Category: Malware Analysis
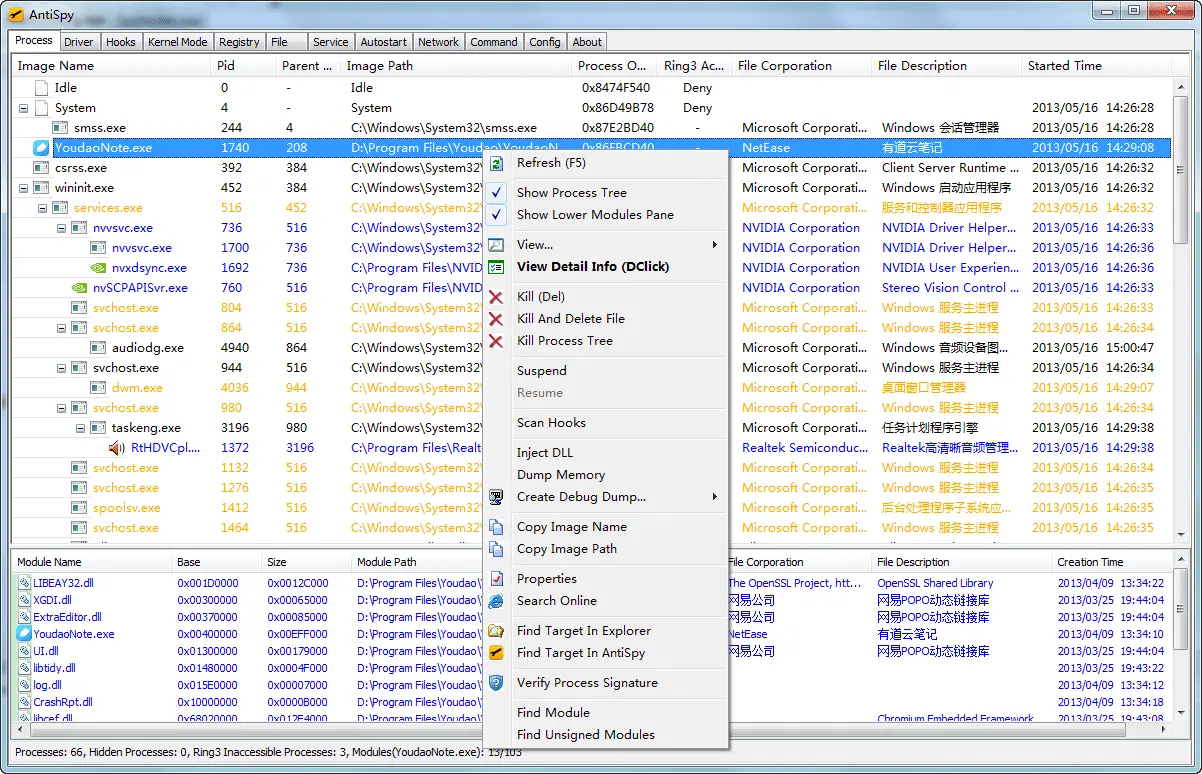
AntiSpy AntiSpy is a free but powerful anti-virus and rootkits toolkit. It offers you the ability with the highest privileges that can detect, analyze and restore various kernel modifications and...
Unprotect Malware for the Mass The Unprotect Project is an Open Source project that aims to propose a classification of Evasion Techniques to help to understand and analyze malware. This...
Mordor Gates The Mordor project provides pre-recorded security events generated by simulated adversarial techniques in the form of JavaScript Object Notation (JSON) files for easy consumption. The pre-recorded data is...
LiSa Project providing automated Linux malware analysis on various CPU architectures. Features QEMU emulation. Currently supporting x86_64, i386, arm, mips, aarch64. Small images built w/ buildroot. Radare2 based static analysis. Dynamic...
