Shelter Shelter is a completely weaponized sleep obfuscation technique that allows you to fully encrypt your in-memory...
Network PenTest
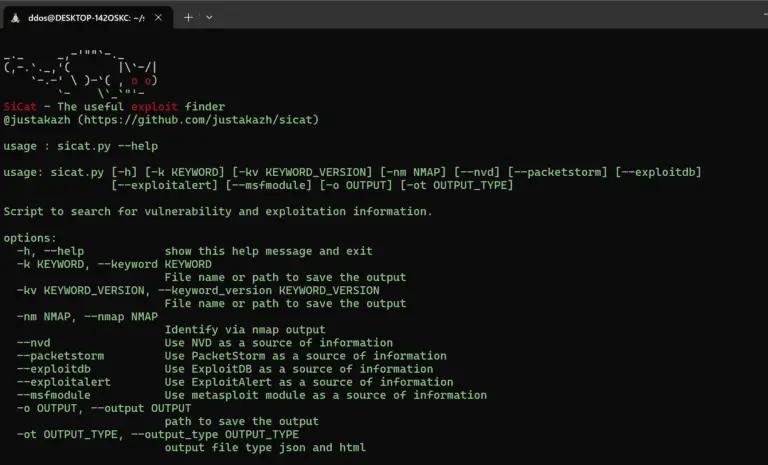
SiCat – The useful exploit finder SiCat is an advanced exploit search tool designed to identify and...
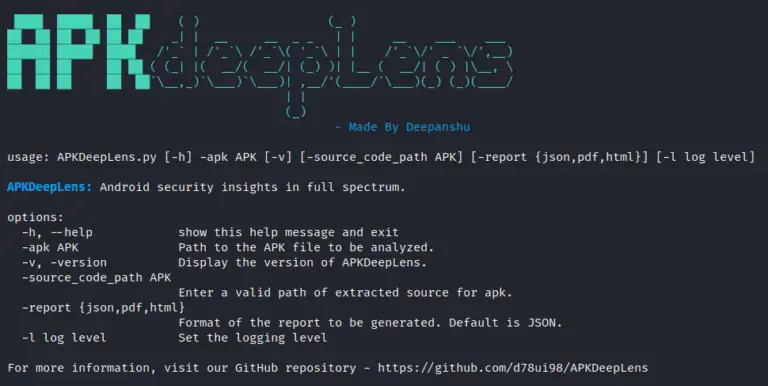
APKDeepLens APKDeepLens is a Python-based tool designed to scan Android applications (APK files) for security vulnerabilities. It...
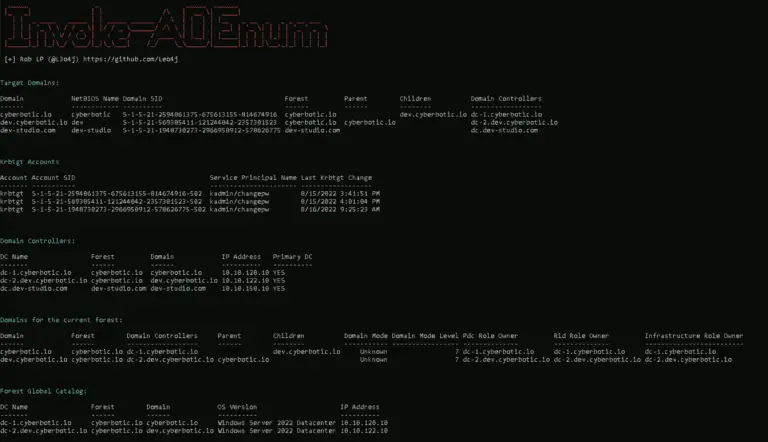
Invoke-ADEnum Active Directory Enumeration Invoke-ADEnum is an Active Directory enumeration tool designed to automate the process of...
