Ketshash A little tool for detecting suspicious privileged NTLM connections, in particular, Pass-The-Hash attack, based on event...
Defense
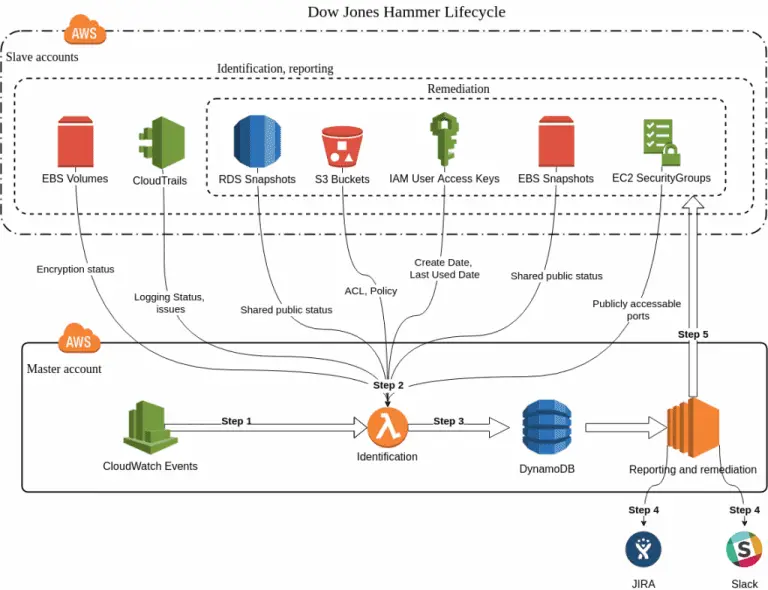
Overview Dow Jones Hammer is a multi-account cloud security tool for AWS. It identifies misconfigurations and insecure...
ssh-hardening This cookbook provides secure ssh-client and ssh-server configurations. This cookbook does not provide capabilities for management...
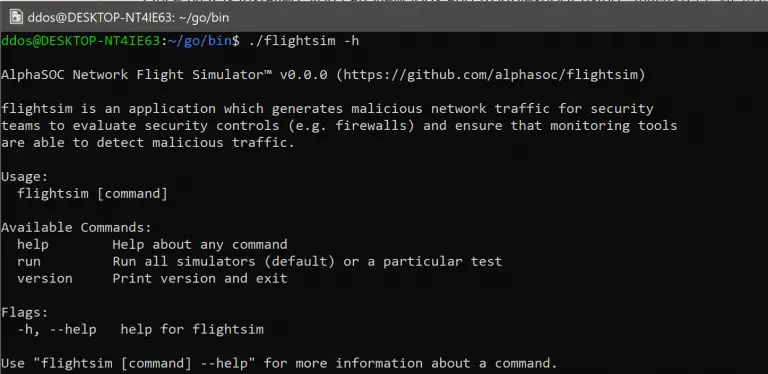
Network Flight Simulator flightsim is a lightweight utility used to generate malicious network traffic and help security teams...
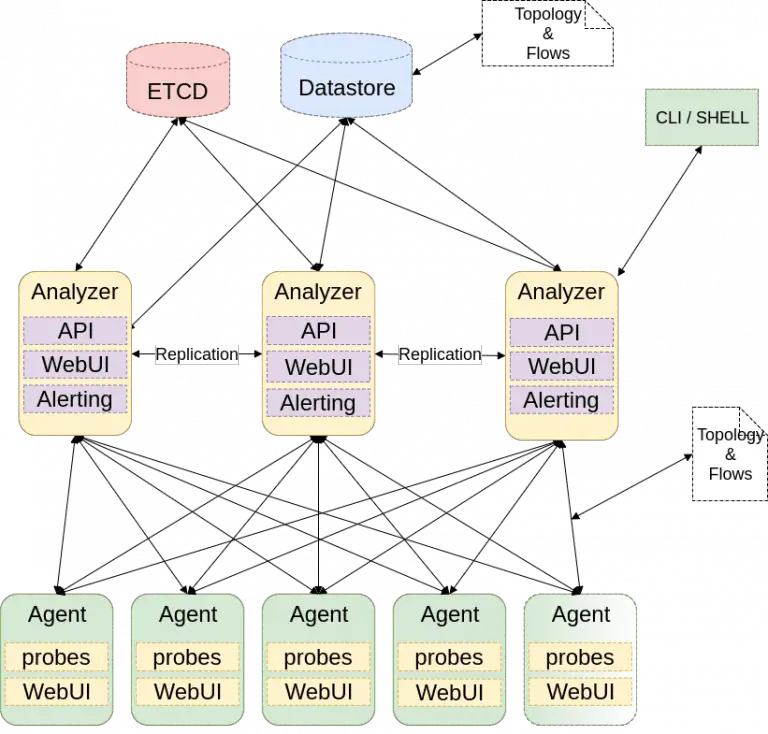
Skydive Skydive is an open-source real-time network topology and protocols analyzer. It aims to provide a comprehensive...
USBGuard is a software framework for implementing USB device authorization policies (what kind of USB devices are...
