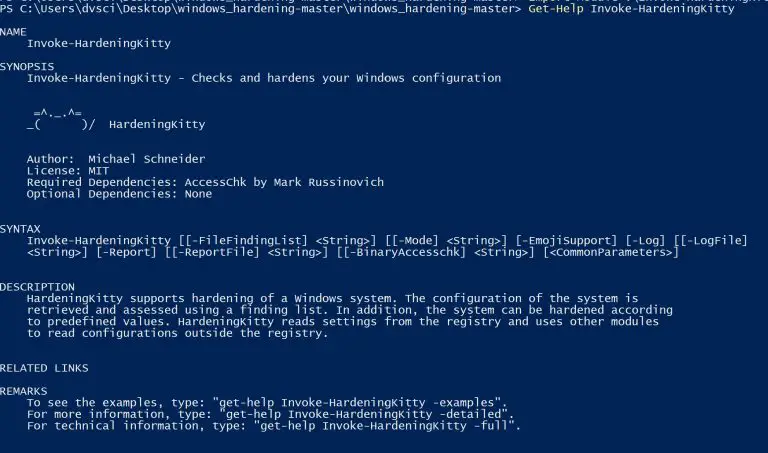
HardeningKitty and Windows 10 Hardening Introduction This is a hardening checklist that can be used in private...
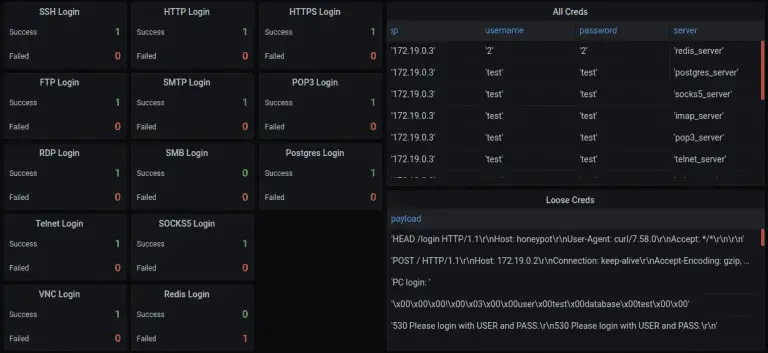
chameleon Customizable honeypots for monitoring network traffic, bots activities, and username\password credentials (DNS, HTTP Proxy, HTTP, HTTPS,...
The Blue Team PowerShell Security Package This repo contains a collection of PowerShell tools that can be...
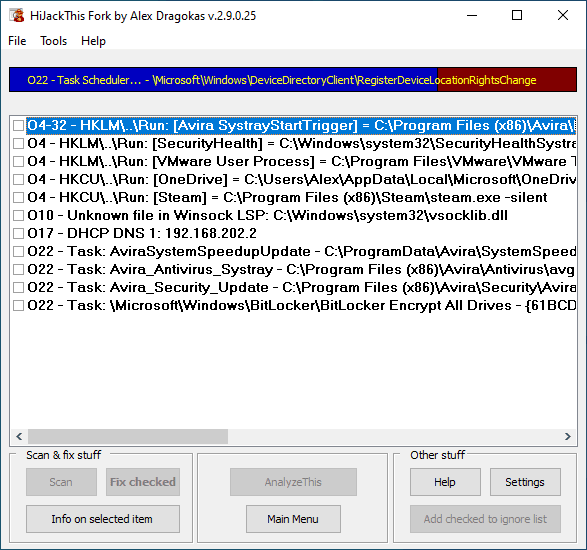
HiJackThis Fork HiJackThis Fork is a free utility for Microsoft Windows that scans your computer for settings...
