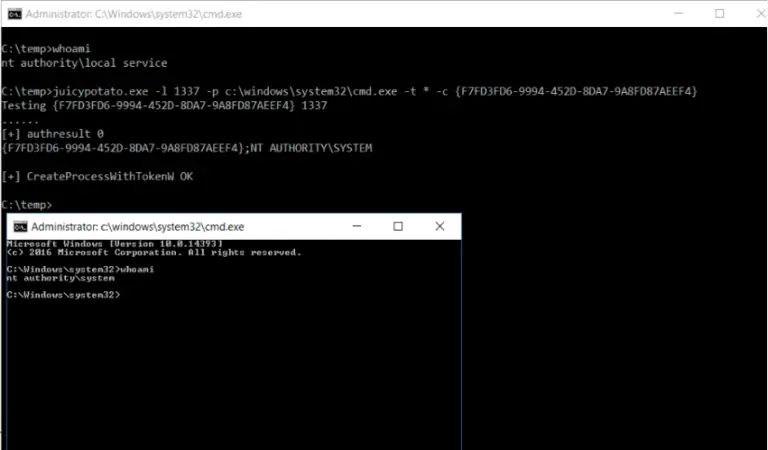
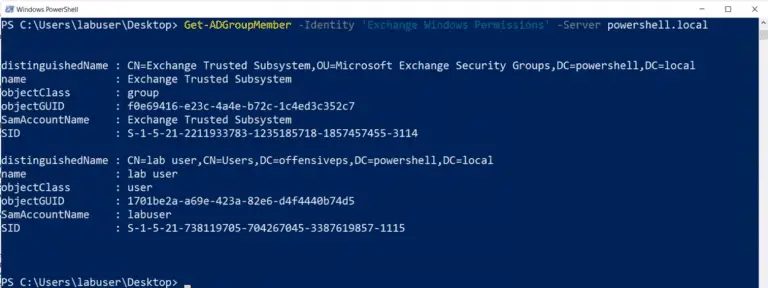
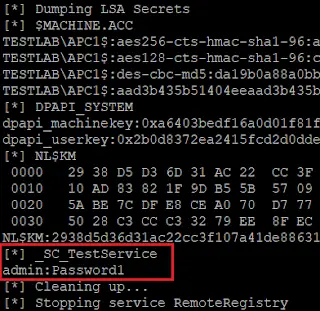
Juicy Potato (abusing the golden privileges) A sugared version of RottenPotatoNG, with a bit of juice, i.e. another Local...
Post Exploitation
RACE RACE is a PowerShell module for executing ACL attacks against Windows targets and Active Directory. RACE...
wmiServSessEnum multithreaded .net tool that uses WMI queries to enumerate active user sessions and accounts configured to...
AADInternals AAD Internals is a PowerShell module where I’ve tried to put all the knowledge I’ve gained...
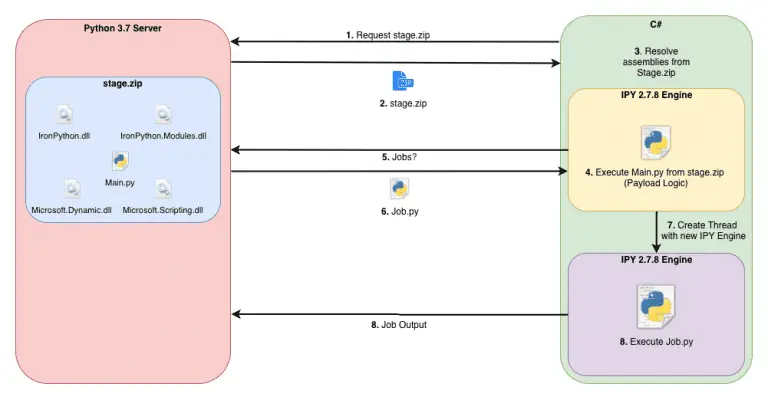
SILENTTRINITY SILENTTRINITY is modern, asynchronous, multiplayer & multiserver C2/post-exploitation framework powered by Python 3 and .NETs DLR....