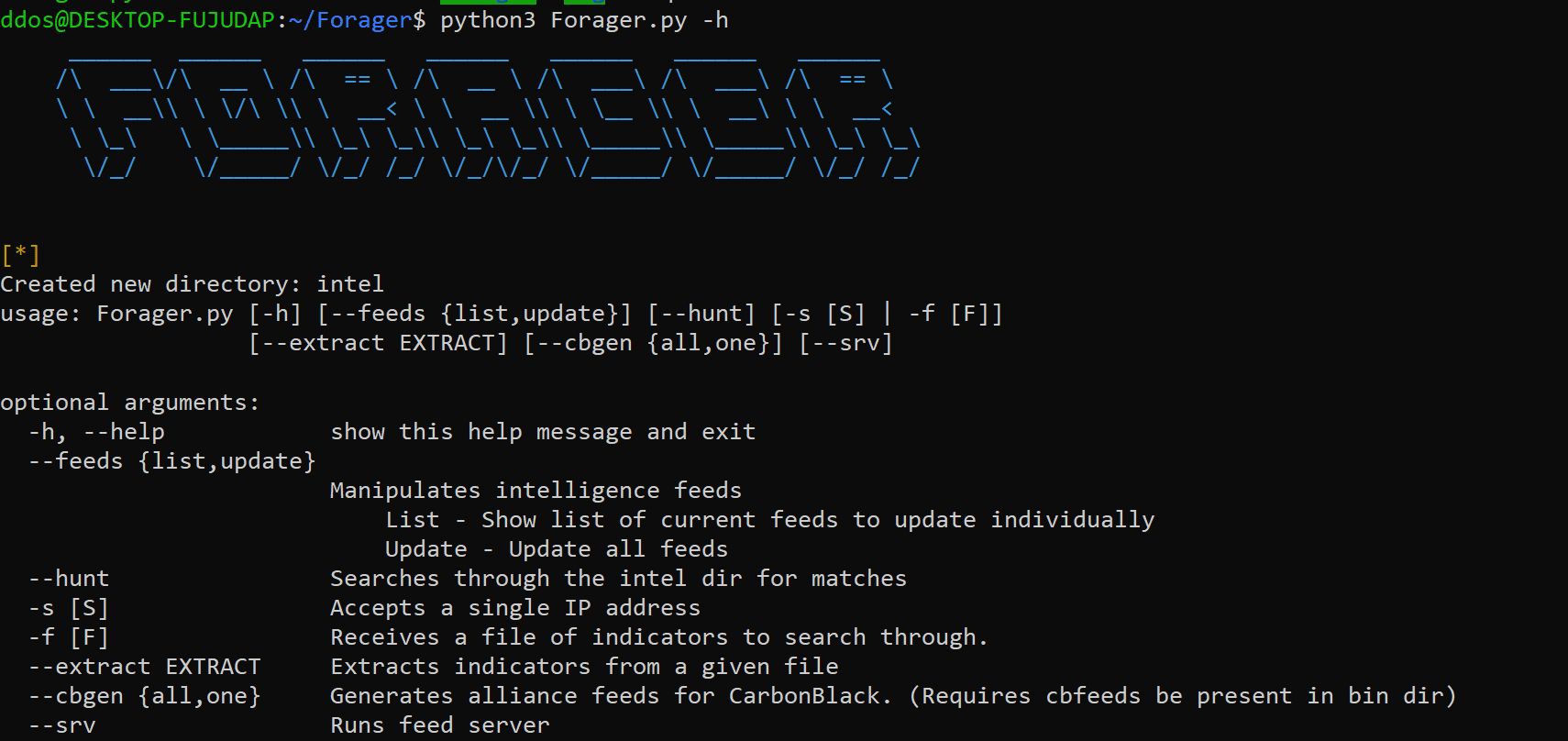
Forager Do you ever wonder if there is an easier way to retrieve, store, and maintain all your threat intelligence data? Random user, meet Forager. Not all threat intel implementations...
Sandboxed Execution Environment Sandboxed Execution Environment (SEE) is a framework for building test automation in secured Environments. The Sandboxes, provided via libvirt, are customizable allowing a high degree of flexibility....
Project Aura: Security audits for packages The current trend in the development is to use a lot of packages in the development phase, even if they provide only trivial functionality...
