Shodan Shodan, the official definition of himself Computer Search Engine (Computer Resource Search Engine), is American man...
Information Gathering
EMAGNET Emagnet is a very powerful tool for its purpose which is to capture email addresses and...
Prior to an attack, the penetration tester should know as much as possible about the target environment...
linux-smart-enumeration Linux enumeration tools for pentesting and CTFs This project was inspired by LinEnum and uses many...
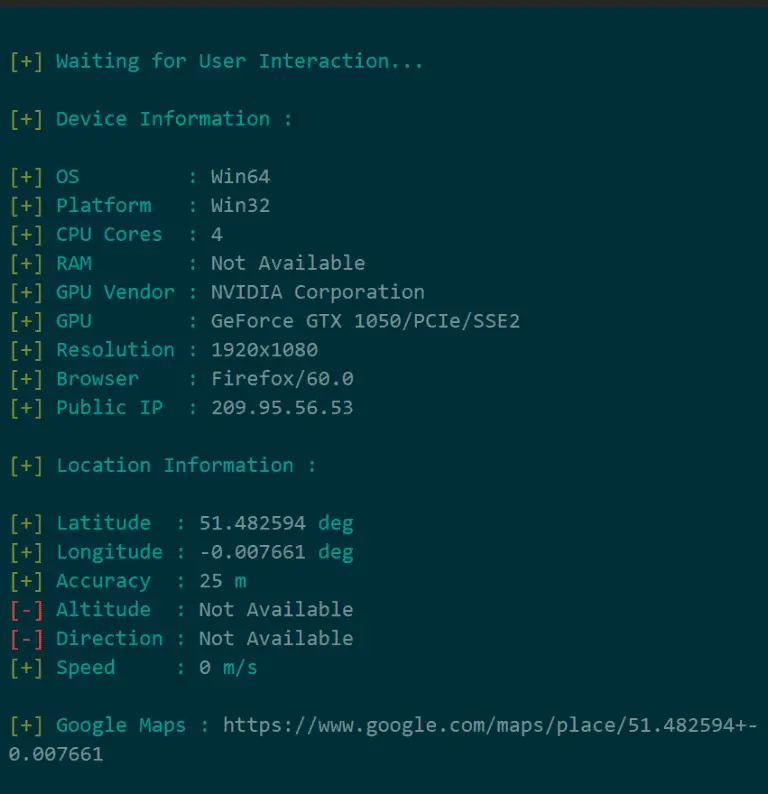
Seeker Introduction Seeker utilizes HTML5, Javascript, JQuery and PHP to grab Device Information and GeoLocation with High Accuracy. Seeker Hosts a fake website...
nmap (“Network Mapper“) is an open-source tool for network exploration and security auditing. It was designed to...
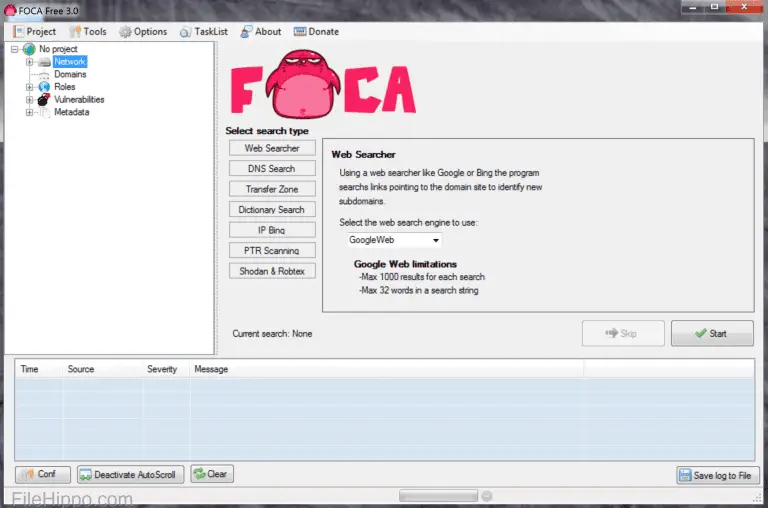
FOCA FOCA (Fingerprinting Organizations with Collected Archives) is a tool used mainly to find metadata and hidden...
