echidna v2.2.1 releases: Ethereum fuzz testing framework
echidna
Echidna is a weird creature that eats bugs and is highly electrosensitive (with apologies to Jacob Stanley)
More seriously, Echidna is a Haskell program designed for fuzzing/property-based testing of Ethereum smarts contracts. It uses sophisticated grammar-based fuzzing campaigns based on a contract ABI to falsify user-defined predicates or Solidity assertions. We designed Echidna with modularity in mind, so it can be easily extended to include new mutations or test specific contracts in specific cases.
Features
- Generates inputs tailored to your actual code
- Optional corpus collection, mutation and coverage guidance to find deeper bugs
- Optional Slither integration to extract useful information before the fuzzing campaign
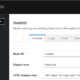
- Curses-based retro UI, text-only or JSON output
- Automatic testcase minimization for quick triage
- Seamless integration into the development workflow
- Maximum gas usage reporting of the fuzzing campaign
- Support for a complex contract initialization with Etheno and Truffle
Changelog v2.2.1
- Shanghai fork support with hevm 0.51.3 (#1090)
- Fixed coverage collection for delegatecalls (#1083)
- Added events to JSON output (#1069)
- Changed event sequence to be displayed on new lines (#1079)
- Improved “No tests found in ABI” error message (#1077)
- Refactored code (#1070, #1074)
Installation
docker is recommended to install Echidna.
docker pull trailofbits/echidna
docker run trailofbits/echidna
for example
docker run -v `pwd`:/src trailofbits/echidna echidna-test /src/solidity/cli.sol
If you’d prefer to build from the source, use Stack. stack install . should build and compile echidna-test in ~/.local/bin You will need to link against libreadline and libsecp256k1 (built with recovery enabled), which should be installed with the package manager of your choosing. If you’re getting errors building related to linking, try tinkering with –extra-include-dirs and –extra-lib-dirs.
Use
Copyright (C) 2018