WhatWaf v1.9 releases: Detect & bypass web application firewalls and protection systems
WhatWaf is an advanced firewall detection tool whose goal is to give you the idea of “There’s a WAF?”. WhatWaf works by detecting a firewall on a web application and attempting to detect a bypass (or two) for said firewall, on the specified target.
Features
- Ability to run on a single URL with the
-u/--urlflag - Ability to run through a list of URL’s with the
-l/--listflag - Ability to detect over 40 different firewalls
- Ability to try over 20 different tampering techniques
- Ability to pass your own payloads either from a file, from the terminal, or use the default payloads
- Default payloads that are guaranteed to produce at least one WAF triggering
- Ability to bypass firewalls using both SQLi techniques and cross-site scripting techniques
- Ability to run behind multiple proxy types (socks4, socks5, http, https, and Tor)
- Ability to use a random user-agent, personal user agent, or custom default user agent
- Auto-assign protocol to HTTP or ability to force protocol to HTTPS
- A built-in encoder so you can encode your payloads into the discovered bypasses
- More to come…
Changelog v1.9
- Completely deprecates setup.sh in favor of setup.py
Install
sudo -s << EOF
git clone https://github.com/ekultek/whatwaf.git
cd whatwaf
chmod +x whatwaf.py
pip2 install -r requirements.txt
./whatwaf.py –help
Usage
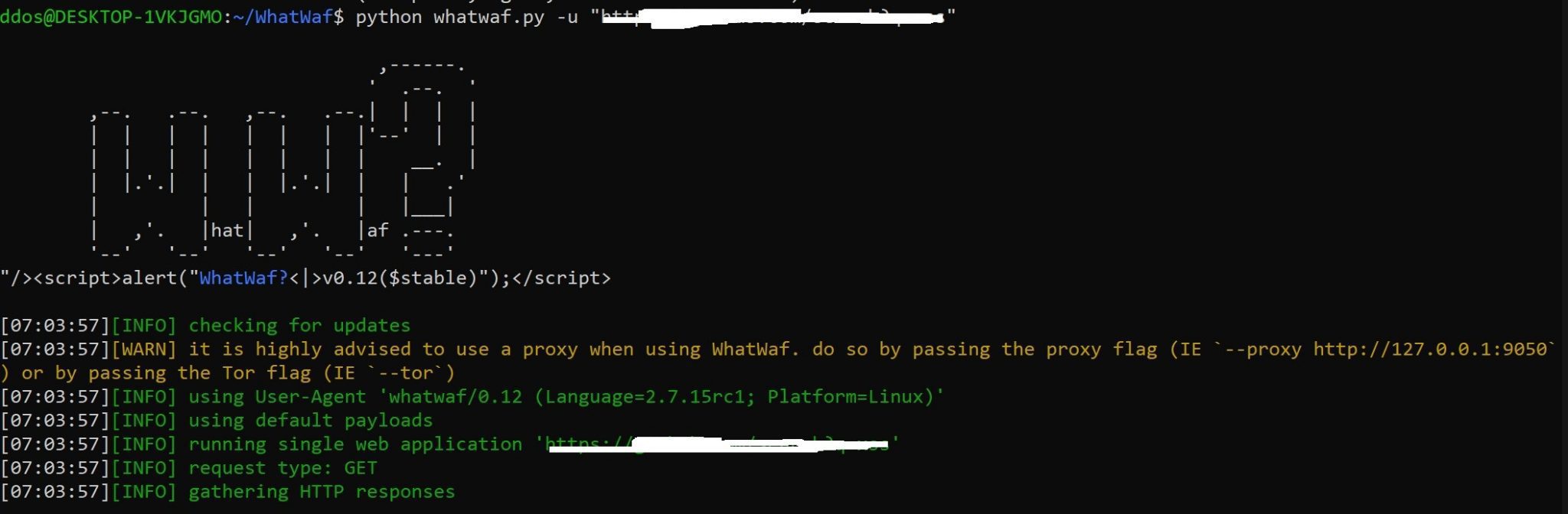
First, we’ll run the website through WhatWaf and figure out which firewall protects it (if any):
Next, we’ll go to that website and see what the page looks like:
Hmm.. that doesn’t really look like Cloudflare does it? Let’s see what the headers say:
And finally, let’s try one of the bypasses that it tells us to try:
Demo video
Demo Video from Ekultek on Vimeo.
Copyright (C) 2018 Ekultek
Source: https://github.com/Ekultek/