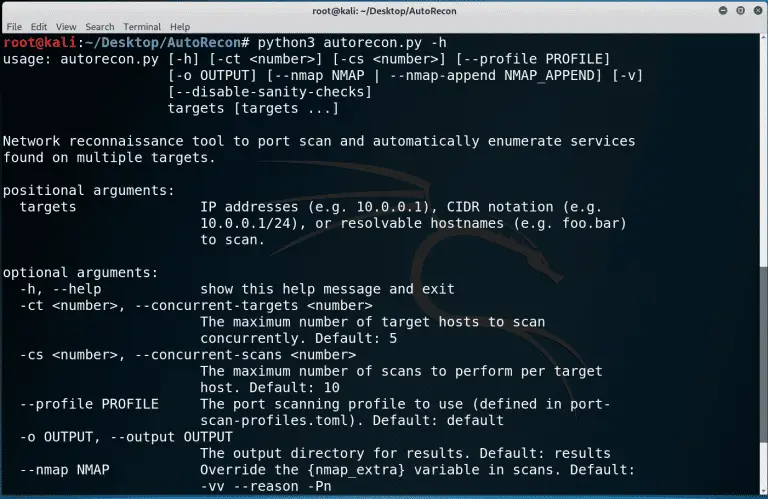
AutoRecon AutoRecon is a multi-threaded network reconnaissance tool which performs automated enumeration of services. It is intended...
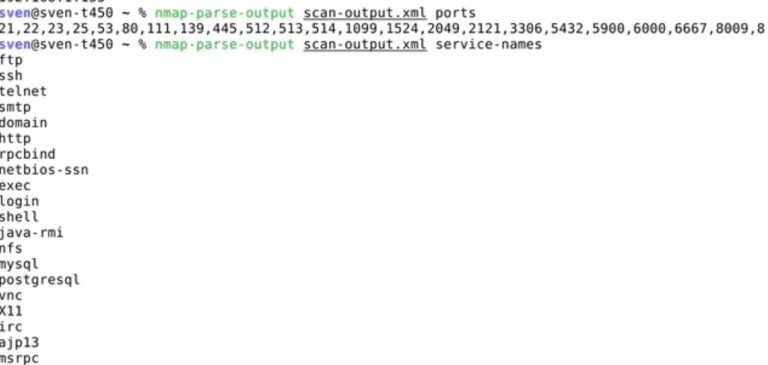
nmap-parse-output Converts/manipulates/extracts data from a nmap scan output. Changelog v1.5.1 More reliable SSL/TLS detection More reliable HTTP(s)...
ATSCAN SCANNER Advanced Search / Dork / Mass Exploitation Scanner Description Search engine Google / Bing /...
Shodan is a search engine for Internet-connected devices. Google lets you search for websites, Shodan lets you...
Fresh Onions TOR Hidden Service Crawler This is a copy of the source for the http://zlal32teyptf4tvi.onion hidden service,...
StalkPhish StalkPhish is a tool created for searching into free OSINT databases for specific phishing kits URL. More, StalkPhish is...
