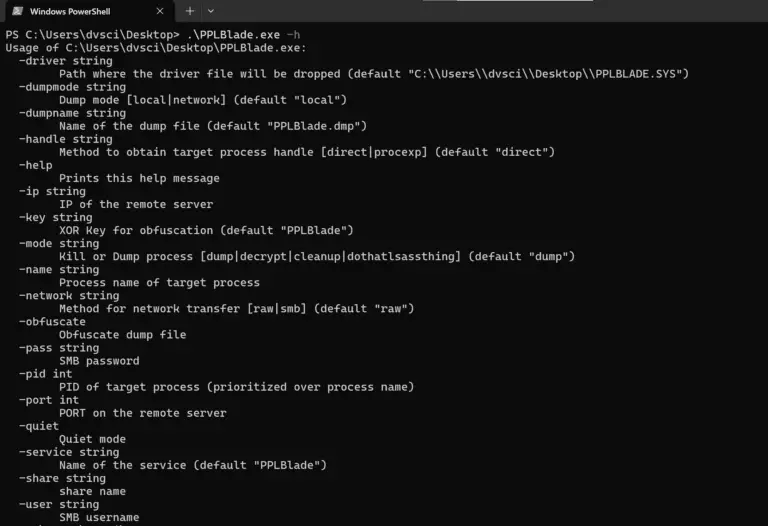
PPLBlade Protected Process Dumper Tool that supports obfuscating memory dump and transferring it on remote workstations without...
Network PenTest
nysm: A stealth post-exploitation container With the rise in popularity of offensive tools based on eBPF, going...
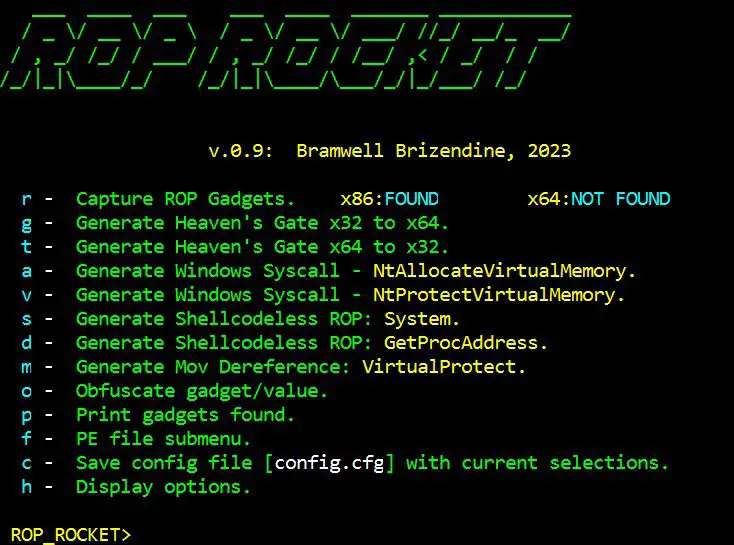
Introducing the ROP ROCKET This new, advanced ROP framework made its debut at DEF CON 31 with...
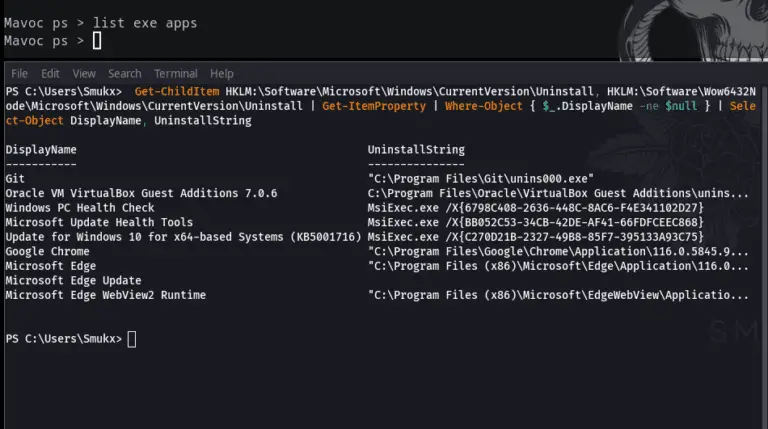
Mavoc C2 Framework Mavoc is a tool used to pentest Windows and Linux machines. This tool mainly...
