kerberoast Kerberos attack toolkit -pure python- Install pip3 install kerberoast Use For the impatient IMPORTANT: the accepted...
Post Exploitation
MacShell MacShell is a macOS post-exploitation tool written in python using encrypted sockets. I wrote this tool...
MacShellSwift MacShellSwift is a proof of concept MacOS post-exploitation tool written in Swift using encrypted sockets. This...
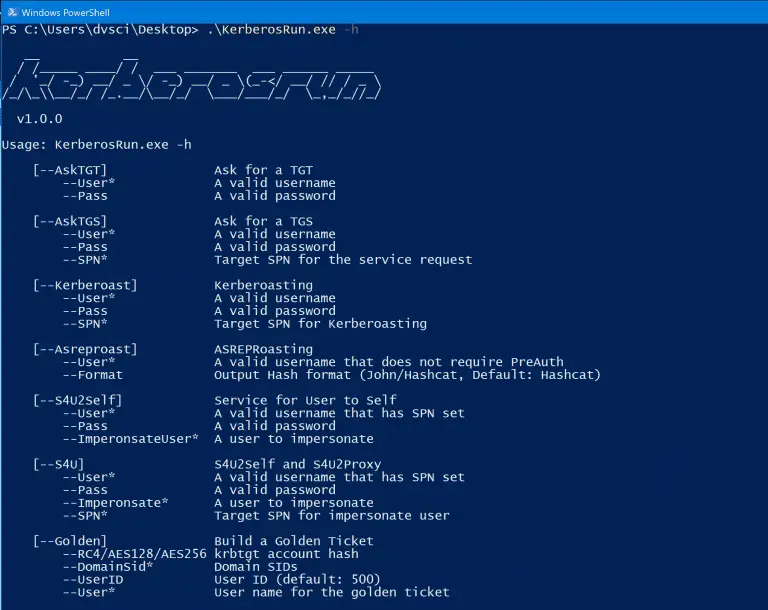
KerberosRun KerberosRun is a little tool I use to study Kerberos internals together with my ADCollector. I’ll try...
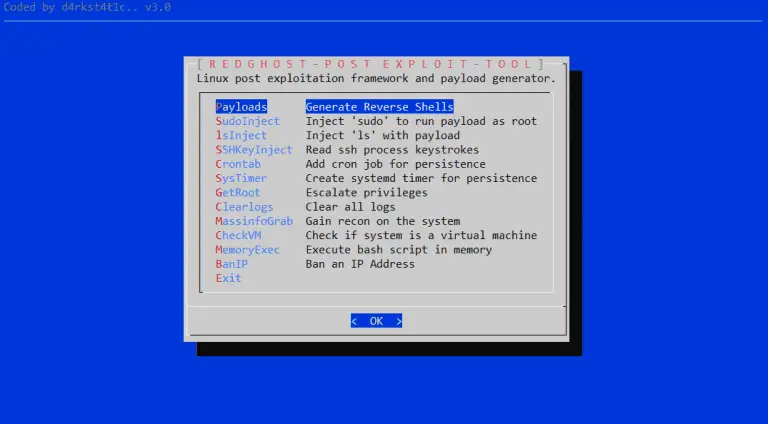
RedGhost Linux post-exploitation framework designed to assist red teams in persistence, reconnaissance, privilege escalation and leaving no...
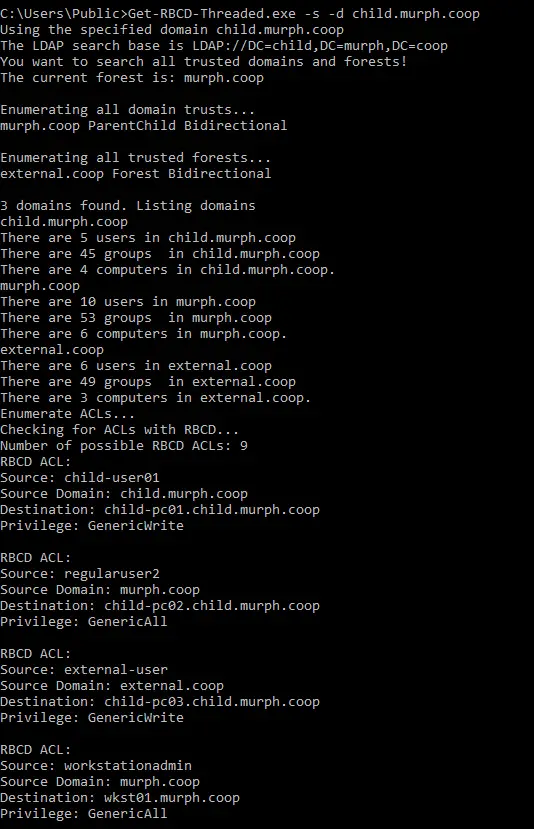
Get-RBCD-Threaded A tool to discover Resource-Based Constrained Delegation attack paths in Active Directory Environments. How it works...
