Sandmap is a tool for supporting network and system reconnaissance using the massive Nmap engine. It provides a user-friendly...
Information Gathering
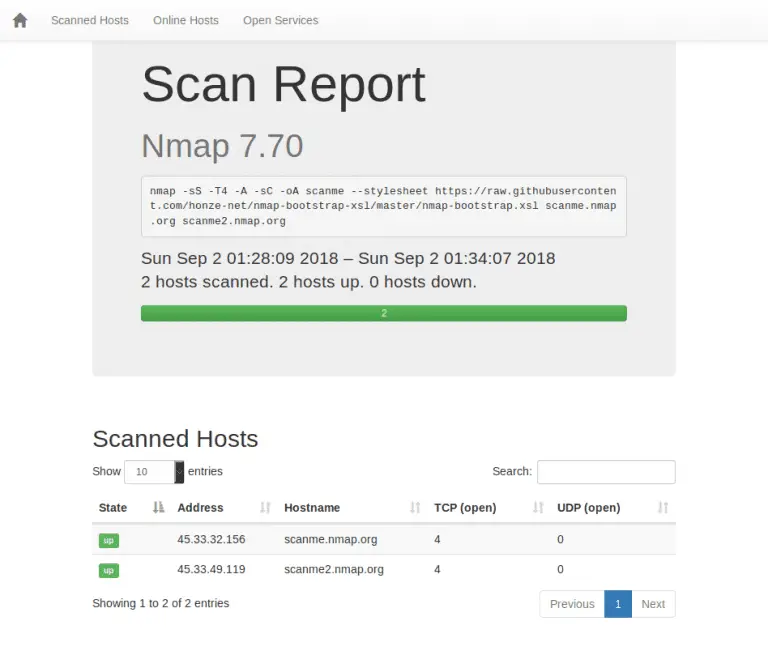
nmap-bootstrap-xsl A Nmap XSL implementation with Bootstrap. Download git clone https://github.com/honze-net/nmap-bootstrap-xsl.git How to use Add the nmap-bootstrap.xsl as stylesheet to...
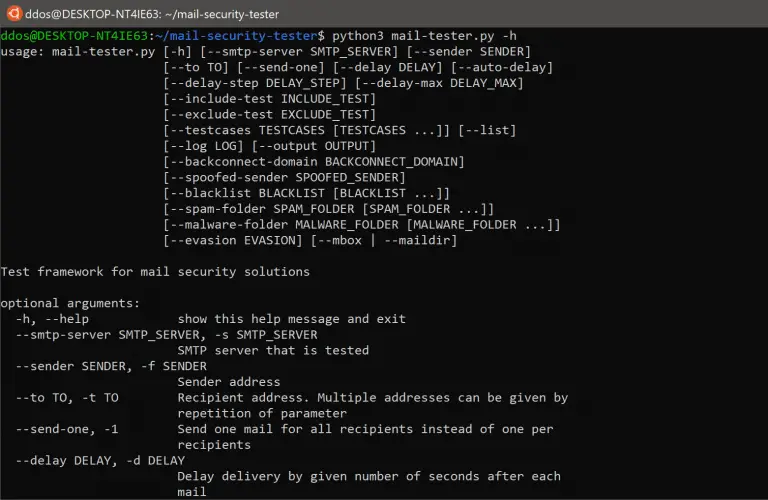
Mail Security Testing Framework A testing framework for mail security and filtering solutions. IMPORTANT: Don’t do anything evil...
GoogleScraper – Scraping search engines professionally GoogleScraper parses Google search engine results (and many other search engines _)...
Pocsuite is an open-sourced remote vulnerability testing and proof-of-concept development framework developed by the Knownsec Security Team. It...