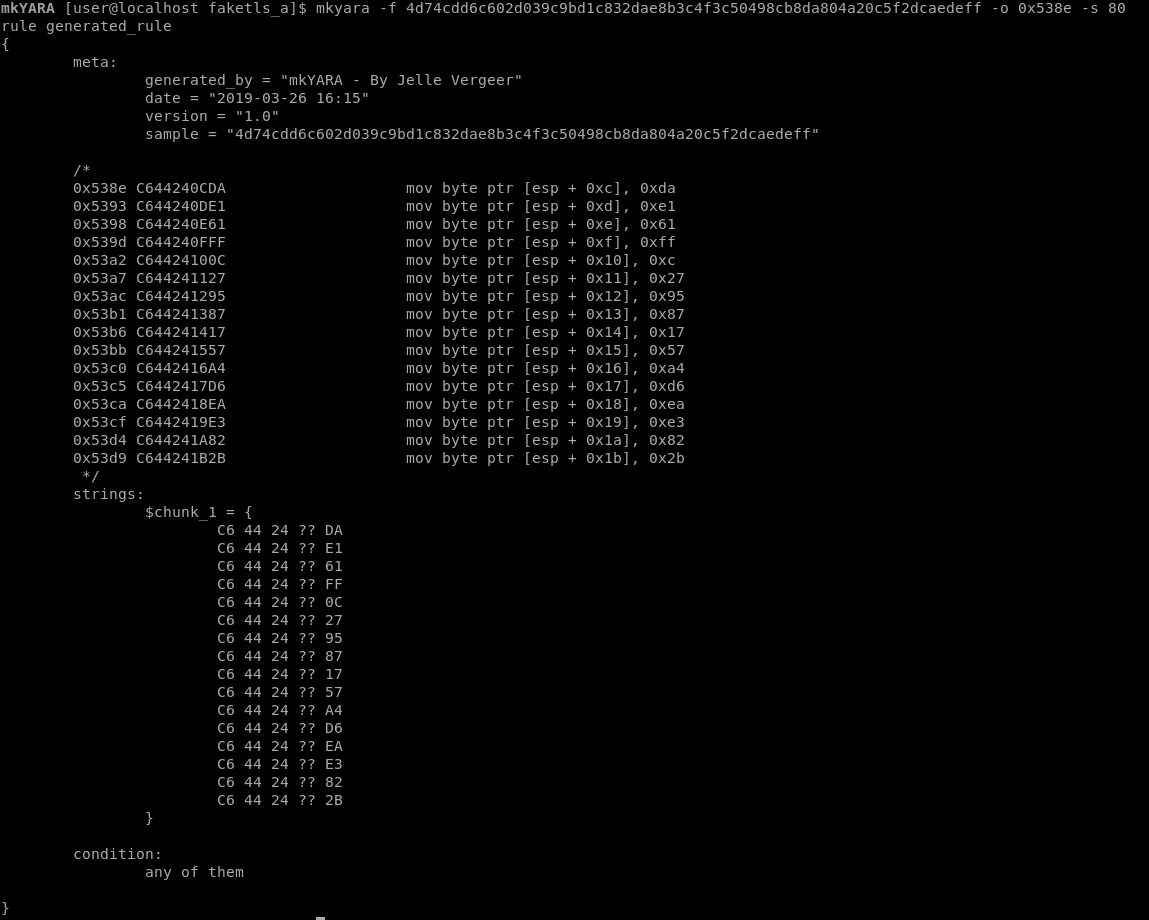
mkYARA Writing YARA rules based on executable code within malware can be a tedious task. An analyst cannot simply copy and paste the raw executable code into a YARA rule,...
flare-emu flare-emu marries IDA Pro’s binary analysis capabilities with Unicorn’s emulation framework to provide the user with an easy to use and flexible interface for scripting emulation tasks. It is designed to handle...
