BlueDelta: GRU-Linked Cyber Espionage Group Targets Critical European Networks
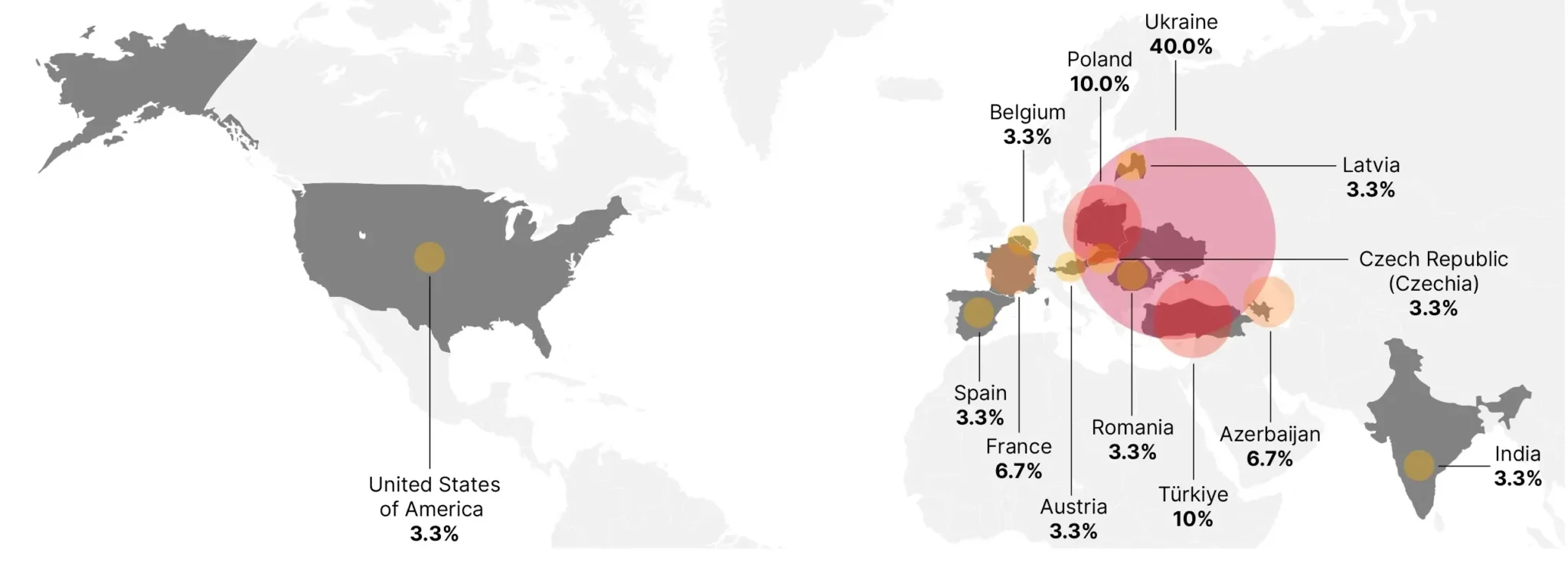
In a new report, cybersecurity firm Insikt Group has exposed a sophisticated cyber espionage campaign orchestrated by BlueDelta, a threat group with suspected ties to Russia’s GRU military intelligence agency. The campaign, which unfolded in multiple phases between April and December 2023, targeted key networks across Europe, including Ukraine’s Ministry of Defence, weapons manufacturers, and even a think tank in Azerbaijan.
