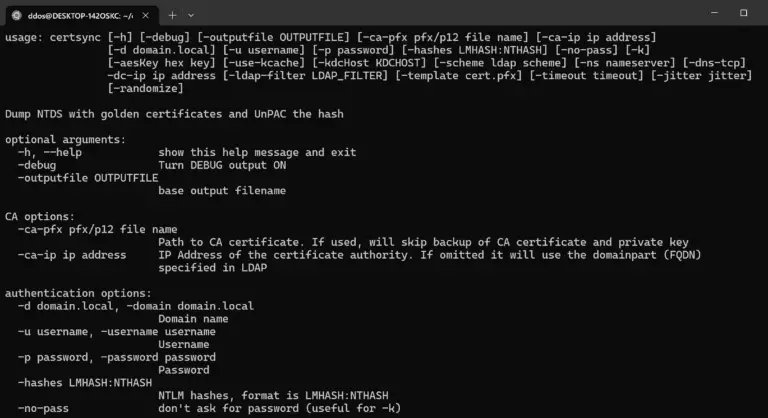
certsync certsync is a new technique in order to dump NTDS remotely, but this time without DRSUAPI:...
Post Exploitation
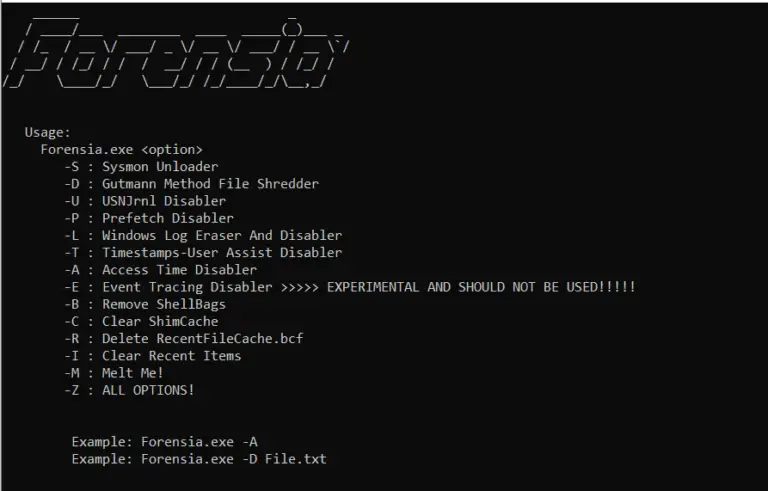
Forensia Anti Forensics Tool For Red Teamers, Used For Erasing Some Footprints In The Post Exploitation Phase....
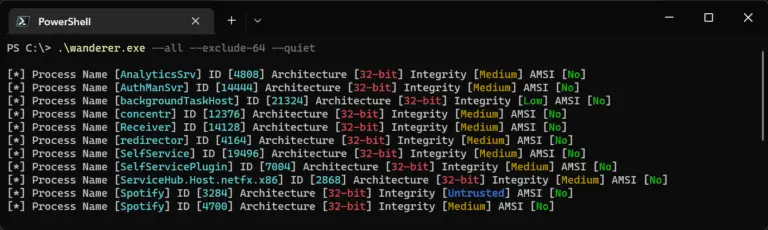
Wanderer Wanderer is an open-source program that collects information about running processes. This information includes the integrity...
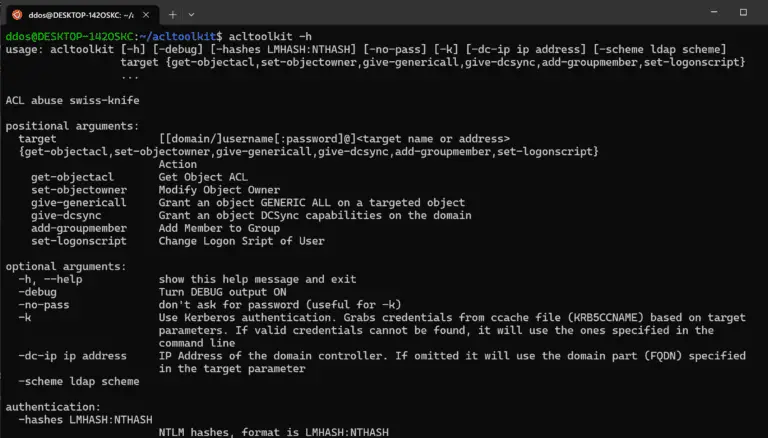
acltoolkit ACL Toolkit is an ACL abuse swiss-knife. Install git clone https://github.com/zblurx/acltoolkit.git cd acltoolkit pip install ....