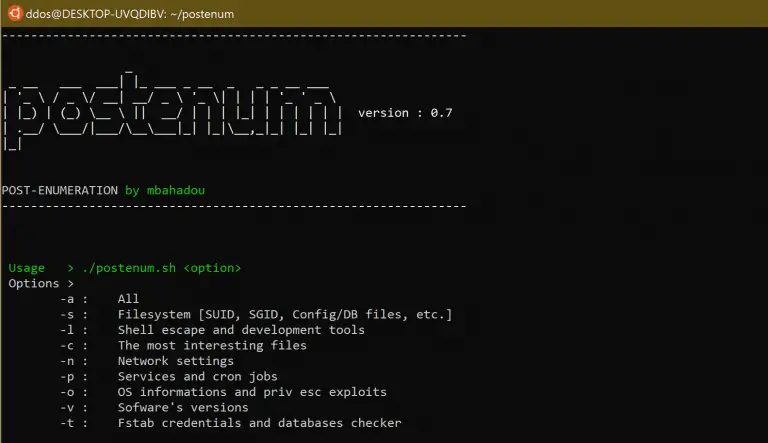
Postenum is a clean, nice, and easy tool for basic/advanced privilege escalation vectors/techniques. Postenum tool is intended...
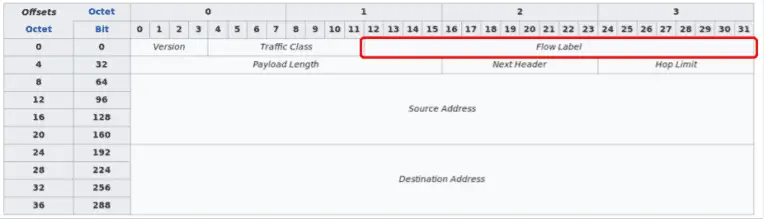
IPv6teal IPv6teal is a Python 3 tool to stealthily exfiltrate data from an internal network using a covert...
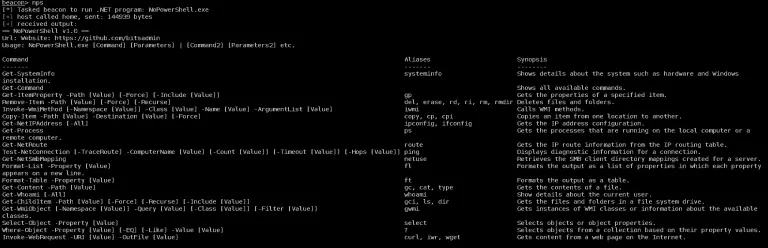
NoPowerShell NoPowerShell is a tool implemented in C# which supports executing PowerShell-like commands while remaining invisible to...
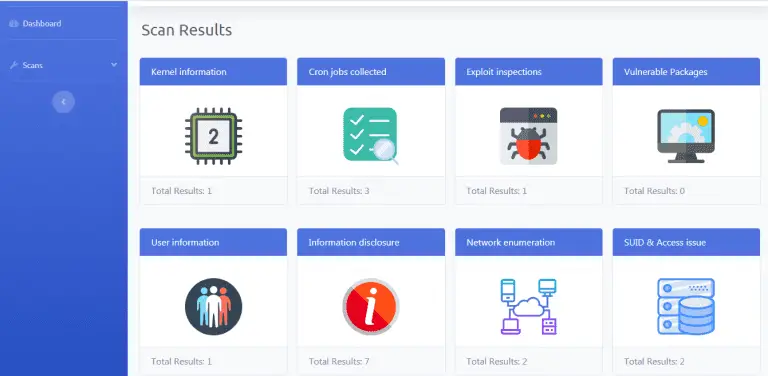
0xsp Mongoose Linux Privilege Escalation intelligent Enumeration Toolkit 0xsp mongoose red version is provided to assist your...
Mimikatz is an open-source gadget written in C, launched in April 2014. It is very powerful, support...