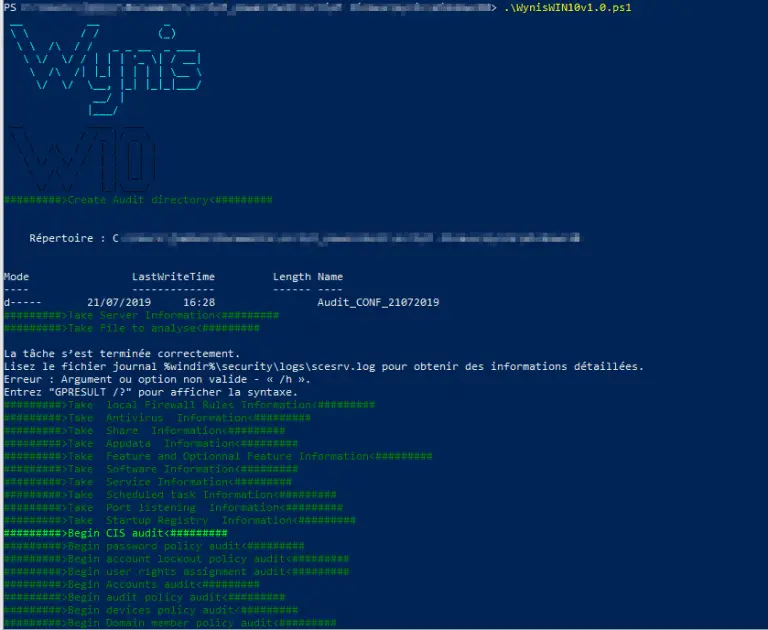
Wynis Just a powershell scripts for auditing security with CIS BEST Practices Windows 10 and Windows Server...
ThreatPursuit-VM Threat Pursuit Virtual Machine (VM): A fully customizable, open-sourced Windows-based distribution focused on threat intelligence analysis...
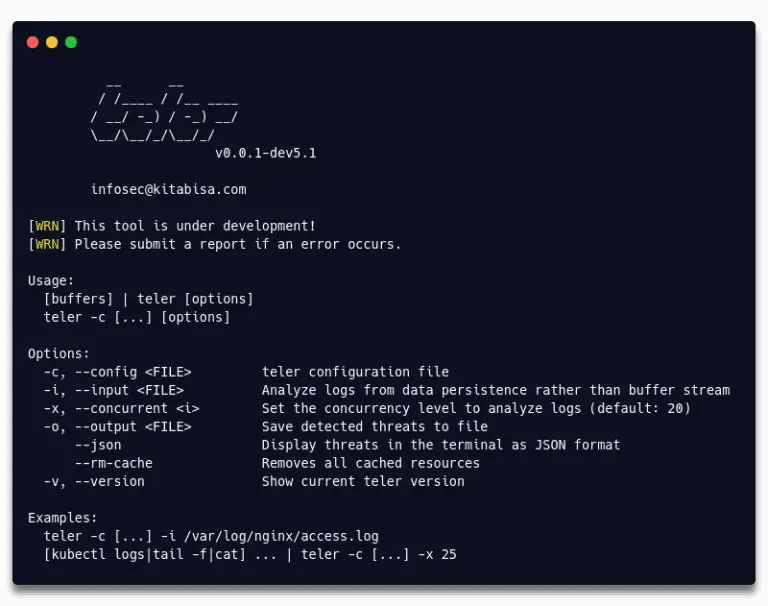
teler teler is a real-time http intrusion detection and threat alert based on a weblog that runs...
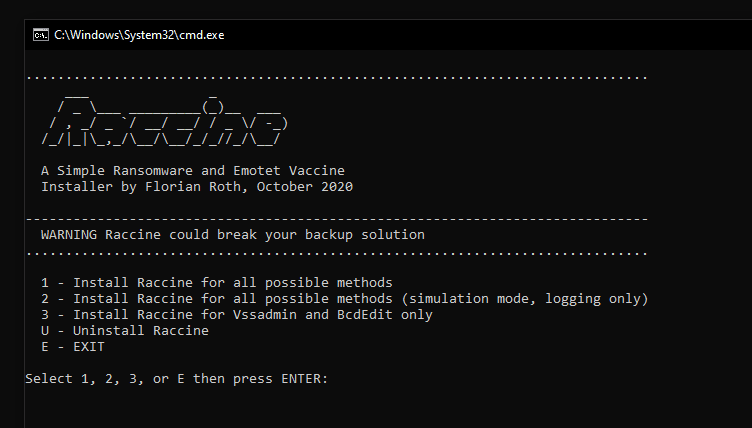
Raccine A Simple Ransomware Protection Why We see ransomware delete all shadow copies using vssadmin pretty often. What...