ossec-hids v3.7 releases: Open Source Host-based Intrusion Detection System
OSSEC
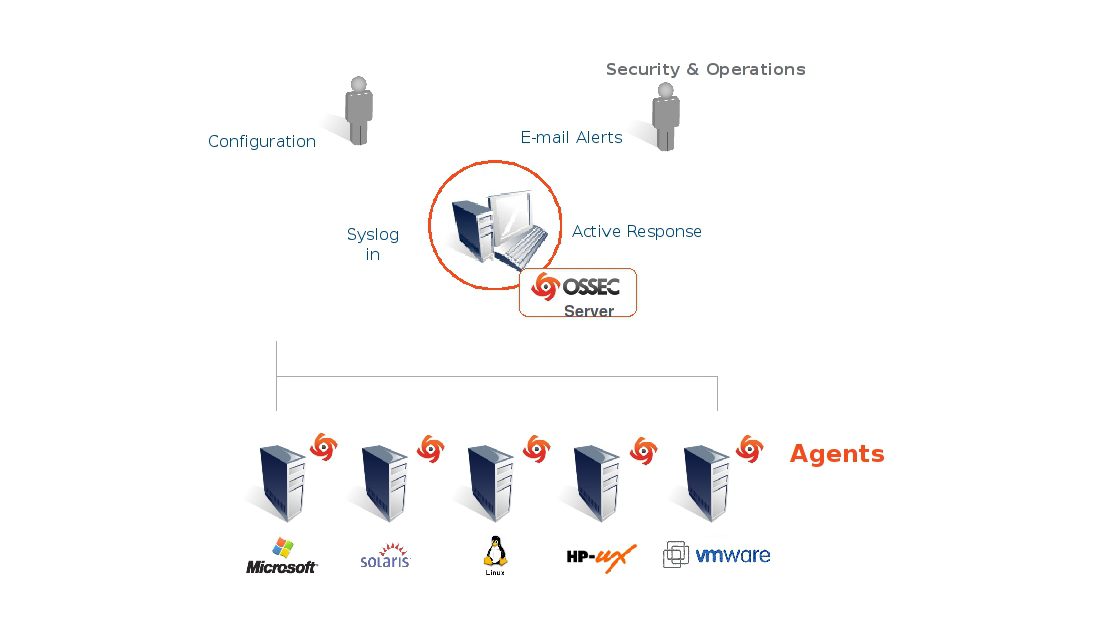
OSSEC is a full platform to monitor and control your systems. It mixes together all the aspects of HIDS (host-based intrusion detection), log monitoring and SIM/SIEM together in a simple, powerful and open-source solution. It has a powerful correlation and analysis engine, integrating log analysis, file integrity checking, Windows registry monitoring, centralized policy enforcement, rootkit detection, real-time alerting and active response. It runs on most operating systems, including Linux, OpenBSD, FreeBSD, MacOS, Solaris and Windows.
Feature
Watching
Alerting
Everywhere
- doc/manage_agents.txt: minor update by @icy in #1835
- Unbound DNSSEC failure rules by @ddpbsd in #1840
- Silence a warning in json output by @ddpbsd in #1841
- Travis with arm64 by @nurse in #1850
- Set PCRE2_SYSTEM=no earlier in the build for winagent by @ddpbsd in #1865
- 2 fixes for Solaris by @ddpbsd in #1878
- Add ossec-aws-waf.sh by @Midi12 in #1846
- Support arm64 packaging by @nurse in #1809
- Support Ubuntu Bionic arm64 by @nurse in #1887
- Update rootkit_files.txt by @Skactor in #1899
- Revert os_dns stuff by @ddpbsd in #1891
- Fix regexp import in ossec-batch-manager.pl by @seren in #1913
- Fix for PR 1889 by @atomicturtle in #1918
- Adding lighttpd decoder/rules by @Nono-m0le in #1787
- Fix NetBSD build. Without this analysisd can’t understand regex. by @giannidaprile in #1919
- Adding wait to travis builds by @atomicturtle in #1920
- Adding screenshots by @atomicturtle in #1921
- Update README.md by @atomicturtle in #1922
- Resize images 800×600 by @atomicturtle in #1923
- Update README.md by @atomicturtle in #1924
- Write md5 and sha1 checksums for newly added files. by @swindmill in #1940
- WIP: journald reader by @sempervictus in #1852
- Attempt to pull a valgrind that exists. by @ddpbsd in #1941
- Closes issue #1949 by @atomicturtle in #1951
- Shuffle some variables around by @ddpbsd in #1875
- [Documentation] Updating Broken Documentation Links by @lyellread in #1974
- Add libsystemd-dev to package list by @ddpbsd in #1972
- Fix for change in named query log format by @ddpbsd in #1936
- Closes issue #1970 by @atomicturtle in #1979
- Update ssh_asa-fwsmconfig_diff by @tonoitp in #1967
- exclude on Overlay and aufs by @atomicturtle in #1952
- 3 new rootkits found in the wild on github by @nfsec in #2017
- active response script for nftables by @ChristianBeer in #2029
- Updating version fields by @atomicturtle in #2032
- Updating changelog by @atomicturtle in #2035
Copyright (C) 2018 Trend Micro Inc