Active Directory Assessment and Privilege Escalation (ADAPE) Script This script will do the following: • Gather hashes...
LinEnum – Scripted Local Linux Enumeration & Privilege Escalation Checks For more information visit www.rebootuser.com Note: Export functionality is...
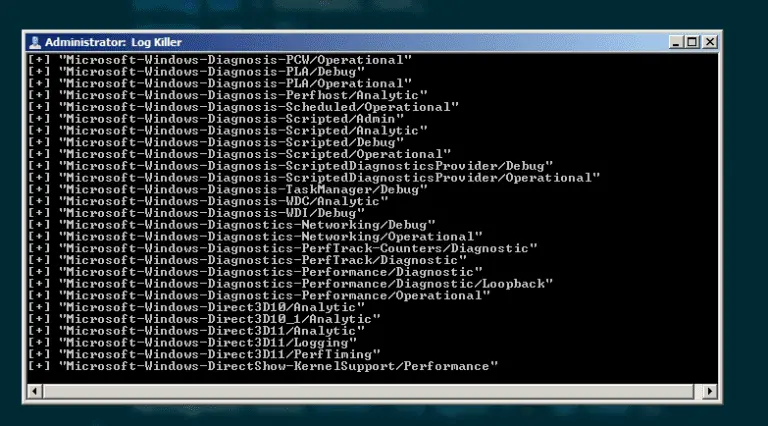
Log-killer Log Killer is a tool for [Linux/Windows] Servers. This tool will delete all your logs, just...
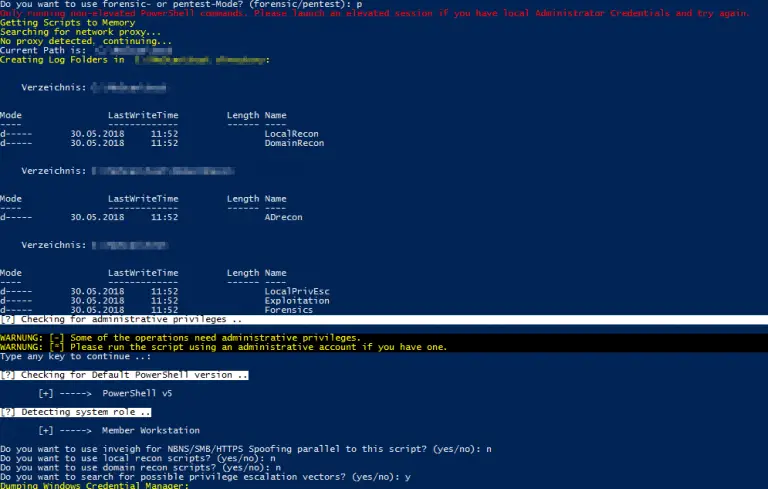
WinPwn Automation for internal Windows Penetration Testing. 1) Automatic Proxy Detection 2) Elevated or unelevated Detection 3)...
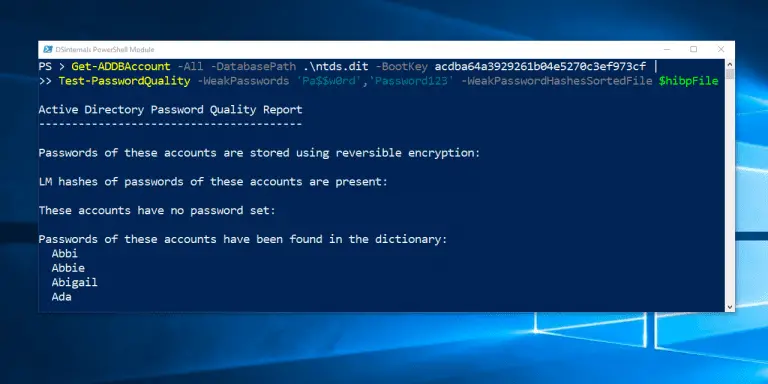
DSInternals PowerShell Module and Framework The DSInternals project consists of these two parts: The DSInternals Framework exposes several internal...