Operation Diplomatic Specter: Chinese State-Sponsored Cyber Espionage Campaign Targeting Governments Across Three Continents
Palo Alto Networks’ Unit 42 threat research team has unveiled a sophisticated and persistent cyber espionage campaign, codenamed Operation Diplomatic Specter, attributed to a Chinese state-sponsored threat actor. The campaign has been targeting governmental entities in the Middle East, Africa, and Asia since late 2022, focusing on sensitive information related to diplomacy, military operations, and political affairs.

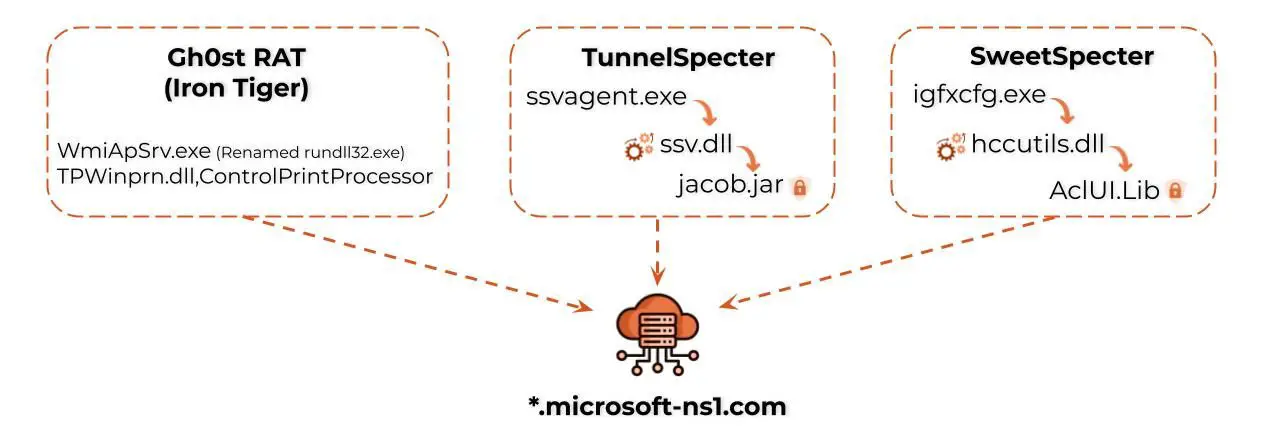
The Gh0st RAT sample and Specter malware family used in Operation Diplomatic Specter | Image: Unit 42
The campaign’s targets include diplomatic and economic missions, embassies, military operations, political meetings, and ministries within the targeted countries. The threat actor has displayed a keen interest in contemporary geopolitical developments, making daily attempts to exfiltrate valuable information. Among the critical sectors targeted are:
- Diplomatic and economic missions
- Embassies
- Military operations
- Political meetings
- Ministries of the targeted countries
- High-ranking officials
A distinctive aspect of Operation Diplomatic Specter is the use of previously undocumented backdoors, named TunnelSpecter and SweetSpecter. These tools allow the attackers to maintain a stealthy presence within the compromised networks, exfiltrate data, execute arbitrary commands, and deploy additional malware. The threat actor has shown adaptability, persistently attempting to regain access and maintain their foothold even after disruptions.
The Specter family of backdoors, TunnelSpecter and SweetSpecter, were instrumental in maintaining the threat actor’s presence within the targeted networks. Key features of these backdoors include:
TunnelSpecter:
- Data encryption and exfiltration via DNS tunneling
- Execution of arbitrary commands
- Storage of configuration data in unique registry keys
SweetSpecter:
- Communication with C2 using encrypted zlib packets over raw TCP
- Unique campaign ID format for compilation time
- Use of unique registry keys for configuration data storage
The group’s modus operandi involves infiltrating mail servers and searching them for information related to geopolitical events. They have utilized Exchange server exploits (ProxyLogon CVE-2021-26855 and ProxyShell CVE-2021-34473) for initial access, emphasizing the importance of patching known vulnerabilities. The threat actor’s exfiltration efforts included:
- Automated mailbox harvesting
- Targeted searches for specific keywords
- Exfiltration of entire archived inboxes and files
The intelligence gathered by the threat actor reveals a strategic interest in military operations, diplomatic missions, political figures, and international relations, particularly those involving China. The campaign’s focus areas include:
- China-related geopolitical and economic information
- OPEC and the energy industry
- Ministries of Foreign Affairs and Defense
- Military operations, drills, and personnel
- Relationships with the Biden administration
- Telecommunications technology
Unit 42 assesses with high confidence that the campaign is orchestrated by a single threat actor operating on behalf of Chinese state-aligned interests. The group’s tactics, techniques, and procedures (TTPs) exhibit characteristics typical of Chinese APT groups, including:
- Use of shared Chinese APT operational infrastructure
- Activity corresponding to working hours in UTC+8, indicative of operations from China
- Linguistic artifacts in Mandarin within the tools and scripts
- Use of tools commonly associated with Chinese APTs, such as customized Gh0st RAT samples, PlugX, Htran, and China Chopper
- Deployment of Chinese VPS providers for C2 servers
For more detailed information and technical analysis, please refer to the full report from Unit 42 Threat Research.