FakeLogonScreen FakeLogonScreen is a utility to fake the Windows logon screen in order to obtain the user’s...
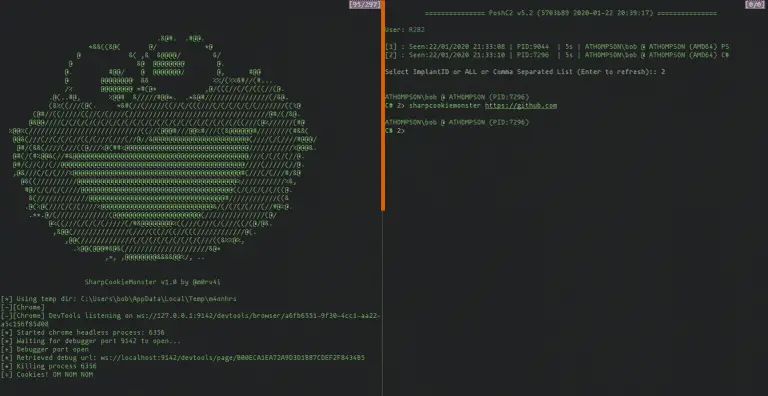
SharpCookieMonster This is a Sharp port of @defaultnamehere’s cookie-crimes module – full credit for their awesome work! This C#...
Invoke-EDRChecker: Checks running processes, process metadata, Dlls loaded into your current process
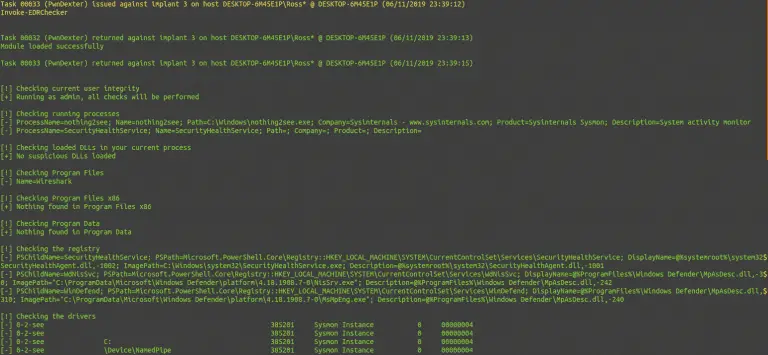

Invoke-EDRChecker: Checks running processes, process metadata, Dlls loaded into your current process
EDR-Checker Invoke-EDRChecker will check running processes, process metadata, Dlls loaded into your current process and each DLLs...
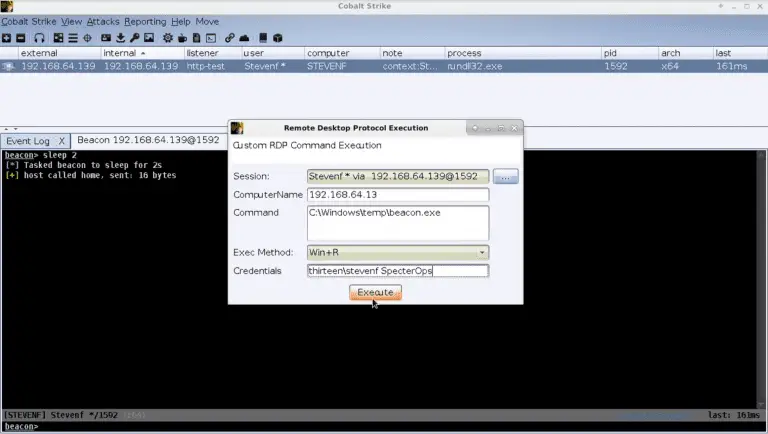
SharpRDP – Remote Desktop Protocol Console Application for Authenticated Command Execution How it works The terminal services...
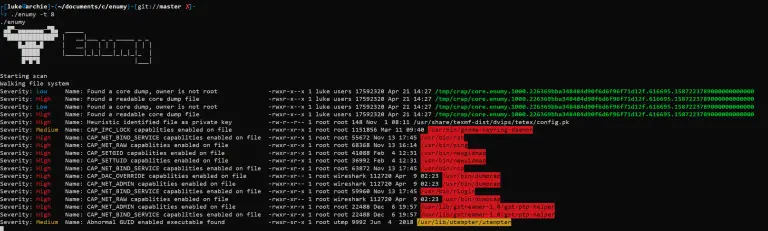
enumy Enumy is an ultra-fast portable executable that you drop on target Linux machine during a pentest or...
