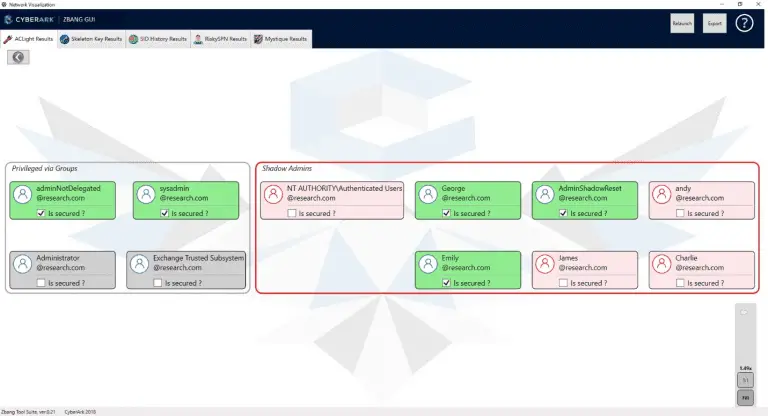
zBang is a special risk assessment tool that detects potential privileged account threats in the scanned network....
Post Exploitation
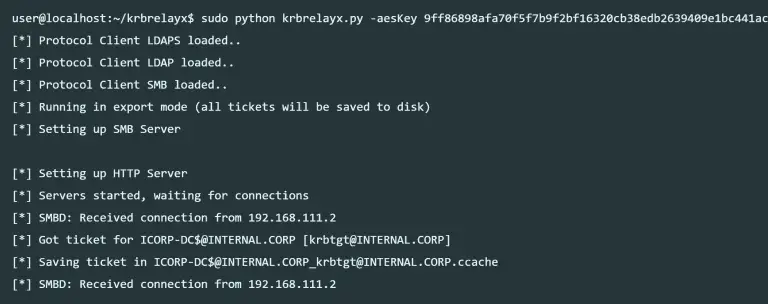
Krbrelayx – Unconstrained delegation abuse toolkit Toolkit for abusing unconstrained delegation. Requires impacket and ldap3 to function. It is recommended to...
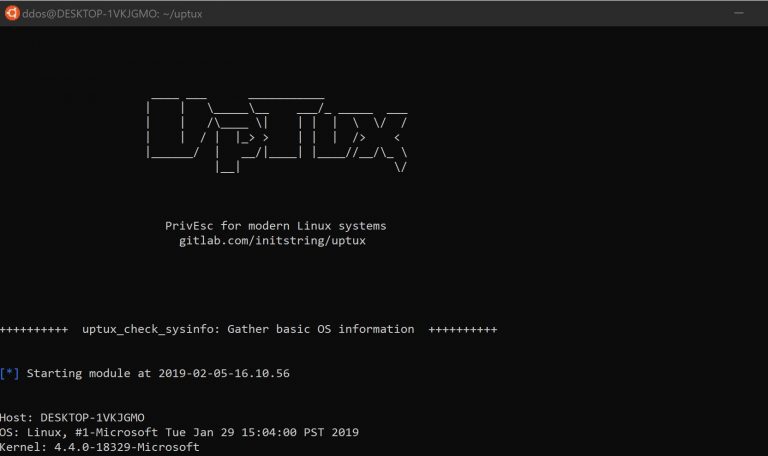
uptux Privilege escalation checks for Linux systemd. This tool checks for issues on Linux systems that may...
UACMe Defeating Windows User Account Control by abusing the built-in Windows AutoElevate backdoor. System Requirements x86-32/x64 Windows...
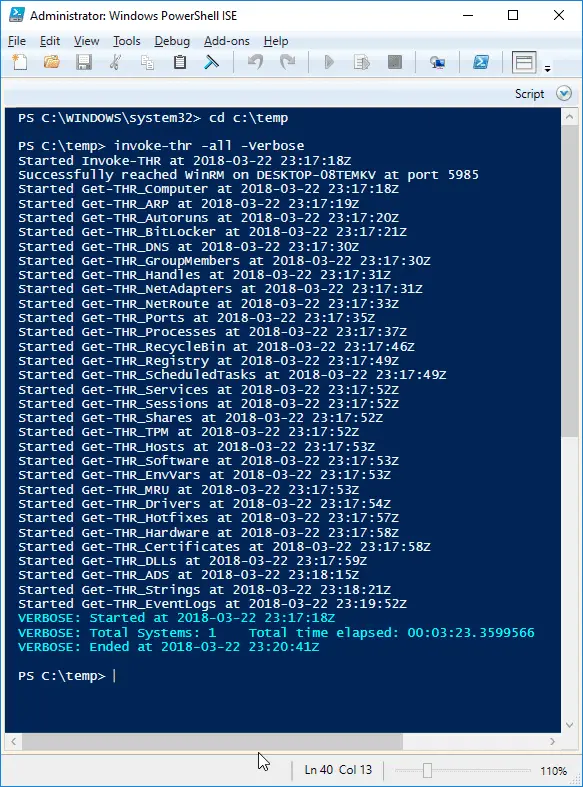
THRecon THRecon -Threat Hunting Reconnaissance Toolkit- A collection of PowerShell modules designed for artifact gathering and reconnaissance...
Red Team Powershell Scripts Various PowerShell scripts that may be useful during a red team exercise ...
SharpCloud SharpCloud is a simple C# utility for checking for the existence of credential files related to...