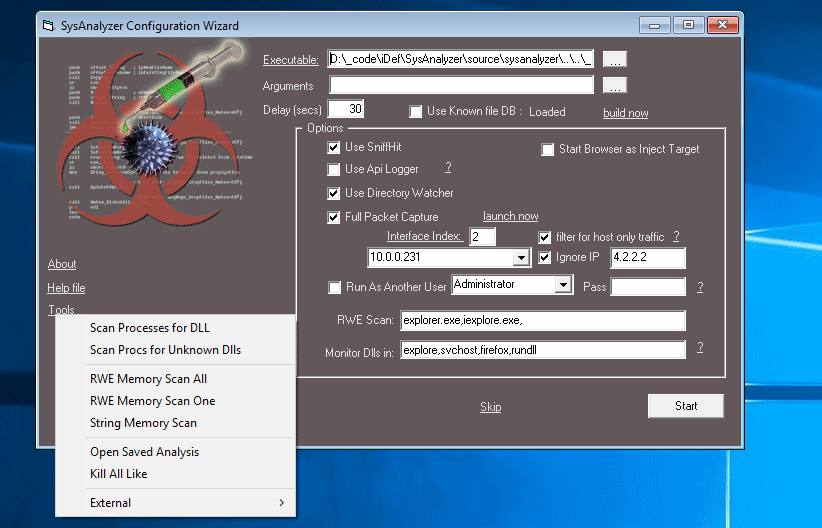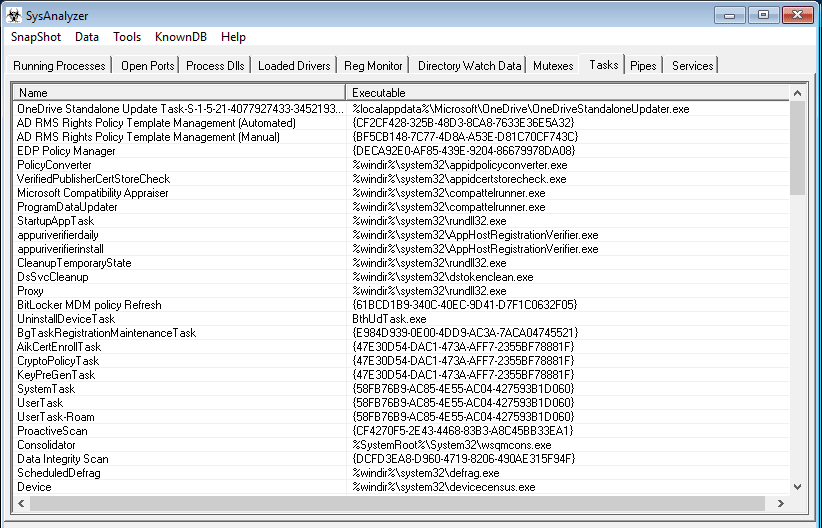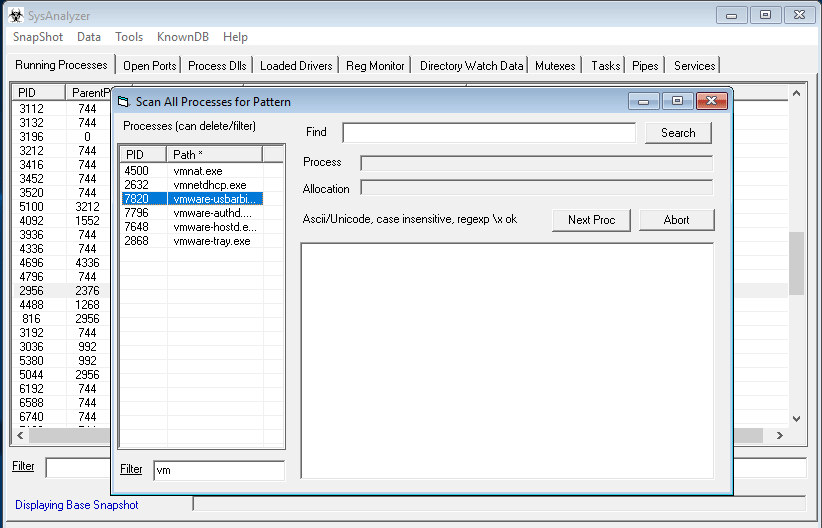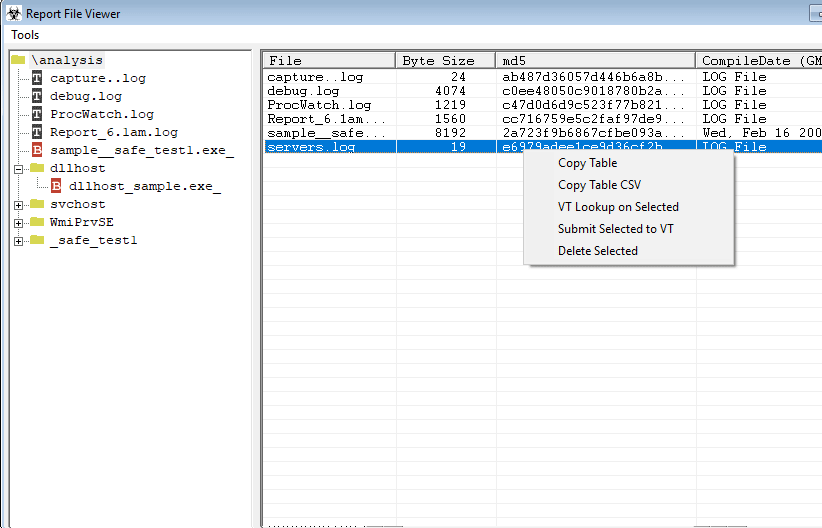
SysAnalyzer is an application that was designed to give malcode analysts an automated tool to quickly collect, compare, and report on the actions a binary took while running on the...