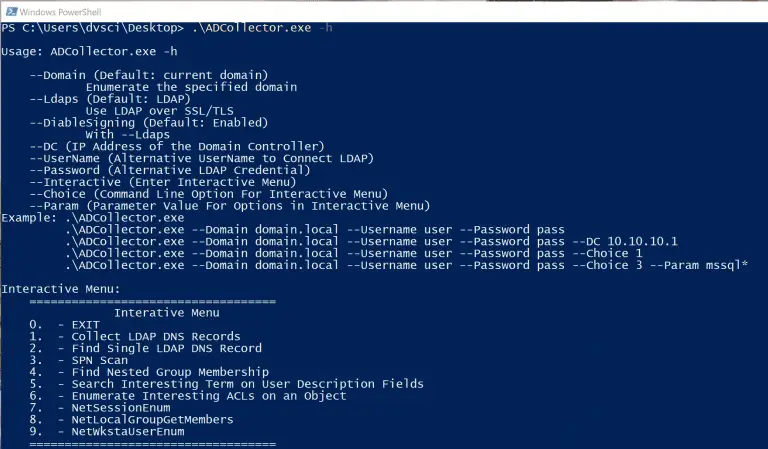
ADCollector ADCollector is a lightweight tool that enumerates the Active Directory environment to identify possible attack vectors....
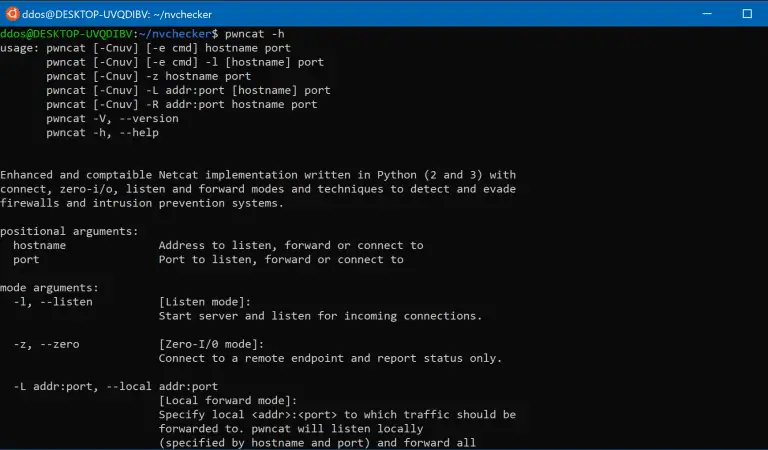
pwncat Netcat with Firewall and IPS evasion, bind and reverse shell, local and remote port-forward. Motivation Ever...
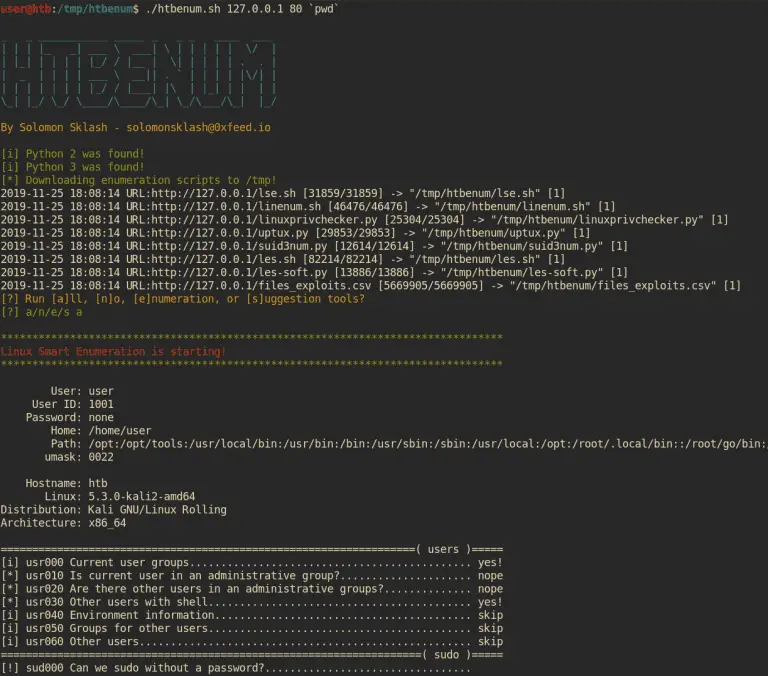
htbenum A Linux enumeration script for Hack The Box This script is designed for use in situations...
Chromepass – Hacking Chrome Saved Passwords Chromepass is a python-based console application that generates a windows executable...