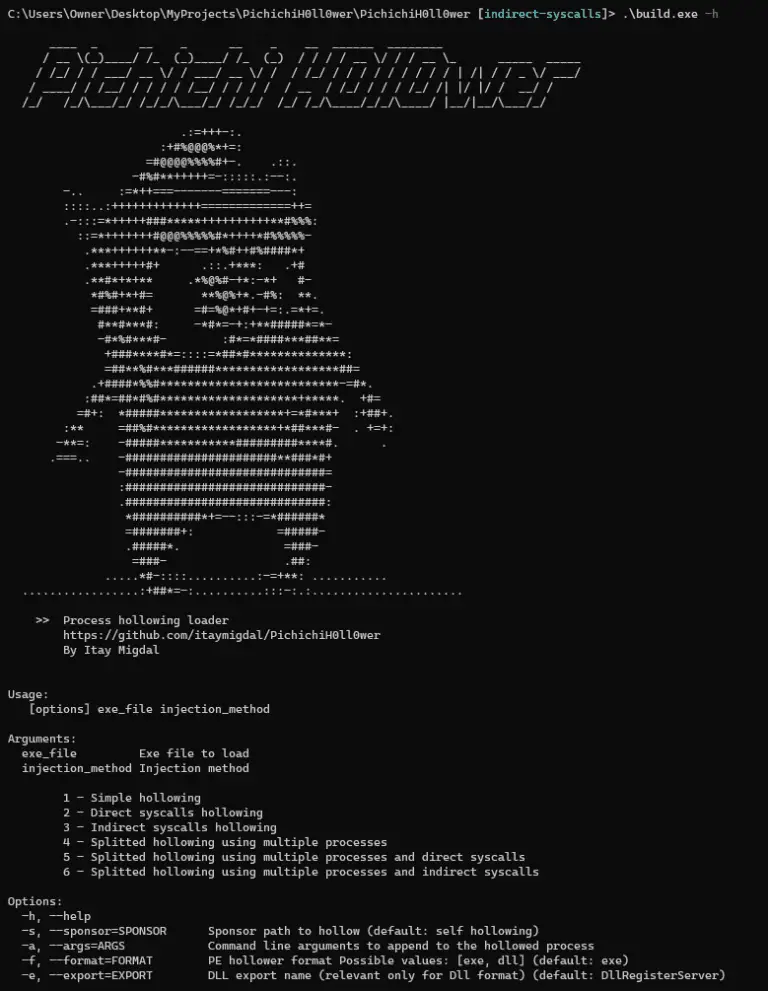
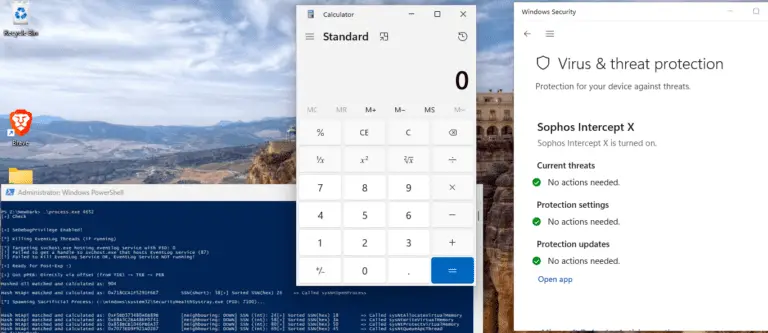
PichichiH0ll0wer Process hollowing loader written in Nim for PEs only PichichiH0ll0wer has some features to protect your...
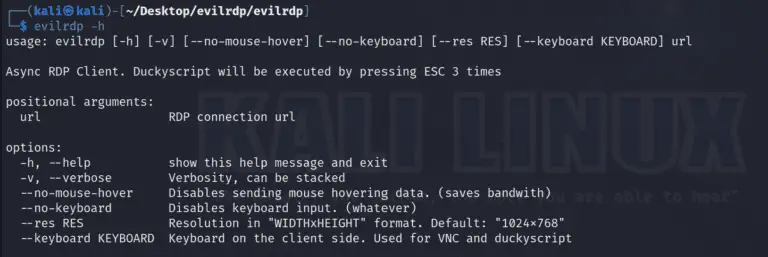
EVILRDP – More control over RDP The evil twin of aardwolfgui using the aardwolf RDP client library that gives you...
DarkWidow This is a Dropper/Post Exploitation Tool (or can be used in both situations) targeting Windows. Capabilities:...
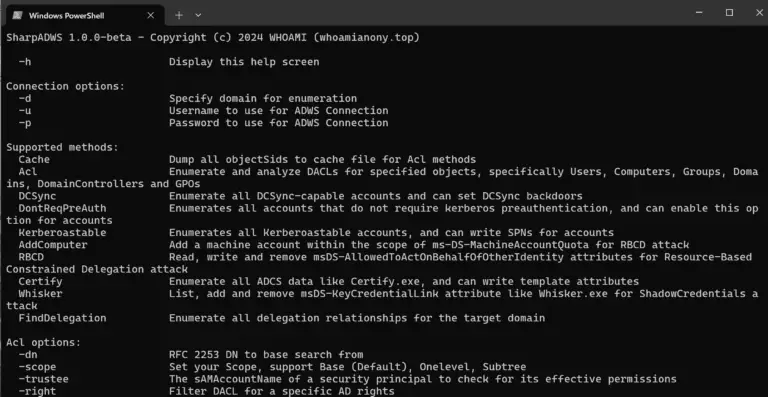
SharpADWS SharpADWS is an Active Directory reconnaissance and exploitation tool for Red Teams that collects and modifies...