LiMEaide LiMEaide is a python application designed to remotely dump RAM on a Linux client and create...
BloodHound.py BloodHound.py is a Python-based ingestor for BloodHound, based on Impacket. This version of BloodHound.py is only compatible with BloodHound...
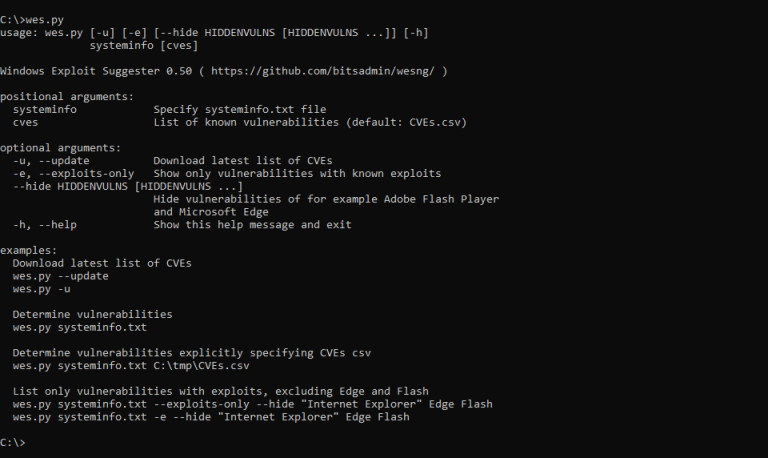
Windows Exploit Suggester – Next Generation (WES-NG) WES-NG is a tool based on the output of Windows’...
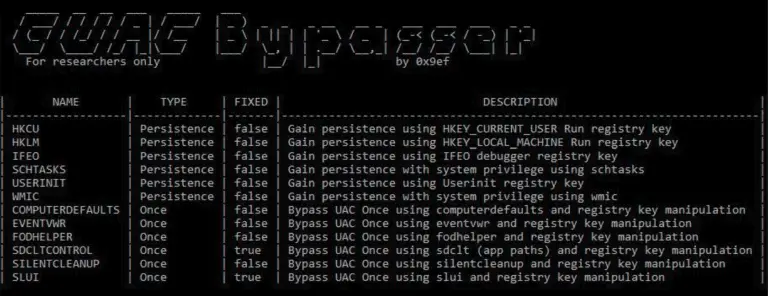
Golang UAC Bypasser (GUACBP) Collection of bypass techniques written in Golang. Rewrite of – https://github.com/rootm0s/WinPwnage to Golang. Techniques implemented:...
Merlin Merlin is a cross-platform post-exploitation HTTP/2 Command & Control server and agent written in golang. An...
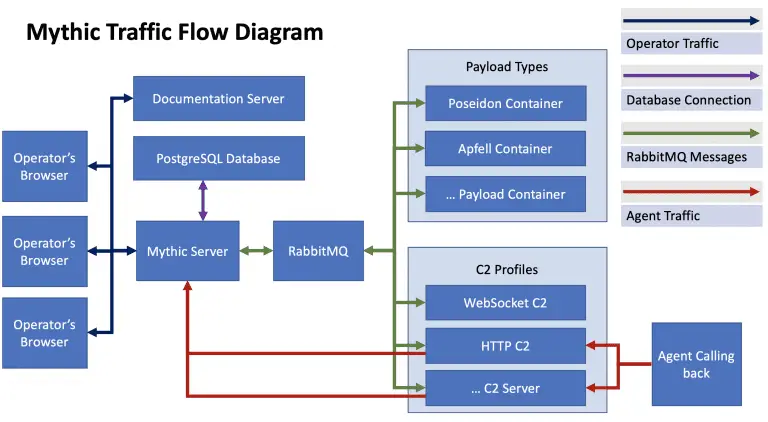
Mythic Mythic is a multiplayer, command, and control platform for red teaming operations. It is designed to...
kekeo kekeo is a little toolbox I have started to manipulate Microsoft Kerberos in C (and for fun)...
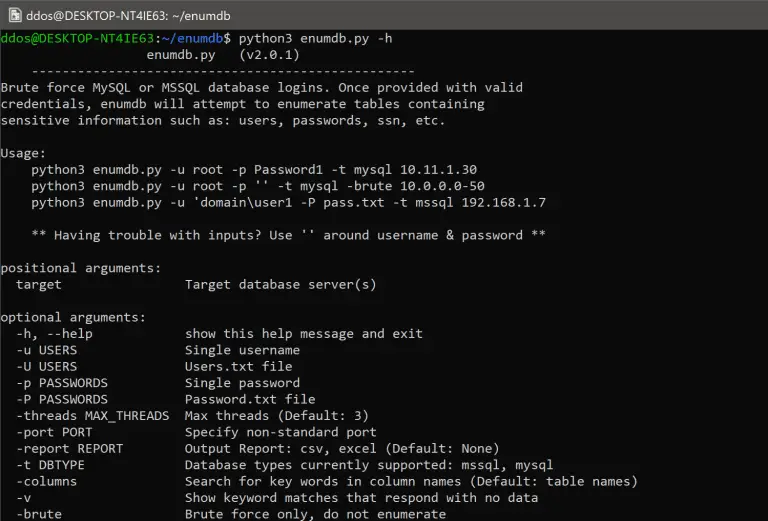
Enumdb is a brute force and post-exploitation tool for MySQL and MSSQL databases. When provided a list...