CVE-2024-0333: Chrome Flaw Could Have Let Attackers Sneak in Malicious Extensions
Security researcher Malcolm Stagg has detailed a critical vulnerability in Google Chrome (designated CVE-2024-0333) that could have left users at risk of stealthy malicious extension installations. Stagg, known for his work in finding privilege escalation vulnerabilities, discovered the flaw after exploring ways to abuse Google Chrome’s Elevation Service.
The Vulnerability’s Core
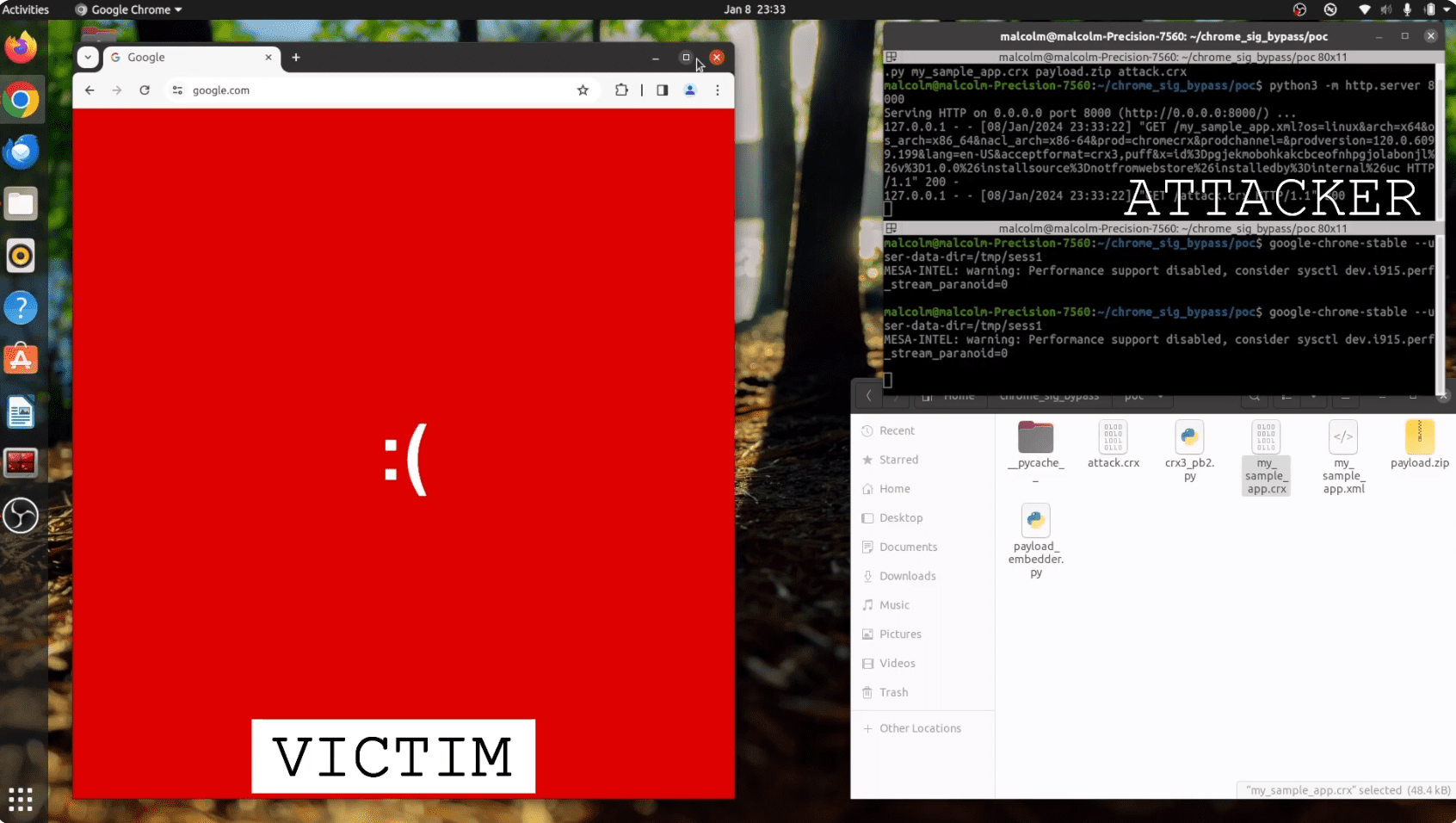
Stagg explains that the CVE-2024-0333 vulnerability stemmed from a peculiarity in how Chrome handles CRX files, the format used for extensions. By carefully manipulating the header of a CRX file and exploiting how the Minizip library processes headers with different archive tokens, an attacker could inject malicious extension data while preserving valid signatures.
The crux of CVE-2024-0333 lies in the ingenious exploitation of the CRX file’s header, an area assumed secure due to its role in containing file signatures. Stagg discovered that by injecting additional data into this header, specifically leveraging the ZIP file format’s End of Central Directory (EOCD) token, it was possible to bypass the signature verification process. This process, dependent on the Minizip library’s handling of ZIP archives, was susceptible to manipulation by inserting an EOCD64 token, redirecting the decompression process to a malicious payload within the size constraints of 64kB.
Potential Impact
While Stagg wasn’t able to directly exploit the flaw for local privilege escalation, he did outline a chilling attack scenario:
- Enterprise Compromise: Companies using Chrome with internal extension update servers were particularly vulnerable. An attacker in a shared network (e.g., a coffee shop) could mimic the internal update server and trick an employee’s Chrome into downloading the tampered malicious extension. This could lead to wide-ranging corporate network compromises.
Google’s Swift Response
Thankfully, Google acted with exceptional speed upon receiving Stagg’s report. A patch was applied to Chromium’s source code within 24 hours, followed shortly by a public fix in Chrome version 120.0.6099.216.
Staying Safe
While this specific vulnerability is fixed, users can protect themselves further by:
- Be Wary of Public Wi-Fi: Exercise caution when using Chrome on public networks, especially when connected to corporate systems.
- Only Install Trusted Extensions: Download extensions solely from the official Chrome Web Store or reputable sources.
- Regular Security Updates: Ensure your operating system and all applications, including Chrome, are consistently updated.
For the full technical breakdown of the vulnerability, along with a demonstration video, read Malcolm Stagg’s write-up.