Over 63,000 Unpatched Microsoft Exchange Servers Vulnerable to RCE Attack
In a concerning turn of events, over 63,000 Microsoft Exchange servers remain exposed online, failing to implement the necessary patches against the critical remote code execution (RCE) vulnerability, CVE-2023-36439. This vulnerability, among the four security flaws addressed by Microsoft’s November 2023 Patch Tuesday update, poses a significant threat to organizations due to its potential for severe exploitation.
According to the Shadowserver Foundation, a non-profit entity committed to bolstering internet security, these servers are susceptible to the CVE-2023-36439 flaw. This vulnerability, identified through the servers’ x_owa_version header, affects Exchange Server 2016 and 2019, and it holds a significant CVSS score of 8.0.
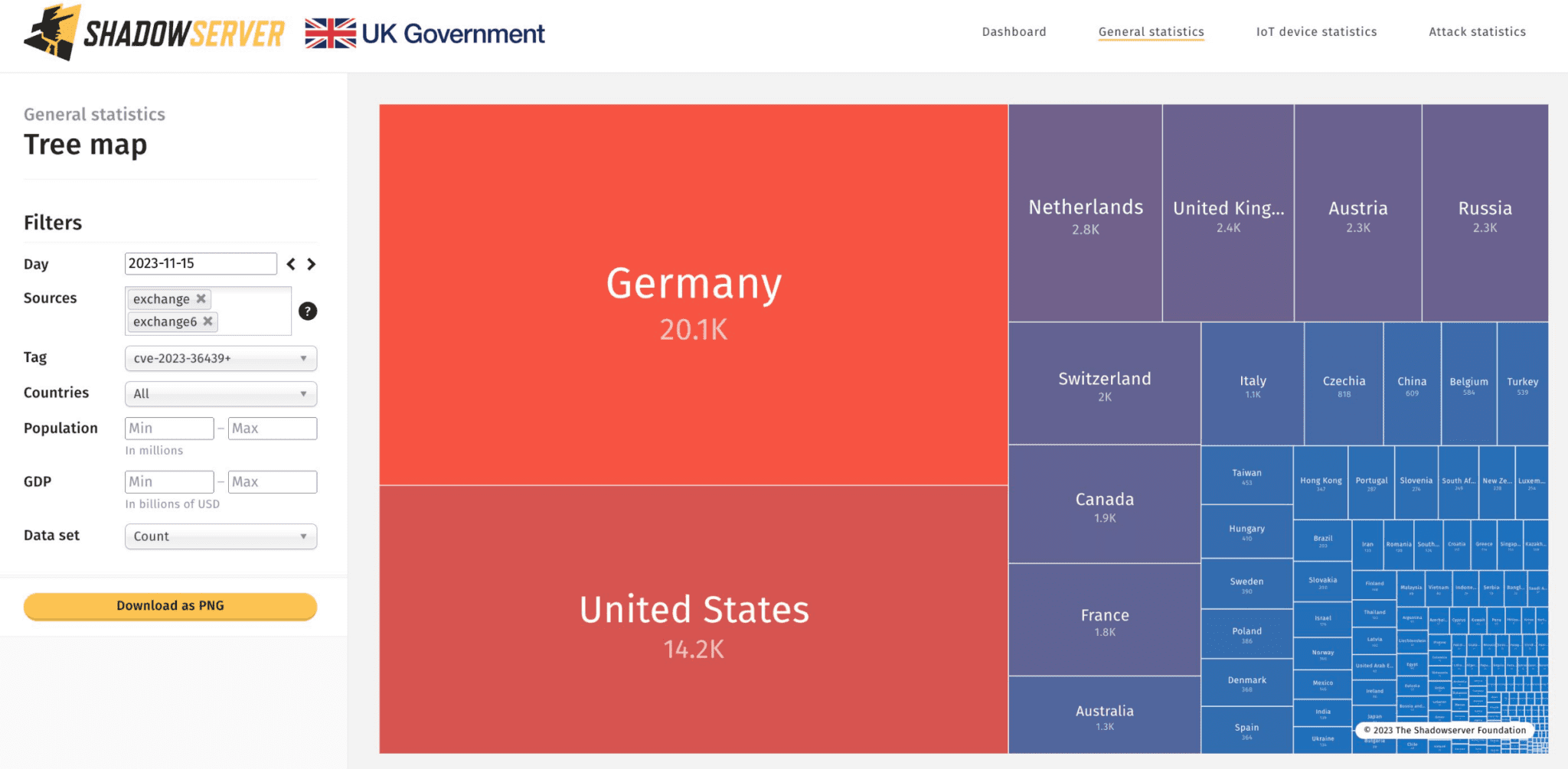
Exchange servers vulnerable to CVE-2023-36439 | Image: Shadowserver
Microsoft’s analysis reveals that exploitation requires the attacker to be authenticated as a valid Exchange user. This vulnerability, if leveraged, could grant an attacker remote code execution rights on the server mailbox backend as NT AUTHORITY\SYSTEM. Essentially, it’s a gateway for attackers to execute code remotely on a victim’s server.
Kevin Breen, Senior Director of Threat Research at Immersive Labs, emphasizes the urgency for organizations using Microsoft Exchange Server to prioritize the patching of this vulnerability. CVE-2023-36439 could enable attackers to install malicious software on an Exchange server. Although this flaw technically demands the attacker to be authenticated to the target’s local network, Breen notes that even a pair of phished Exchange credentials could suffice to gain this access.
Breen points out that attackers often achieve initial access through social engineering, with spear-phishing being a common tactic. Once inside the network, they search for other vulnerable targets. He warns that even if an Exchange Server does not offer internet-facing authentication, it doesn’t guarantee safety against such attacks.
This vulnerability is accompanied by three other Exchange bugs that Microsoft has marked as “exploitation more likely”: CVE-2023-36050, CVE-2023-36039, and CVE-2023-36035. Together, they form a quartet of security challenges that organizations must swiftly address.
Organizations running Microsoft Exchange Server should prioritize patching CVE-2023-36439 immediately. Additionally, organizations should implement additional security measures, such as multi-factor authentication (MFA) and network segmentation, to further protect their systems. MFA adds an extra layer of security by requiring users to provide a second factor, such as a code from their phone, in addition to their password. Network segmentation creates isolated network segments, limiting the spread of potential attacks if a breach occurs.