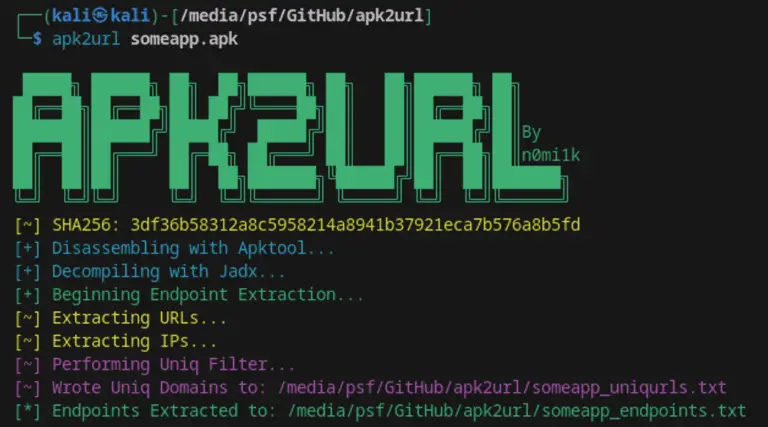
apk2url apk2url easily extracts URL and IP endpoints from an APK file to a .txt output. This...
Network PenTest
VulnMapAI VulnMapAI combines the power of Nmap’s detailed network scanning and the advanced natural language processing capabilities...
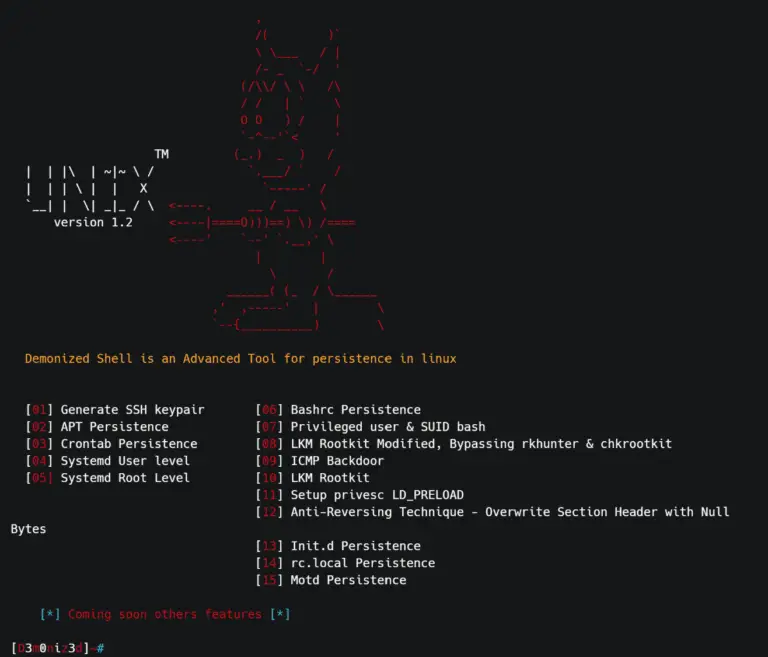
D3m0n1z3dShell Demonized Shell is an Advanced Tool for persistence in Linux. Demonized Features Auto Generate SSH keypair...
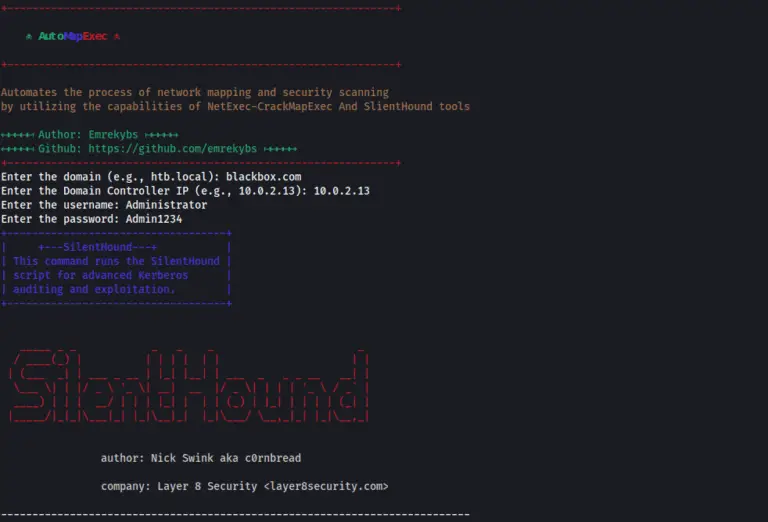
AD-AssessmentKit These tools are ideal for network administrators and cybersecurity professionals seeking to assess and enhance the...