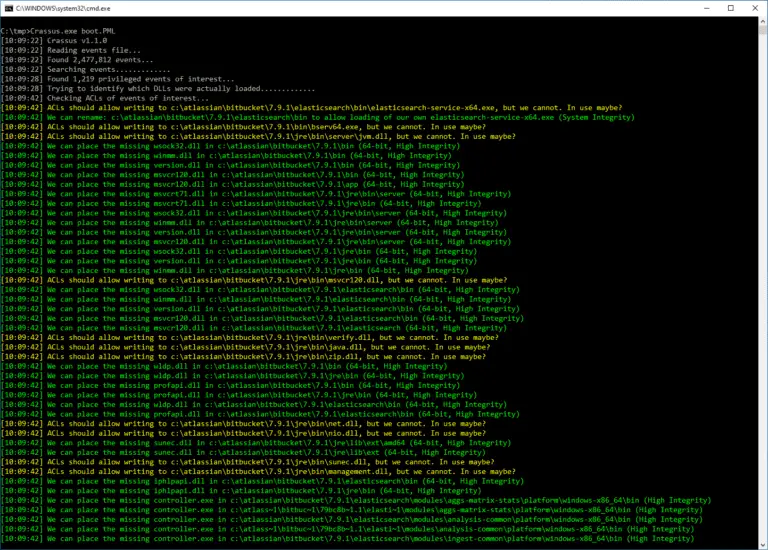
Crassus Windows privilege escalation discovery tool Why “Crassus”? Accenture made a tool called Spartacus, which finds DLL hijacking...
Inline-Execute-PE Inline-Execute-PE is a suite of Beacon Object Files (BOF’s) and an accompanying Aggressor script for CobaltStrike...
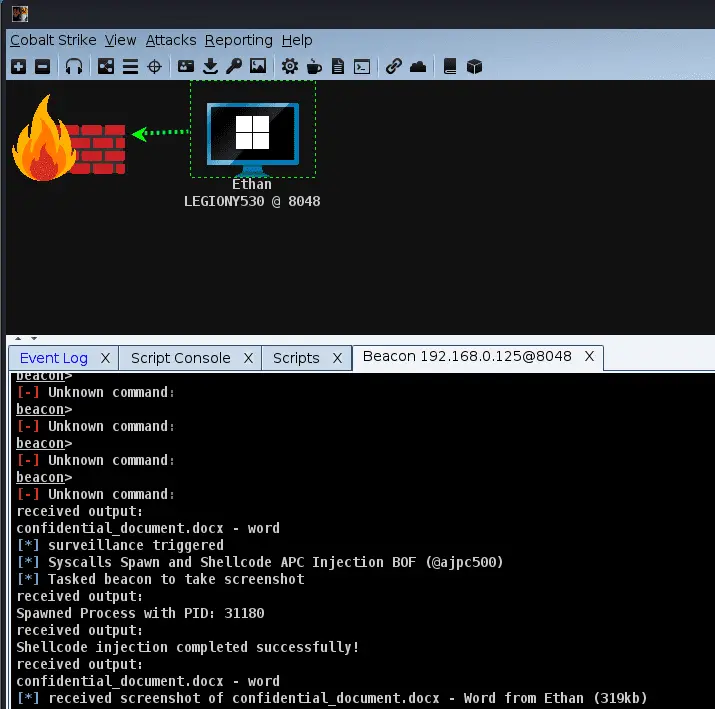
WindowSpy WindowSpy is a Cobalt Strike Beacon Object File meant for targeted user surveillance. The goal of...
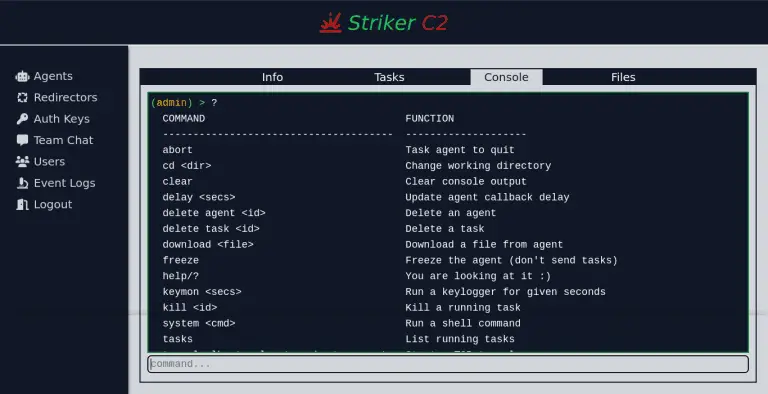
Striker C2 Striker is a simple Command and Control (C2) program. Features A) Agents Native agents for Linux and windows...