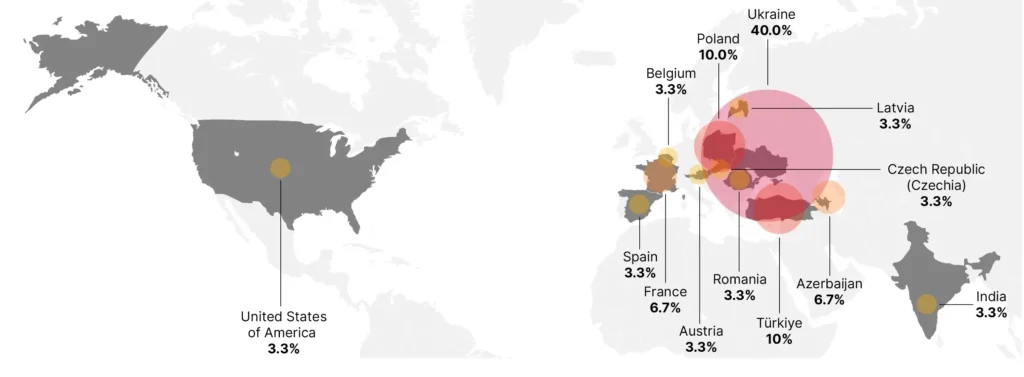
Image: Insikt Group
BlueDelta demonstrated a high degree of sophistication and adaptability, employing a multi-pronged approach to infiltrate their targets. The group utilized phishing emails, legitimate internet services like GitHub and InfinityFree, and “living off the land” techniques to deploy their information-stealing malware, Headlace.
One particularly alarming tactic involved credential harvesting campaigns aimed at users of Yahoo and UKR.net webmail services. BlueDelta even managed to bypass two-factor authentication and CAPTCHA challenges by leveraging compromised Ubiquiti routers.
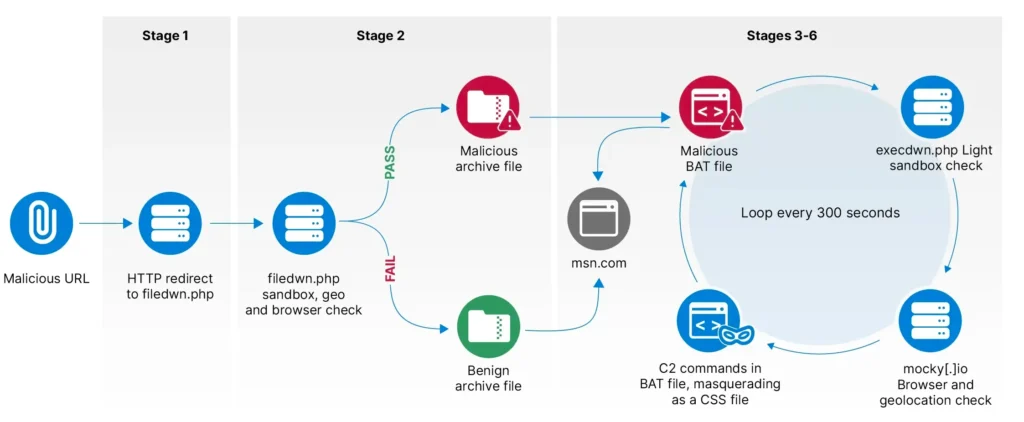
Image: Insikt Group
The report outlines three distinct phases of BlueDelta’s operations, each marked by evolving tactics and infrastructure to deploy the Headlace malware:
- Phase One (April – June 2023): BlueDelta initiated their campaigns using phishing emails, legitimate internet services (LIS), and living off-the-land binaries (LOLBins) to infiltrate networks. They abused services like GitHub, Mocky, and InfinityFree to host and execute their malicious scripts, making detection challenging.
- Phase Two (July – September 2023): The group refined their techniques, incorporating new first-stage redirection infrastructure on GitHub and employing advanced filtering scripts. This phase saw the use of geo-fencing and user agent checks to ensure the payloads reached only targeted systems.
- Phase Three (October – December 2023): BlueDelta further improved their operational security by moving to server-side PHP scripts, making their activities less visible to security researchers. They expanded their targeting scope, increasing the number of first-stage domains and payload variations.
The targets of BlueDelta’s espionage activities align closely with Russia’s strategic interests, particularly in the context of the ongoing conflict in Ukraine. The group’s focus on Ukrainian defense entities, weapons manufacturers, and European railway infrastructure suggests a concerted effort to gather intelligence on military capabilities and potential vulnerabilities.
Additionally, the targeting of a think tank in Azerbaijan indicates a broader interest in regional geopolitical developments and strategic policies.
Insikt Group’s report serves as a stark reminder of the persistent and evolving cyber threats facing critical infrastructure and government entities. The researchers urge organizations in targeted sectors to bolster their defenses, prioritize security training, and remain vigilant against BlueDelta’s sophisticated tactics.