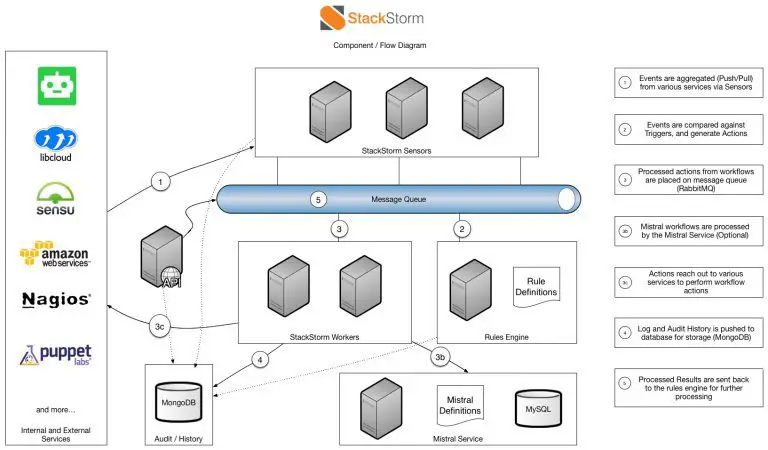
StackStorm is a platform for integration and automation across services and tools. It ties together your existing...
TheHive is a scalable 3-in-1 open source and free Security Incident Response Platform designed to make life...
Sensu A simple, malleable, and scalable framework for composing the monitoring system you need. It is offered...
JShielder JShielder Automated Hardening Script for Linux Servers JSHielder is an Open Source Bash Script developed to...
StalkPhish StalkPhish is a tool created for searching into free OSINT databases for specific phishing kits URL. More, StalkPhish is...
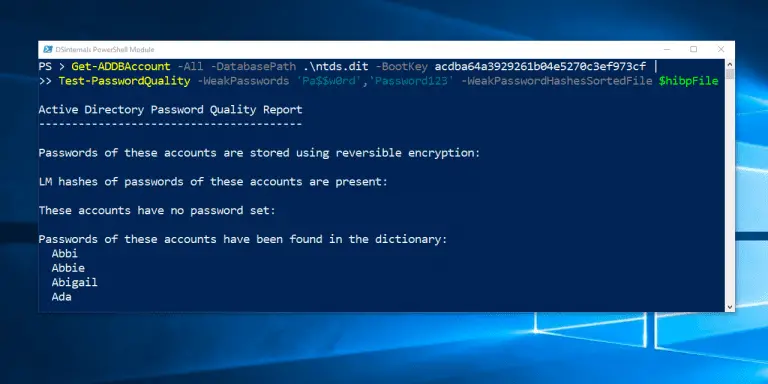
DSInternals PowerShell Module and Framework The DSInternals project consists of these two parts: The DSInternals Framework exposes several internal...
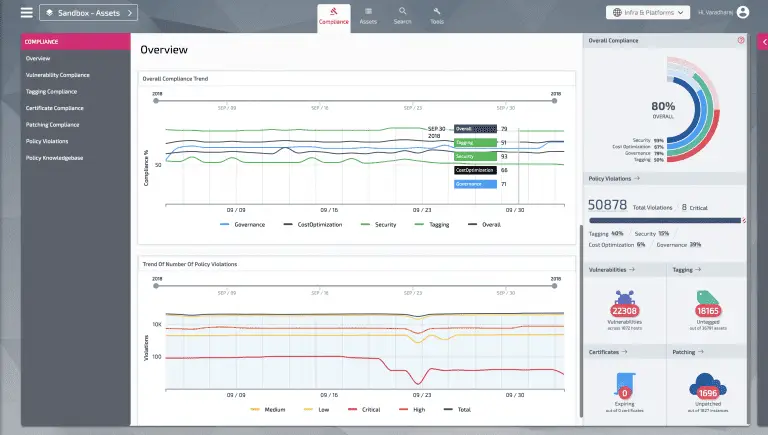
Policy as Code Bot (PacBot) is a platform for continuous compliance monitoring, compliance reporting and security automation...
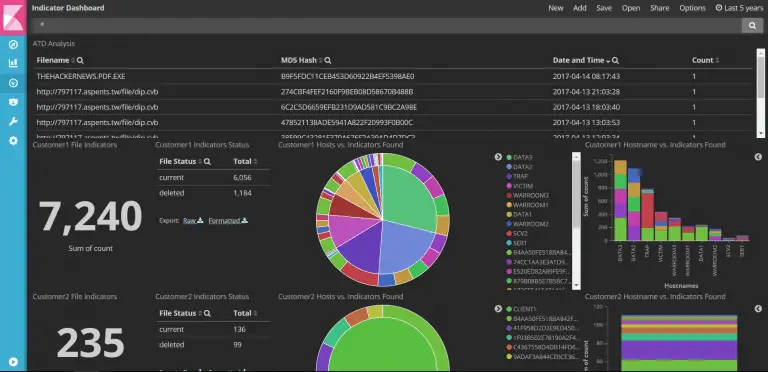
Automated Threat Intelligent System An improvised automated threat intelligent system with advanced vulnerability scanners and Opensource Intelligence...
OSweep Description If you work in IT security, then you most likely use OSINT to help you...