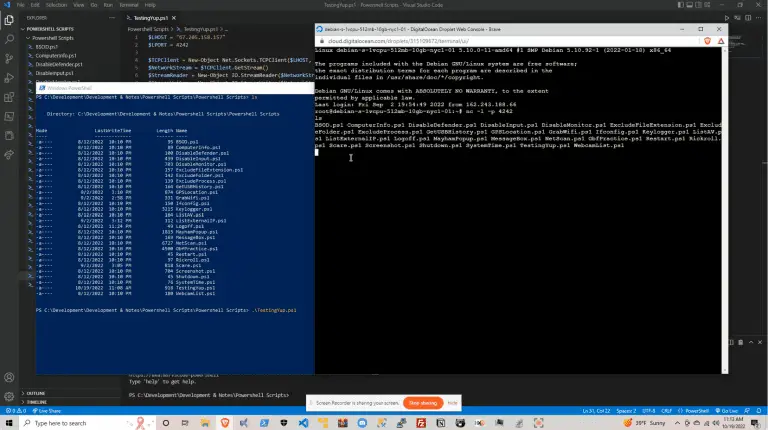
PowerMeUp This is a powershell reverse shell that executes the commands and or scripts that you add...
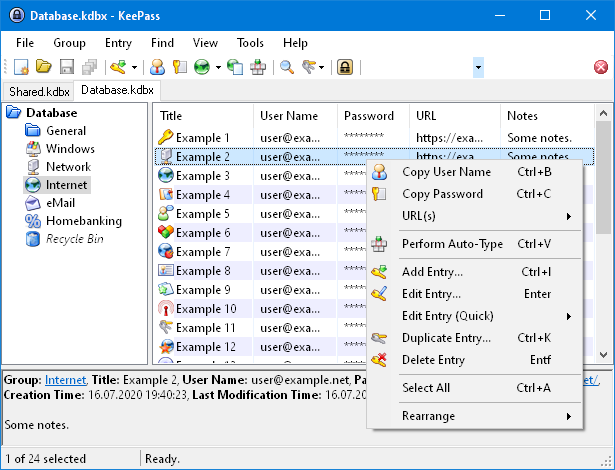
KeeFarce Reborn A standalone DLL that exports databases in cleartext once injected in the KeePass process. Yet...
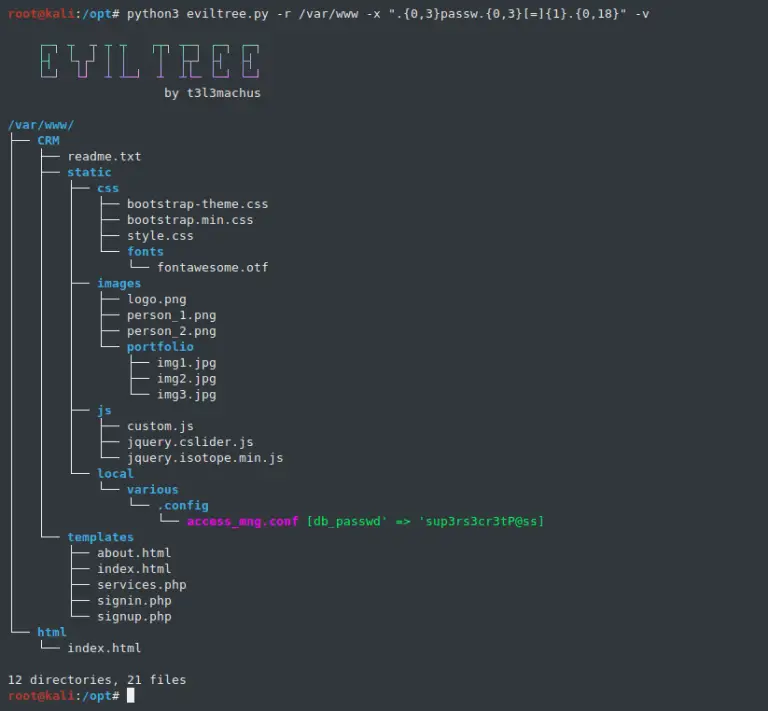
EvilTree A standalone python3 remake of the classic “tree” command with the additional feature of searching for...