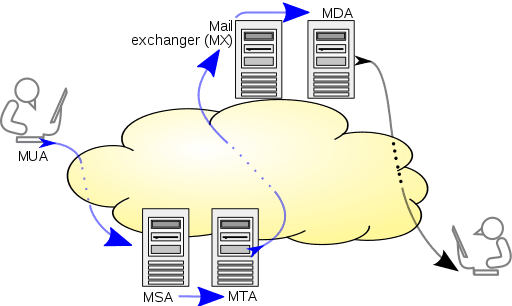
Swaks’ primary design goal is to be a flexible, scriptable, transaction-oriented SMTP test tool. It handles SMTP...
trape (open source) People tracker on the Internet: Learn to track the world, to avoid being traced....
reconerator This is a custom .NET assembly which will perform a number of situational awareness activities. There...
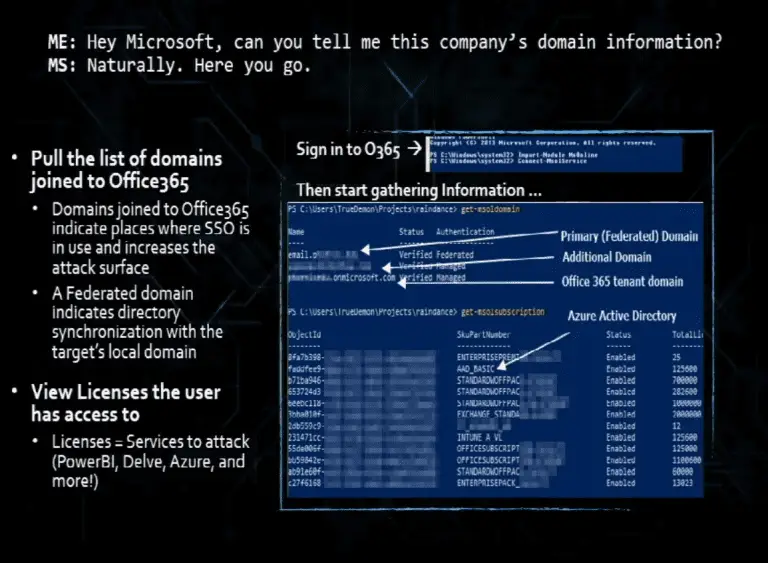
RainDance A toolkit for enumerating and collecting information from Office 365. Raindance uses built-in powershell modules, namely...
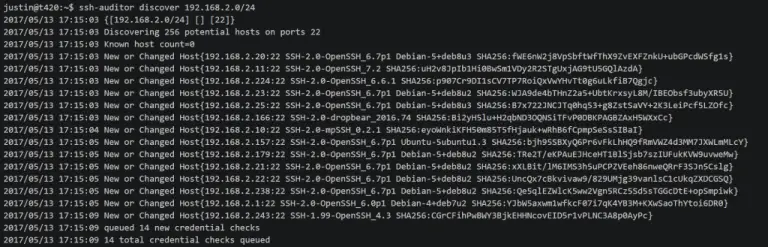
SSH Auditor The best way to scan for weak ssh passwords on your network Features ssh-auditor will...
ADRecon: Active Directory Recon ADRecon is a tool which extracts and combines various artifacts (as highlighted below)...
Nili is a Tool for Network Scan, Man in the Middle, Protocol Reverse Engineering, and Fuzzing. Prerequisites...
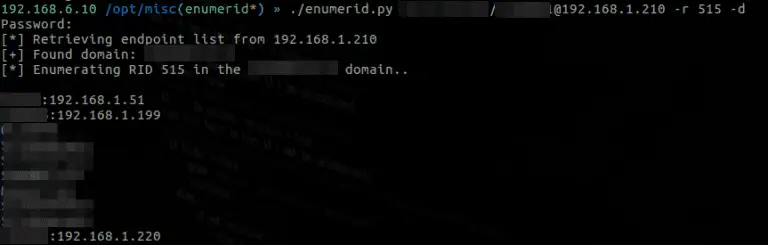
enumerid Enumerid is an impacket based Relative Identifier (RID) enumeration utility. It was initially created to solve a common...