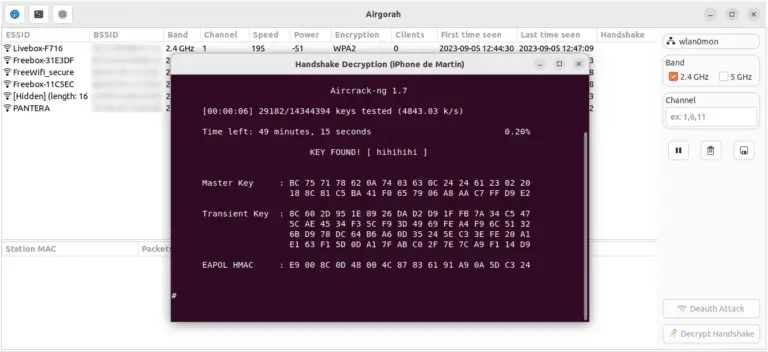
airgorah Airgorah is a WiFi auditing software that can discover the clients connected to an access point, perform...
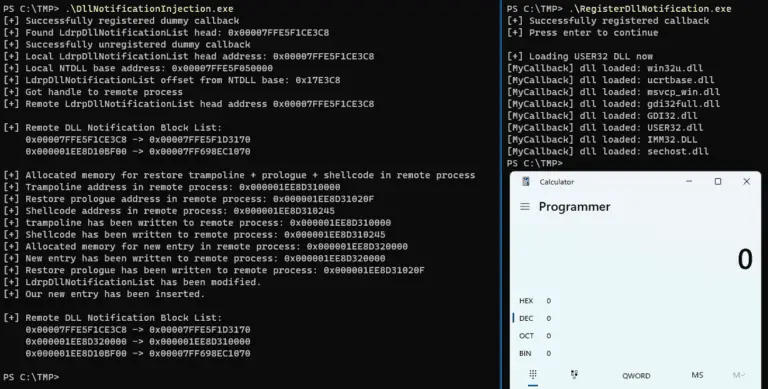
DllNotificationInjection DllNotificationInection is a POC of a new “threadless” process injection technique that works by utilizing the...
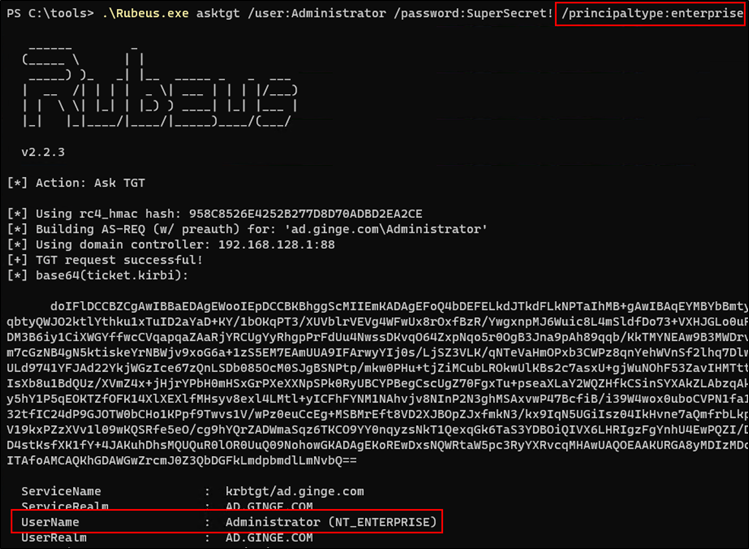
gssapi-abuse gssapi-abuse was released as part of my DEF CON 31 talk. A full write-up on the...
