capa v6.1 releases: identify capabilities in executable files
capa
capa detects capabilities in executable files. You run it against a PE file or shellcode and it tells you what it thinks the program can do. For example, it might suggest that the file is a backdoor, is capable of installing services, or relies on HTTP to communicate.
Changelog v6.1
New Features
- ELF: implement import and export name extractor #1607 #1608 @Aayush-Goel-04
- bump pydantic from 1.10.9 to 2.1.1 #1582 @Aayush-Goel-04
- develop script to highlight features not used during matching #331 @Aayush-Goel-04
New Rules (8)
- executable/pe/export/forwarded-export ronnie.salomonsen@mandiant.com
- host-interaction/bootloader/get-uefi-variable jakub.jozwiak@mandiant.com
- host-interaction/bootloader/set-uefi-variable jakub.jozwiak@mandiant.com
- nursery/enumerate-device-drivers-on-linux @mr-tz
- anti-analysis/anti-vm/vm-detection/check-for-foreground-window-switch ervin.ocampo@mandiant.com
- linking/static/sqlite3/linked-against-cppsqlite3 still@teamt5.org
- linking/static/sqlite3/linked-against-sqlite3 still@teamt5.org
Modified rules (9)
- anti-analysis/anti-forensic/self-deletion/self-delete.yml
- collection/browser/gather-chrome-based-browser-login-information.yml
- collection/browser/gather-firefox-profile-information.yml
- data-manipulation/encoding/base64/decode-data-using-base64-via-dword-translation-table.yml
- host-interaction/process/inject/free-user-process-memory.yml
- lib/get-os-version.yml
- nursery/deserialize-json-in-dotnet.yml
- nursery/serialize-json-in-dotnet.yml
- persistence/authentication-process/act-as-credential-manager-dll.yml
Renamed rules (1)
Bug Fixes
- rules: fix forwarded export characteristic #1656 @RonnieSalomonsen
- Binary Ninja: Fix stack string detection #1473 @xusheng6
- linter: skip native API check for NtProtectVirtualMemory #1675 @williballenthin
- OS: detect Android ELF files #1705 @williballenthin
- ELF: fix parsing of symtab #1704 @williballenthin
- result document: don’t use deprecated pydantic functions #1718 @williballenthin
- pytest: don’t mark IDA tests as pytest tests #1719 @williballenthin
capa explorer IDA Pro plugin
- fix unhandled exception when resolving rule path #1693 @mike-hunhoff
Usage
See capa -h for all supported arguments and usage examples.
tips and tricks
only run selected rules
Use the -t option to run rules with the given metadata value (see the rule fields rule.meta.*). For example, capa -t william.ballenthin@mandiant.com runs rules that reference Willi’s email address (probably as the author), or capa -t communication runs rules with the namespace communication.
IDA Pro integrations
You can run capa from within IDA Pro. Run capa/main.py via File - Script file... (or ALT + F7). When running in IDA, capa uses IDA’s disassembly and file analysis as its backend. These results may vary from the standalone version that uses vivisect. IDA’s analysis is generally a bit faster and more thorough than vivisect’s, so you might prefer this mode.
When run under IDA, capa supports both Python 2 and Python 3 interpreters. If you encounter issues with your specific setup, please open a new Issue.
Additionally, capa comes with an IDA Pro plugin located in the capa/ida directory: the explorer.
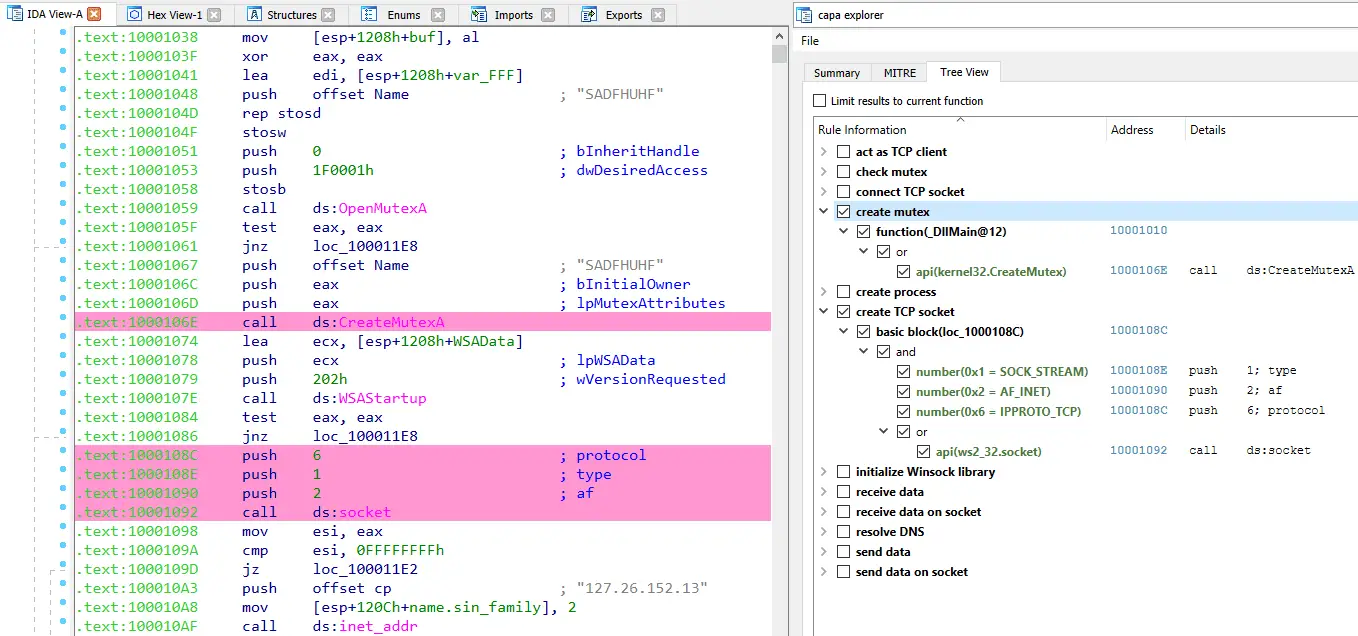
capa explorer
The capa explorer allows you to interactively display and browse capabilities capa identified in a binary. As you select rules or logic, capa will highlight the addresses that support its analysis conclusions. We like to use capa to help find the most interesting parts of a program, such as where the C2 mechanism might be.
To install the plugin, you’ll need to be running IDA Pro 7.4 or 7.5 with either Python 2 or Python 3. Next make sure pip commands are run using the Python install that is configured for your IDA install:
- Only if running Python 2.7, run command
$ pip install https://github.com/williballenthin/vivisect/zipball/master - Run
$ pip install .from capa root directory - Open IDA and navigate to
File > Script file…orAlt+F7 - Navigate to
<capa_install_dir>\capa\ida\and chooseida_capa_explorer.py
Download
Copyright (C) 2020 Mandiant, Inc.