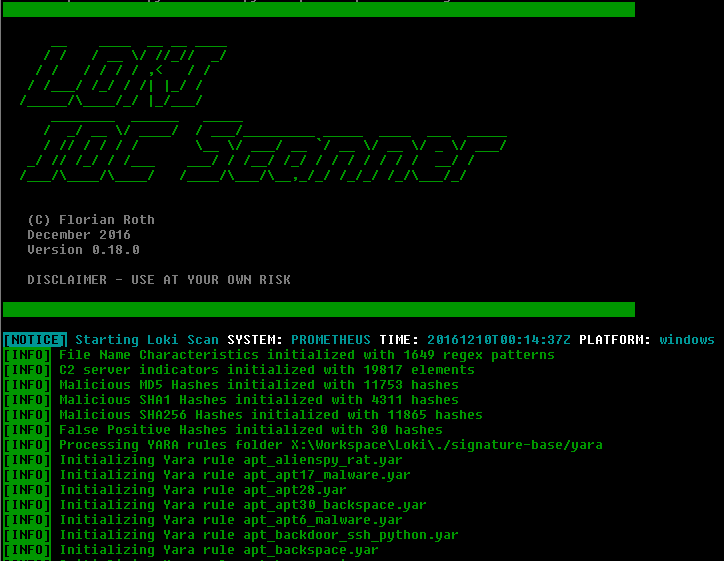
Loki – Simple IOC Scanner Scanner for Simple Indicators of Compromise Detection is based on four detection methods: File Name IOC Regex match on full file path/name Yara Rule Check...
idenLib – Library Function Identification When analyzing malware or 3rd party software, it’s challenging to identify statically linked libraries and to understand what a function from the library is doing....
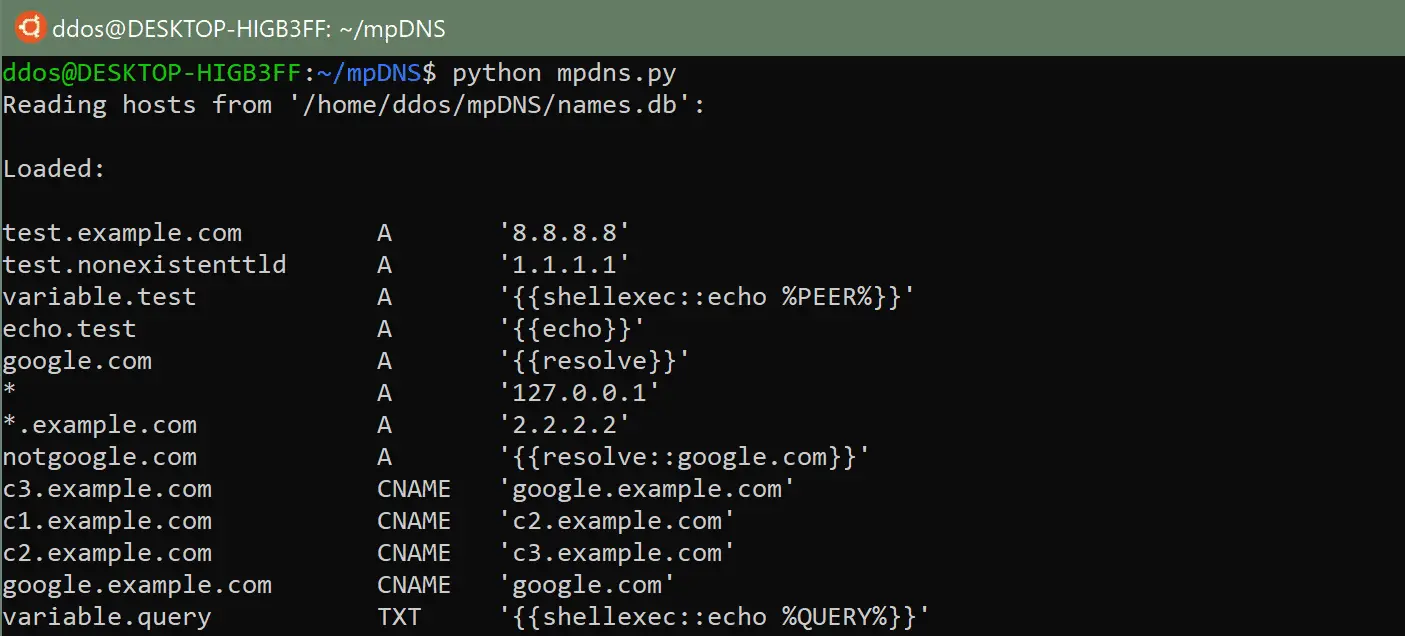
