Microsoft: Spectre security patch will slow down your PC
On Tuesday, Microsoft said patches released to protect against Meltdown and Specter vulnerabilities led some PCs and servers to slow down, with the significantly lower performance for systems running on older Intel processors. According to a blog post from Microsoft, these security patches can also cause some computers based on the AMD chipset to crash, according to complaints from the company’s customers.
Affected, Intel shares fell 1.4%, AMD shares also fell nearly 4%. Over the past week, AMD shares rose nearly 20%, due to the most affected by the security vulnerabilities Intel chip, prompting investors speculation that its market share may be snapped by AMD.
In a blog post, Microsoft executive Tim Terry Myerson wrote: “Under the Confidentiality Agreement, we (and some others in the industry) learned of this vulnerability a few months ago and immediately started developing engineering mitigation measures, But also updated our cloud infrastructure. ”
- With Windows 10 on newer silicon (2016-era PCs with Skylake, Kabylake or newer CPU), benchmarks show single-digit slowdowns, but we don’t expect most users to notice a change because these percentages are reflected in milliseconds.
- With Windows 10 on older silicon (2015-era PCs with Haswell or older CPU), some benchmarks show more significant slowdowns, and we expect that some users will notice a decrease in system performance.
- With Windows 8 and Windows 7 on older silicon (2015-era PCs with Haswell or older CPU), we expect most users to notice a decrease in system performance.
- Windows Server on any silicon, especially in any IO-intensive application, shows a more significant performance impact when you enable the mitigations to isolate untrusted code within a Windows Server instance. This is why you want to be careful to evaluate the risk of untrusted code for each Windows Server instance and balance the security versus performance tradeoff for your environment.
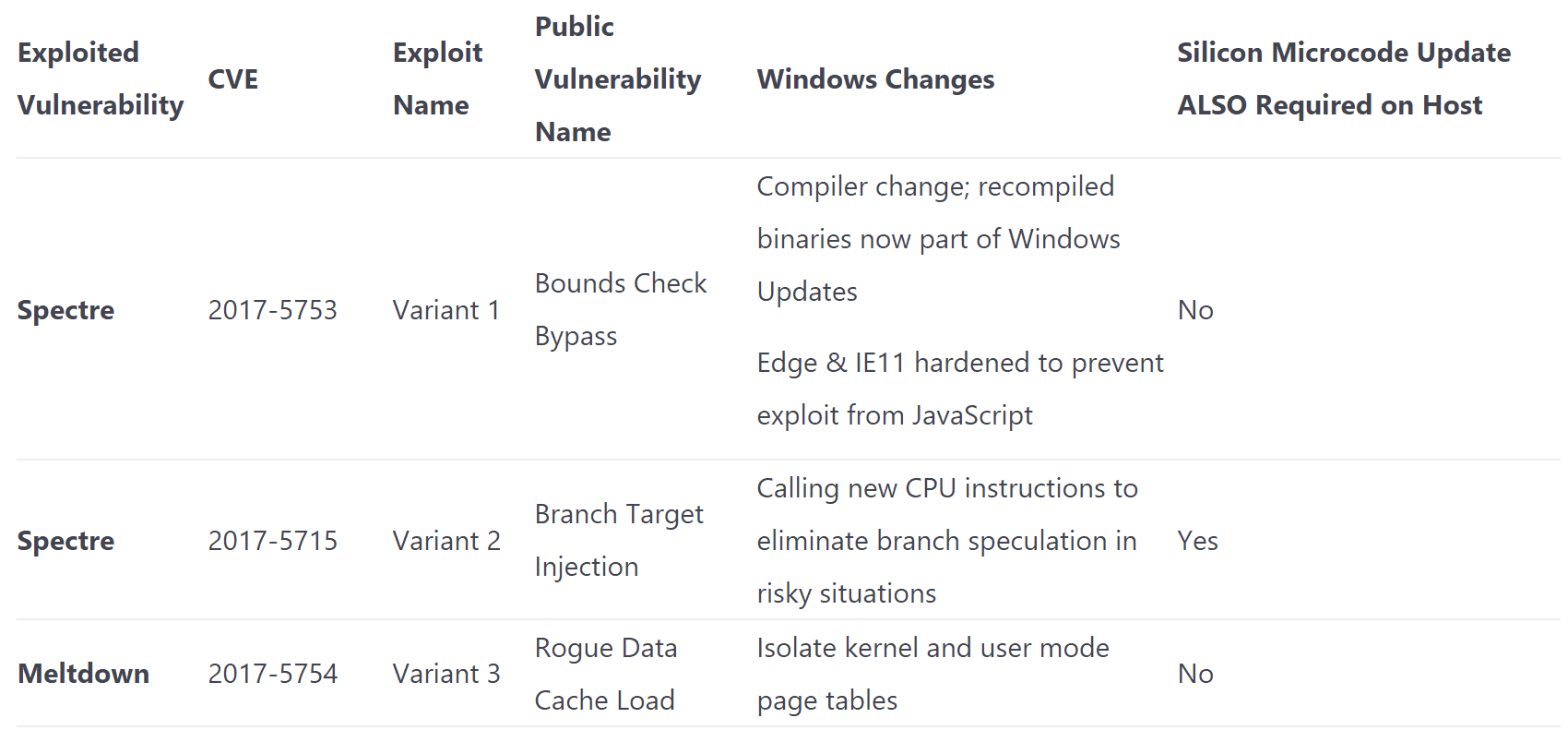
Security researchers disclosed the vulnerabilities on January 3, both of which affect virtually every modern computing device based on Intel, AMD, and ARM chips. Meltdown and Spectre are two memory corruption vulnerabilities, hackers can exploit these vulnerabilities to bypass the operating system and other security software to steal most types of computers, mobile phones and cloud service user password or encryption keys on the device.
Intel said home and business PC users should not experience significant slowdowns when doing common tasks like reading mail, writing files or accessing digital photos. The company said last week that its fix to its microchip would not slow down to address the security issue, and denied that the flaws would cause a dramatic drop in performance.
AMD also said it does not have to worry too much about the threat, saying its product is “zero-risk” to the Meltdown vulnerability, while a variant of the Specter vulnerability can be addressed through software updates from vendors such as Microsoft. But on Tuesday, AMD said it learned of some older processors that have had problems installing the security update that Microsoft released over the weekend. Microsoft said the company is working with AMD to solve the problem.
Apple also released an upgraded version of the operating system on Monday to address the security breach.
Reference: Microsoft