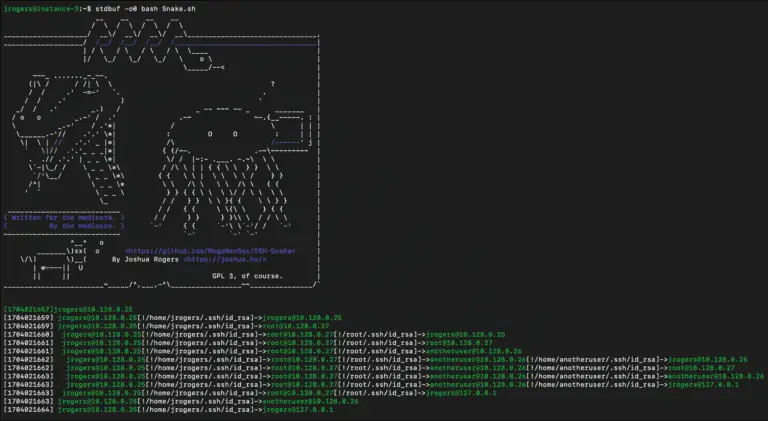
SSH-Snake: Automated SSH-Based Network Traversal SSH-Snake is a powerful tool designed to perform automatic network traversal using...
DynastyPersist A CTF Tool for Linux persistence (KOTH, Battlegrounds) A powerful and versatile Linux persistence script designed...
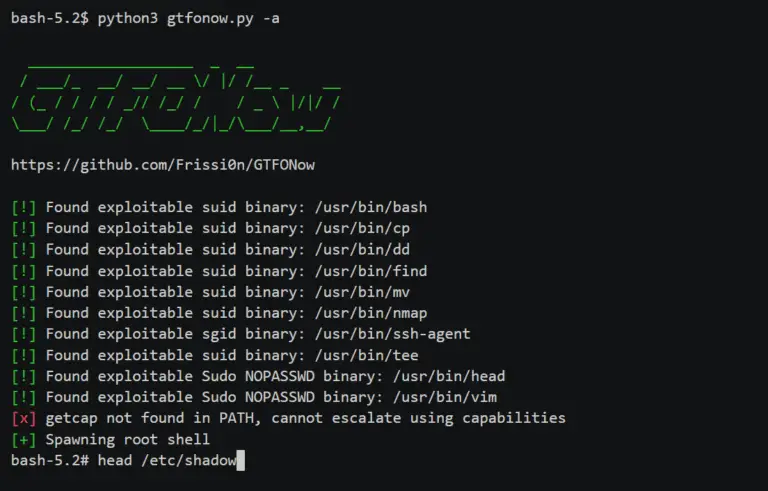
GTFONow Automatic privilege escalation on Unix systems by exploiting misconfigured setuid/setgid binaries, capabilities, and sudo permissions. Designed...
Stinger CIA Vault7 leak describes Stinger as a Privilege Escalation module in the “Fine Dining” toolset. Stinger...
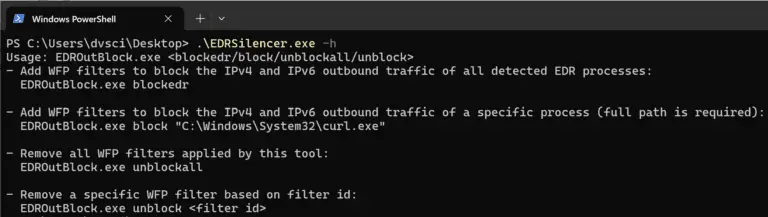
EDRSilencer Inspired by the closed-source FireBlock tool FireBlock from MdSec NightHawk, I created my version. This tool...