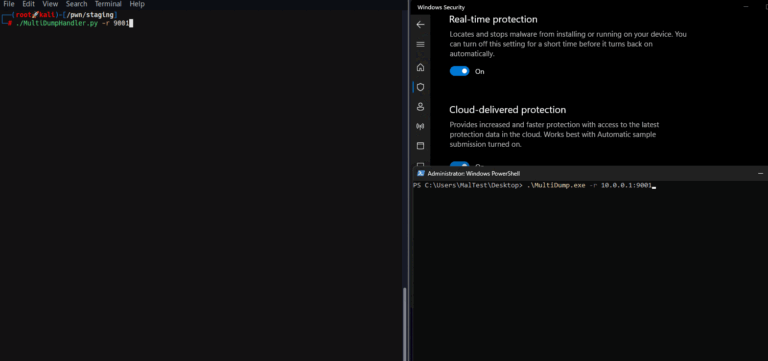
MultiDump MultiDump is a post-exploitation tool written in C for dumping and extracting LSASS memory discreetly, without...
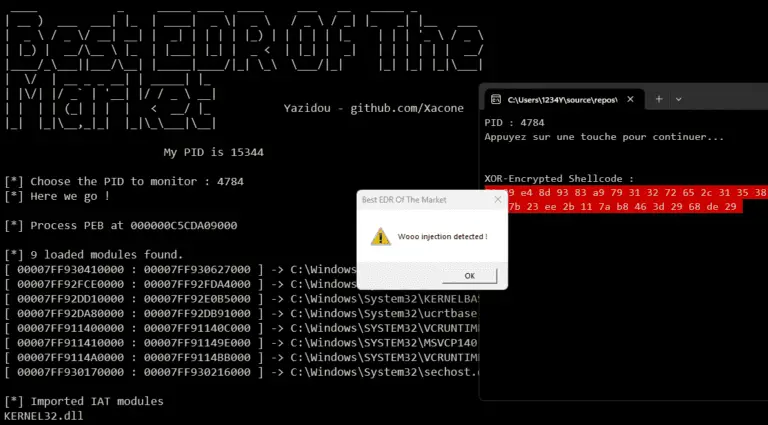
Best EDR Of The Market (BEOTM) BestEDROfTheMarket is a naive user-mode EDR (Endpoint Detection and Response) project,...
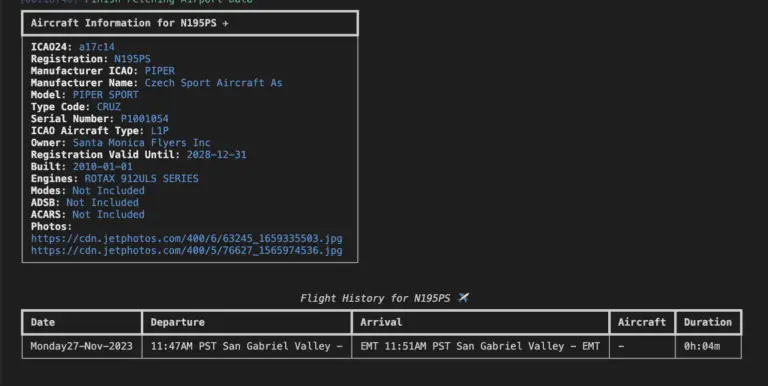
skytrack skytrack is a command-line-based plane spotting and aircraft OSINT reconnaissance tool made using Python. It can...
UAC-BOF-Bonanza This repository serves as a collection of public UAC bypass techniques that have been weaponized as...
CrimsonEDR CrimsonEDR is an open-source project engineered to identify specific malware patterns, offering a tool for honing...
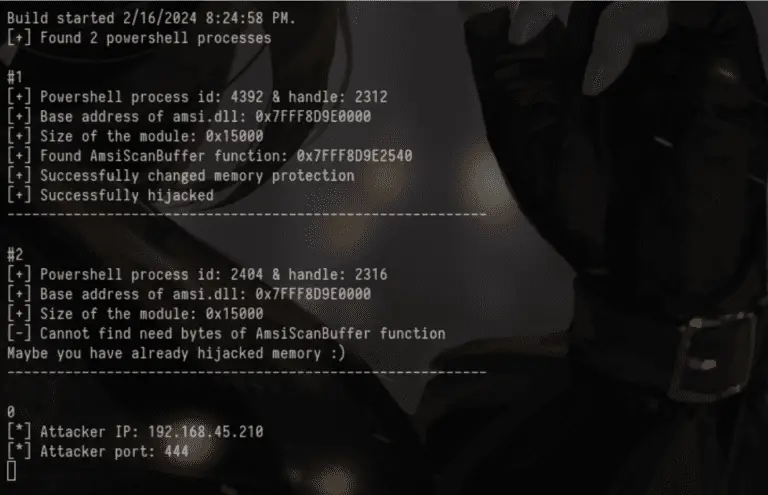
FullBypass A tool that bypasses AMSI (AntiMalware Scan Interface) and PowerShell CLM (Constrained Language Mode) and gives...
InflativeLoading Background Converting an exe to shellcode is one of my goals, in this way, some security...