mpDNS aka multi-purpose DNS Server DNS Server with multiple useful features Should work on Python 2 and 3 names.db -> holds all custom records (see examples) Simple wildcards like *.example.com...
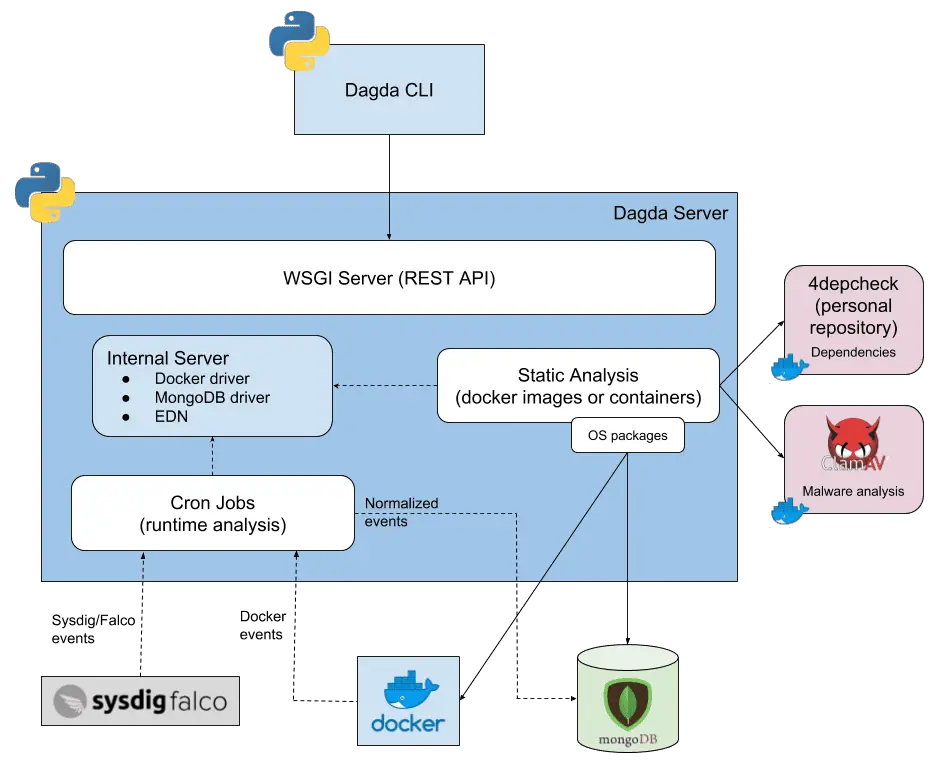
Dagda is a tool to perform static analysis of known vulnerabilities, trojans, viruses, malware & other malicious threats in docker images/containers and to monitor the docker daemon and running Docker containers...