GraphGenie GraphGenie is a bug-finding tool to detect logic bugs and performance issues (we also find internal...
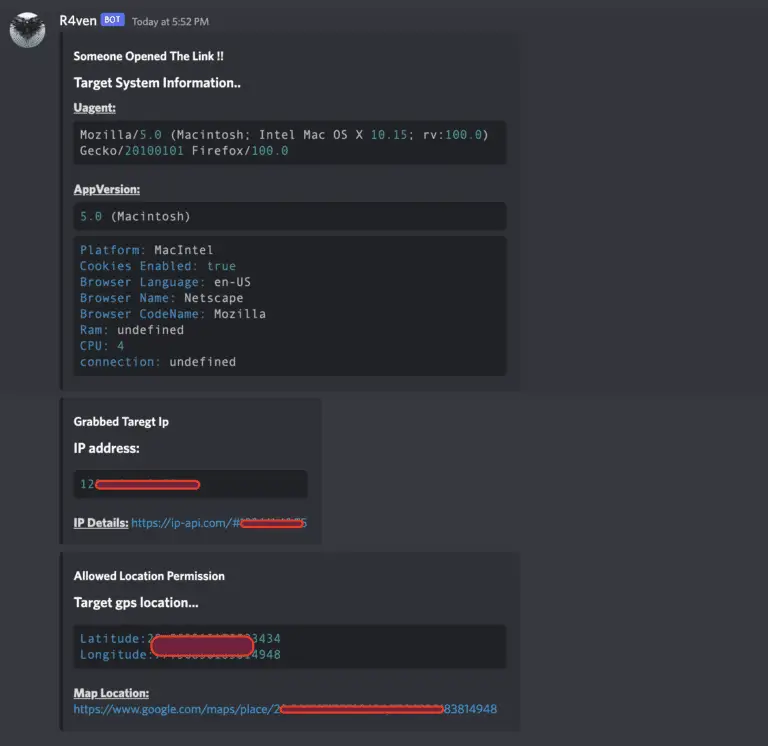
r4ven The tool hosts a fake website that uses an iframe to display a legit website and,...
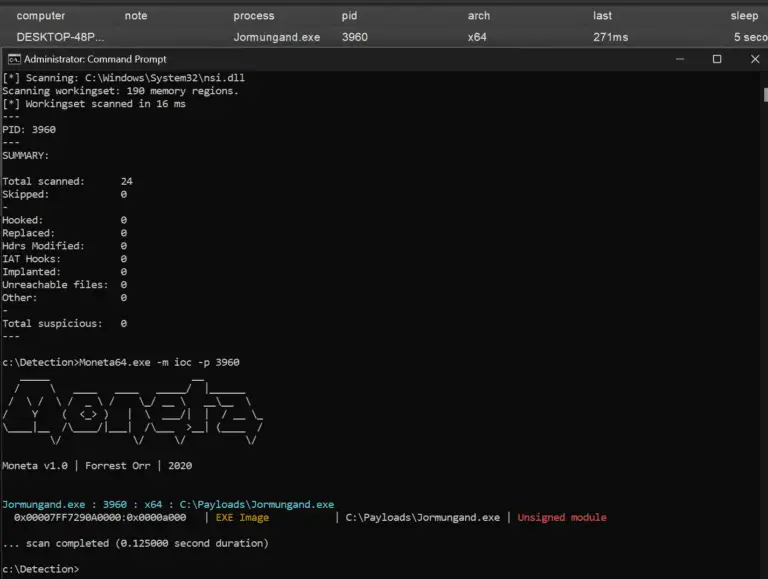
Jomungand Shellcode Loader with memory evasion by @DallasFR How does it work? I use HWBP to hook...