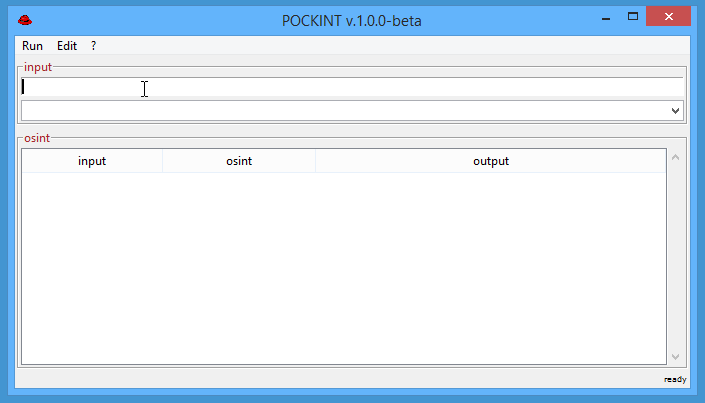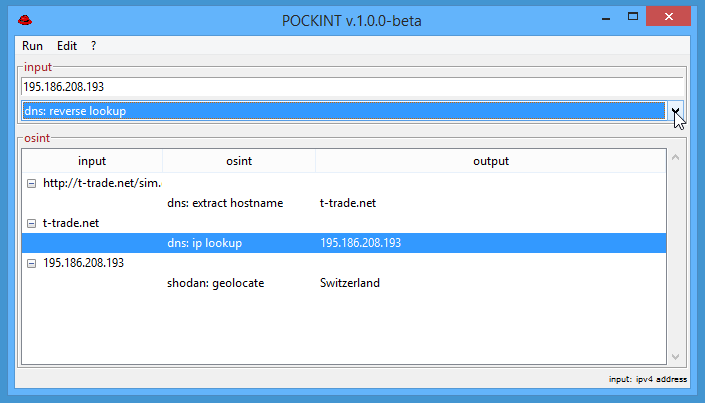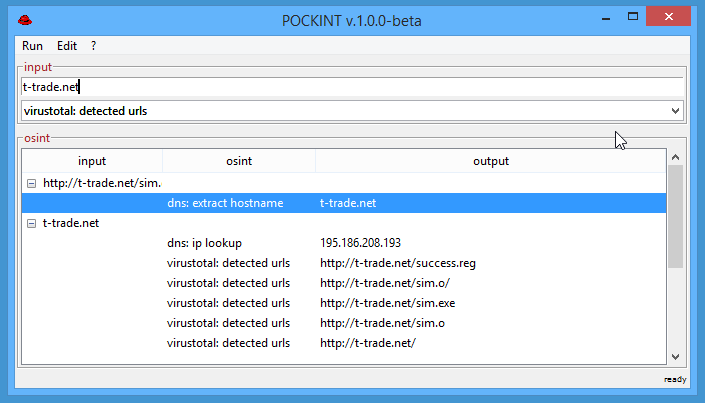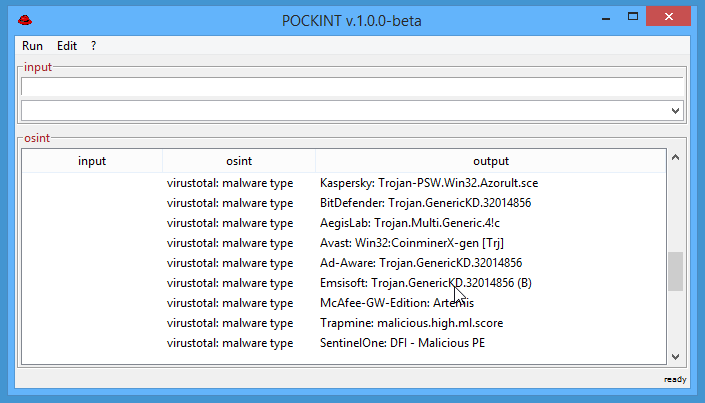
POCKINT (a.k.a. Pocket Intelligence) is the OSINT swiss army knife for DFIR/OSINT professionals. Designed to be a...
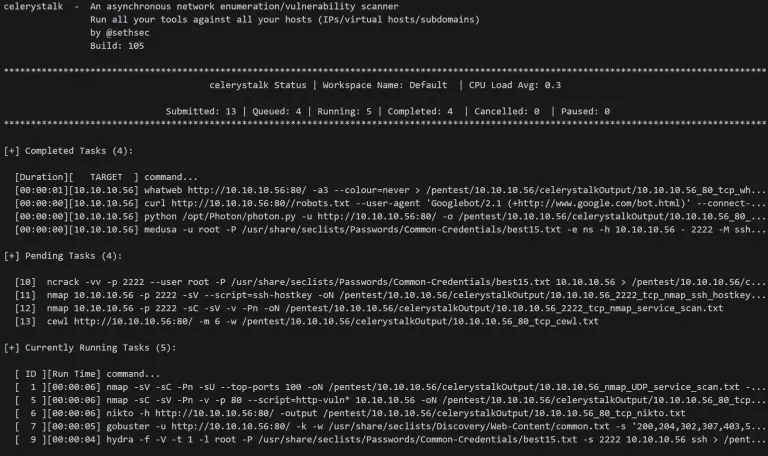
celerystalk celerystalk helps you automate your network scanning/enumeration process with asynchronous jobs (aka tasks) while retaining full control...