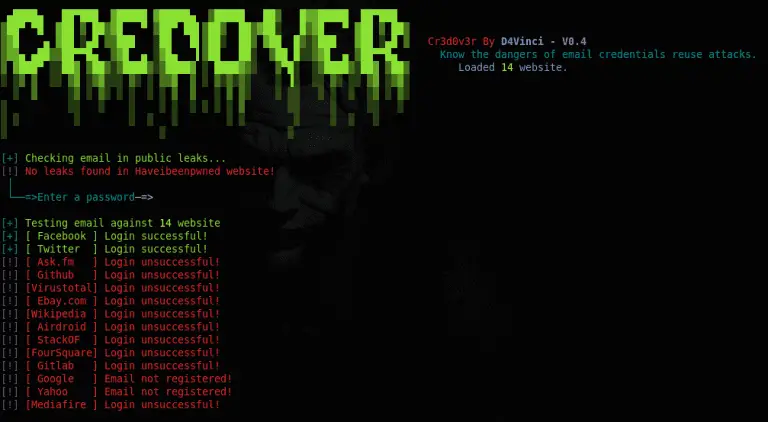
Cr3dOv3r Your best friend in credential reuse attacks. You give Cr3dOv3r an email then it does two...
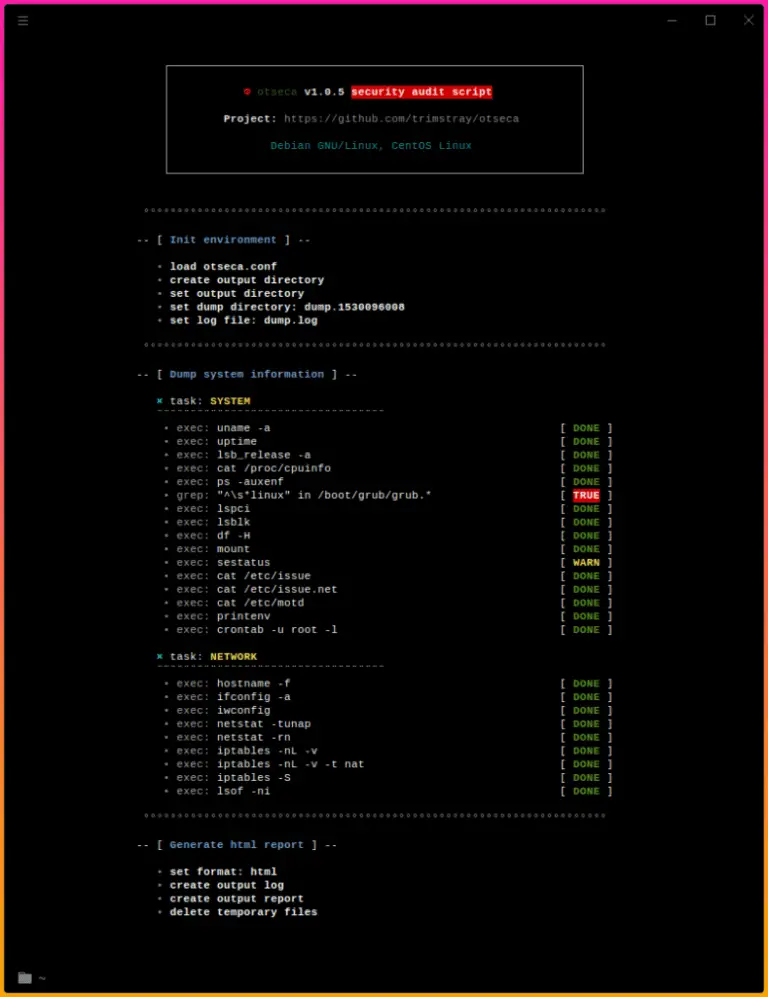
Open-source security auditing tool to search and dump system configuration. Otseca is an open-source security auditing tool...