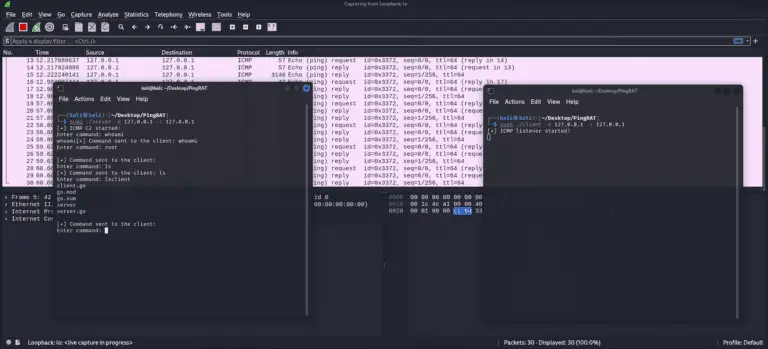
PingRAT PingRAT secretly passes C2 traffic through firewalls using ICMP payloads. Features: Uses ICMP for Command and...
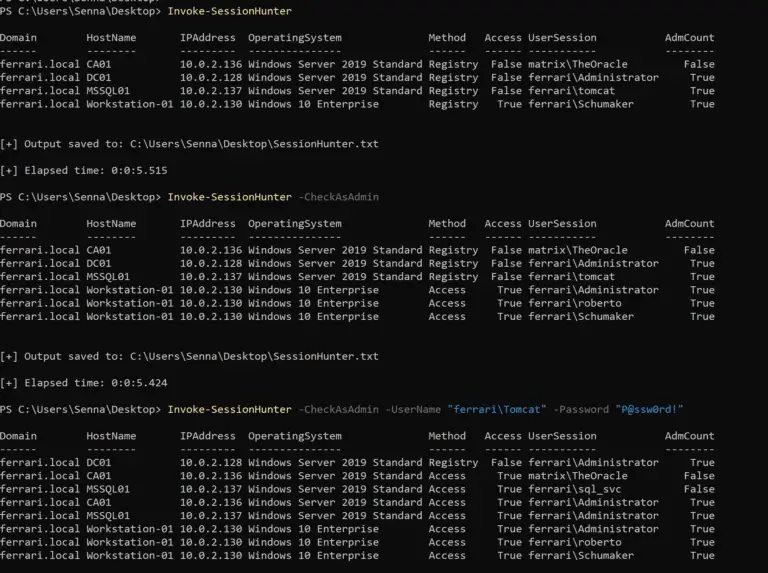
Invoke-SessionHunter Retrieve and display information about active user sessions on remote computers. No admin privileges are required....
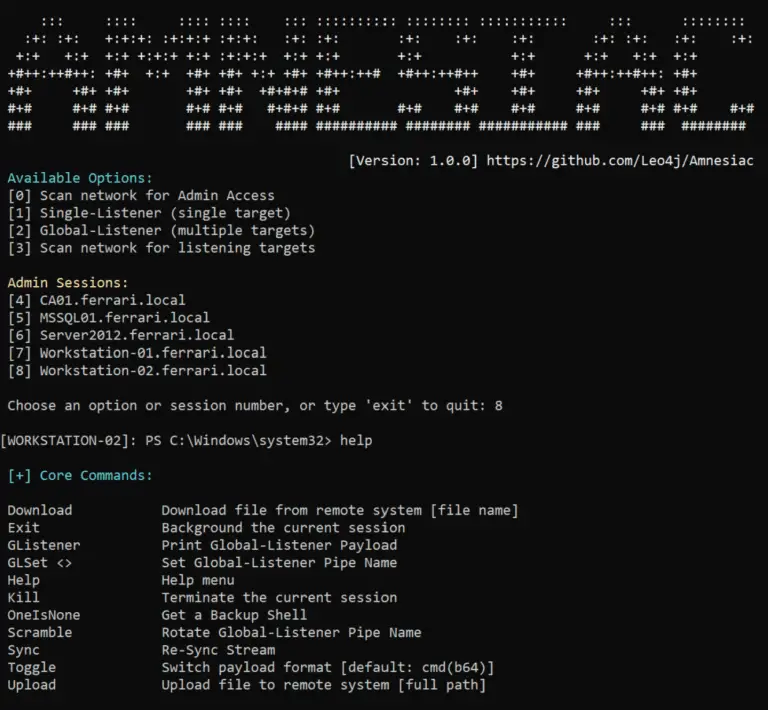
Amnesiac Amnesiac is a post-exploitation framework designed to assist with lateral movement within active directory environments. Amnesiac...