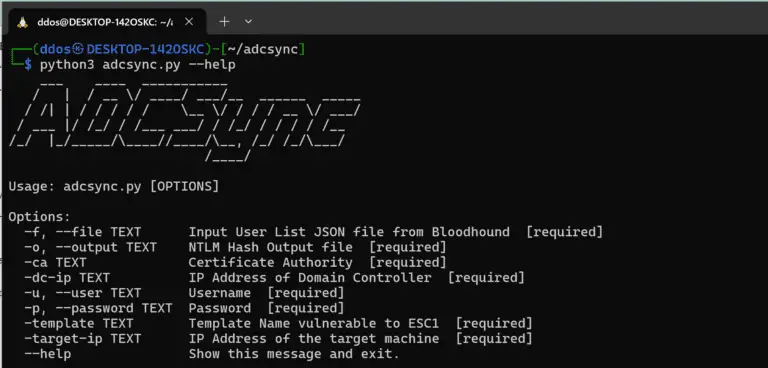
ADCSync ADCSync uses the ESC1 exploit to dump NTLM hashes from user accounts in an Active Directory...
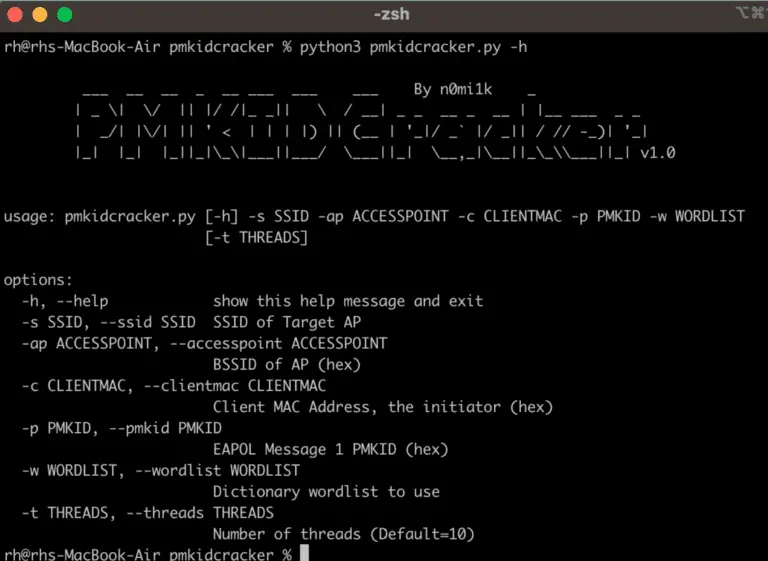
pmkidcracker This program is a tool written in Python to recover the pre-shared key of a WPA2...
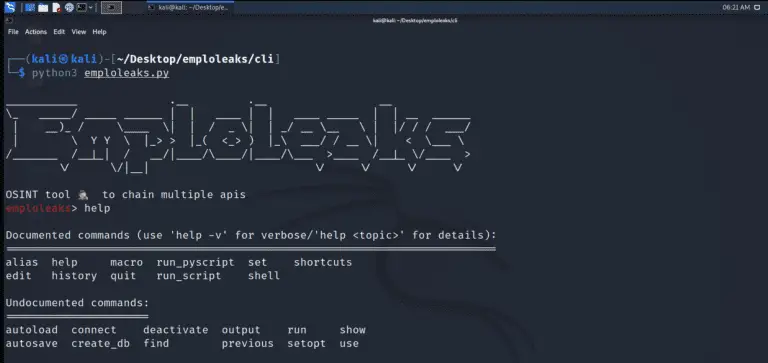
EmploLeaks This is a tool designed for Open Source Intelligence (OSINT) purposes, which helps to gather information...
unshackle – Password Bypass Tool Unshackle is an open-source tool to bypass Windows and Linux user passwords from...
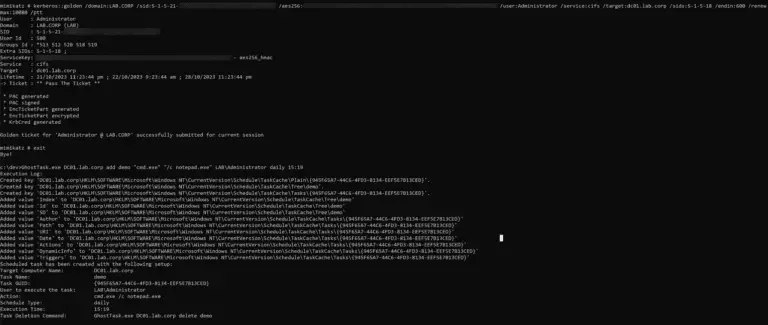
Ghost Scheduled Task While using scheduled tasks as a means of persistence is not a novel approach,...
