forbidden v10.4 releases: Bypass 4xx HTTP response status codes
Forbidden
Bypass 4xx HTTP response status codes.
Script uses multithreading, and is based on brute-forcing so might have some false positives. Script uses colored output.
Results will be sorted by HTTP response status code ascending, content length descending, and ID ascending.
Extend this script to your liking.
Tested on Kali Linux v2021.4 (64-bit).
Made for educational purposes. I hope it will help!
Tests:
- various HTTP methods,
- various HTTP methods with ‘Content-Length: 0’ header,
- cross-site tracing (XST) with HTTP TRACE and TRACK methods,
- file upload with HTTP PUT method,
- various HTTP method overrides,
- various HTTP headers,
- various URL overrides,
- URL override with two ‘Host’ headers,
- various URL path bypasses,
- basic-authentication/authorization including null session,
- broken URL parser check.
Changelog v10.4
- argument parsing code rebase and improved few other stuff,
- boolean options / arguments no longer require
yesornovalue.
Install
apt-get install -y curl
https://github.com/ivan-sincek/forbidden.git
pip3 install -r requirements.txt
Use
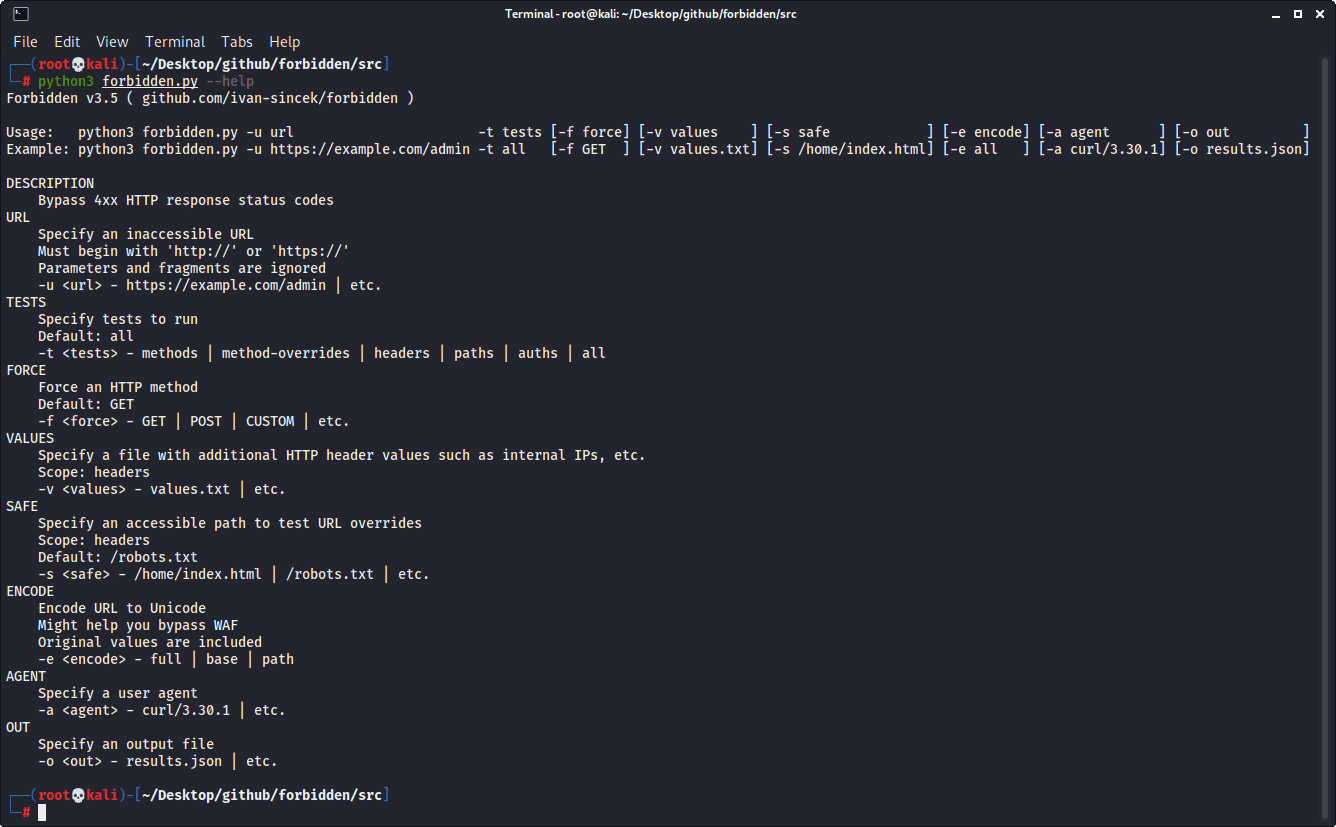
Automate the script:
count=0; for subdomain in $(cat subdomains_403.txt); do count=$((count+1)); echo “#${count} | ${subdomain}”; python3 forbidden.py -u “${subdomain}” -t all -f GET -e path -o “forbidden_results_${count}.json”; done
Download a user agent list from here.
Copyright (c) 2021 Ivan Šincek
Source: https://github.com/ivan-sincek/