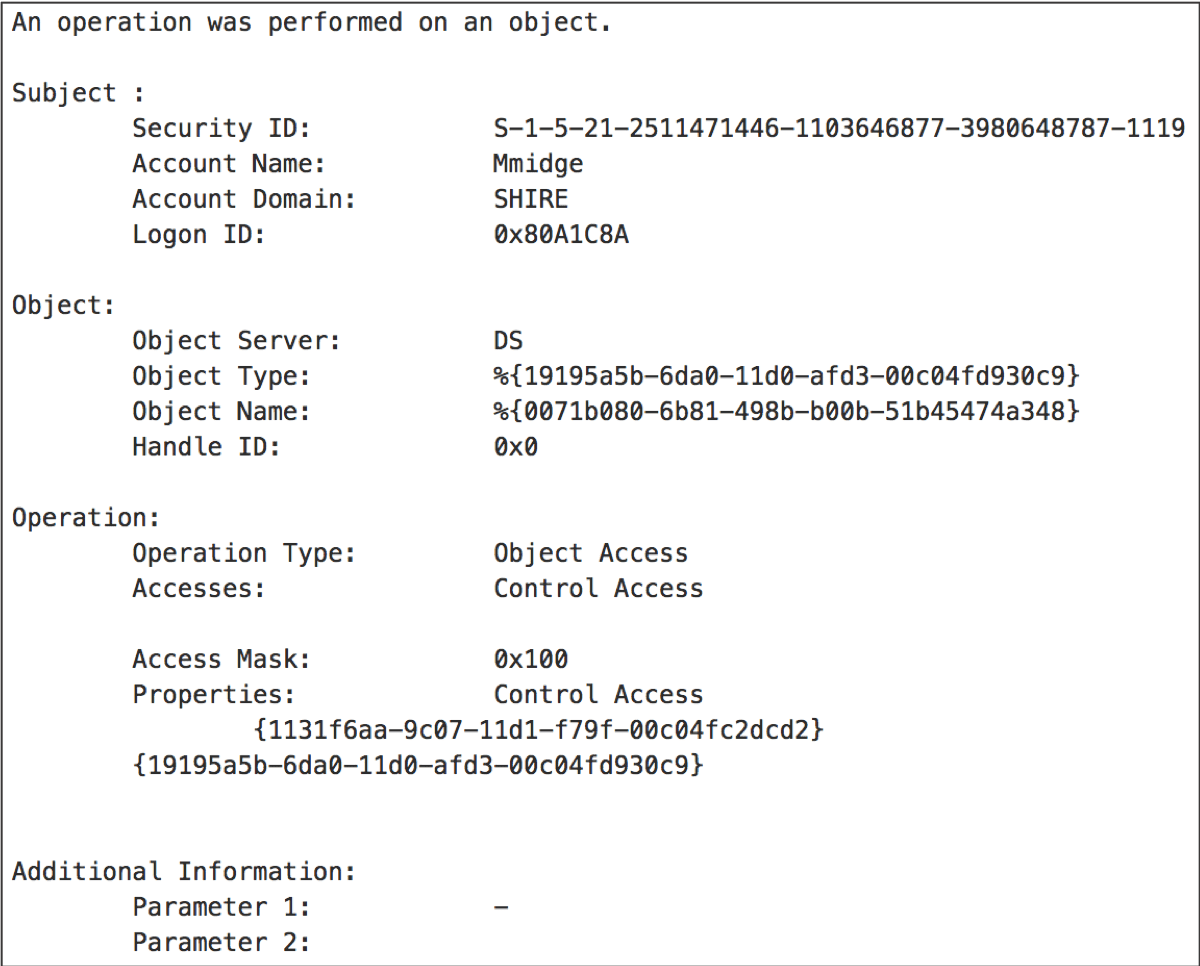
Sigma Generic Signature Format for SIEM Systems What is Sigma? Sigma is a generic and open signature format that allows you to describe relevant log events in a straightforward manner....