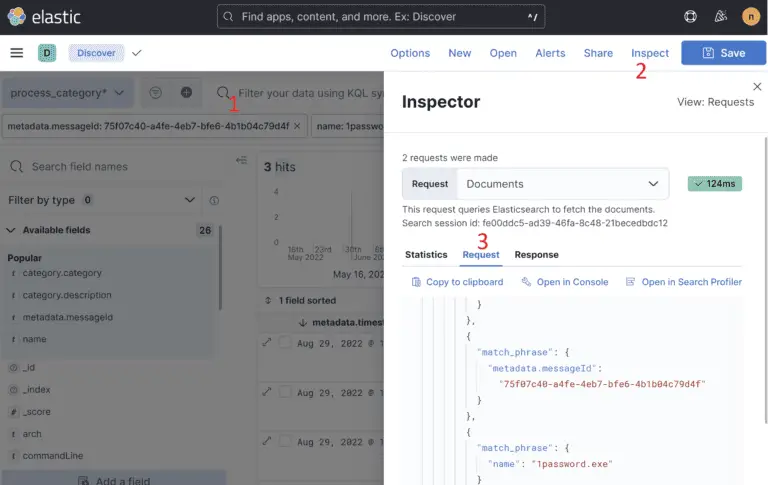
Nemesis Nemesis is an offensive data enrichment pipeline and operator support system. Built on Kubernetes with scale...
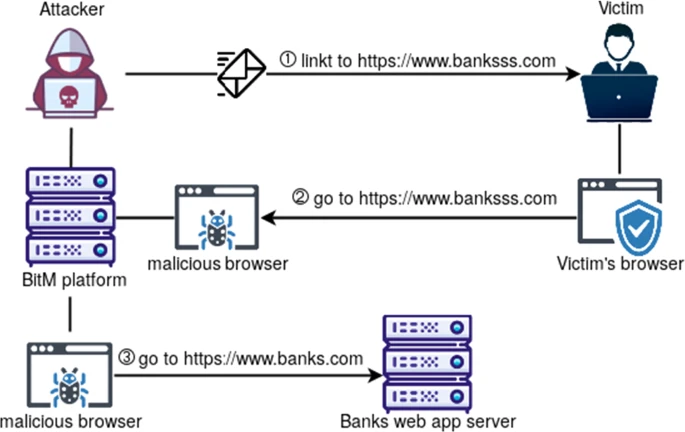
CuddlePhish Weaponized multi-user browser-in-the-middle (BitM) for penetration testers. This attack can be used to bypass multi-factor authentication...
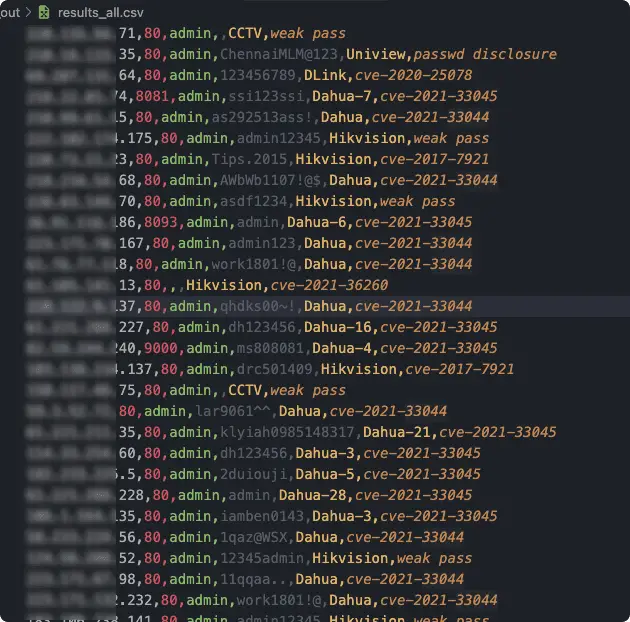
Ingram This is a webcam device vulnerability scanning tool, that already supports Hikvision, Dahua, and other devices....