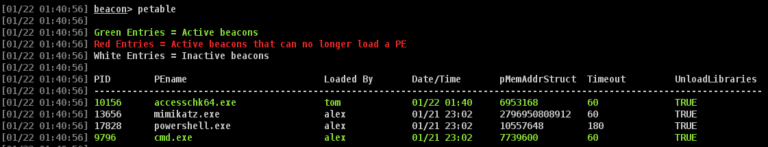
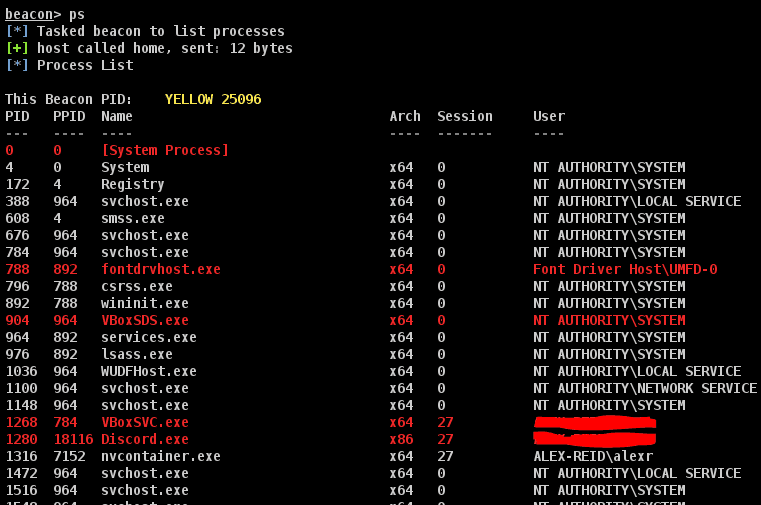
Cohab_Processes This Aggressor script is intended to help internal Red Teams identify suspicious or foreign processes (“Cohabitation”)...
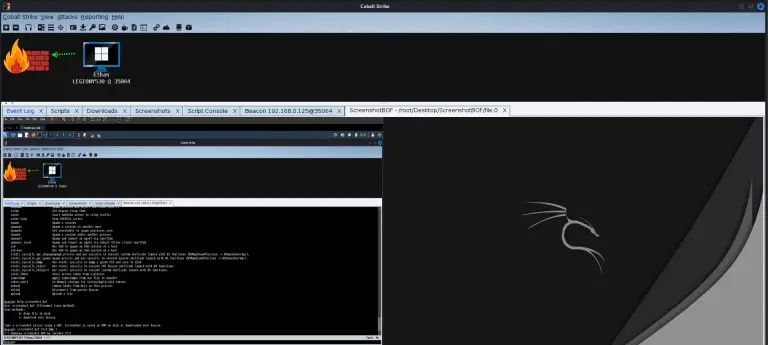
ScreenshotBOF An alternative screenshot capability for Cobalt Strike that uses WinAPI and does not perform a fork...
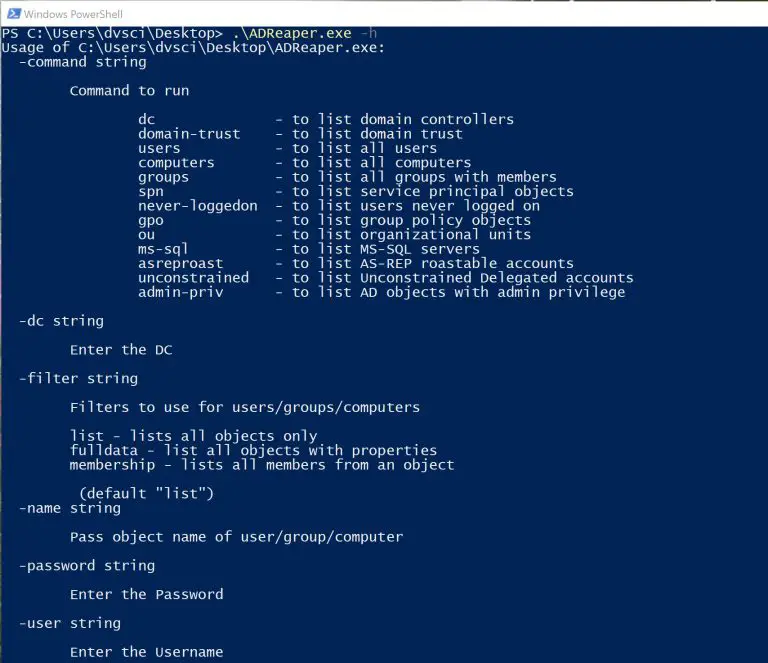
ADReaper ADReaper is a tool written in Golang which enumerates an Active Directory environment with LDAP queries...
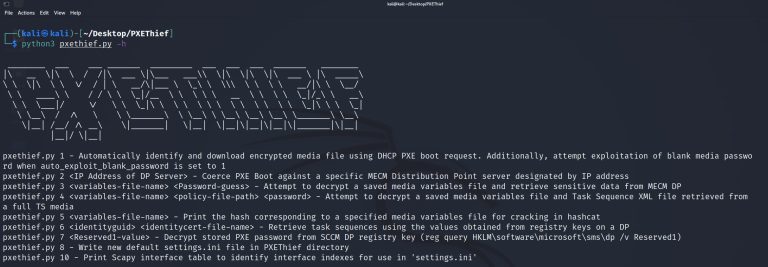
PXEThief PXEThief is a set of tooling that implements attack paths discussed at the DEF CON 30...