TLS Prober: A tool to fingerprint SSL/TLS servers
TLS Prober
TLS Prober is a tool for identifying the implementation in use by SSL/TLS servers. It analyses the behavior of a server by sending a range of probes then comparing the responses with a database of known signatures. Key features include:
- Requires no knowledge of the server configuration.
- Does not rely on the supported cipher suites (since administrators often change those).
- Successfully identifies openssl, schannel, Java (JSSE), wolfSSL (previously CyaSSL), GnuTLS, MatrixSSL, mbedTLS (previously PolarSSL).
- Supports both pure SSL/TLS protocols like HTTPS and those that use STARTTLS such as SMTP and POP3.
- Resilient against differences in the build options used by a given server.
- Extensible – you can easily record the signatures of additional implementations.
Installation
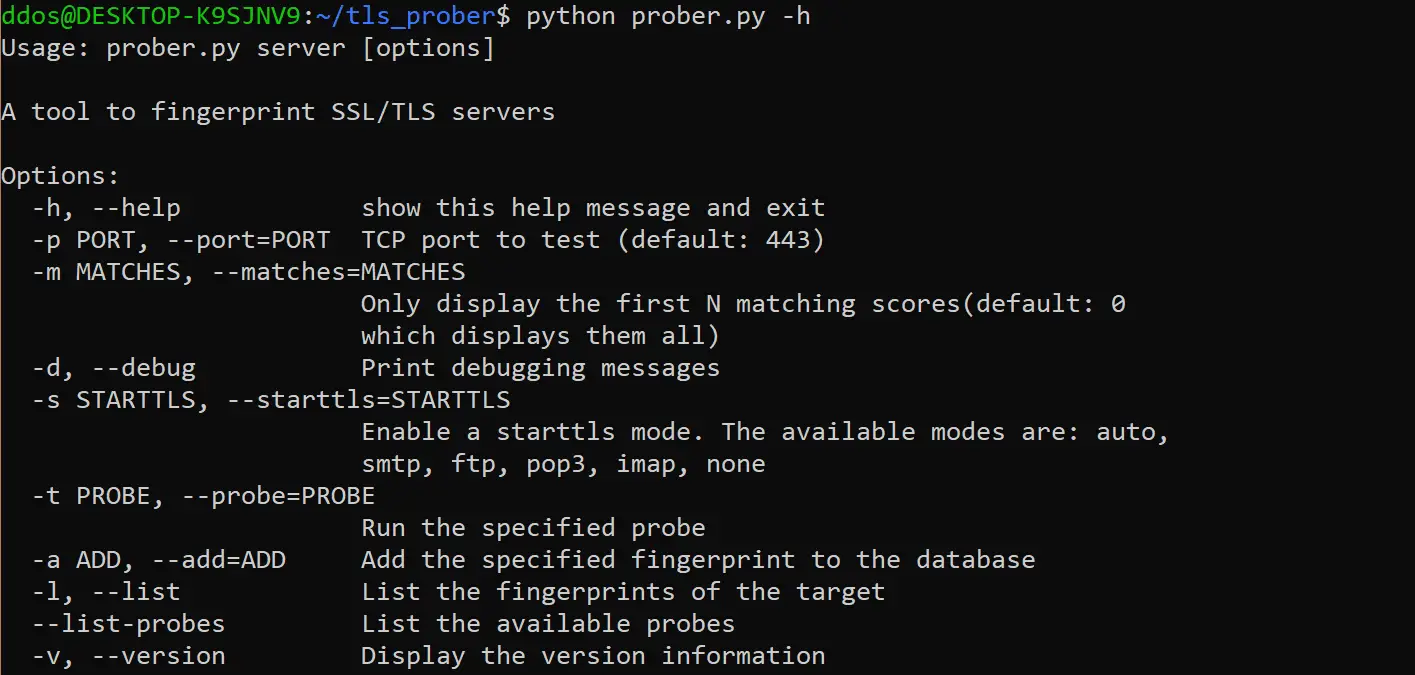
Usage
Copyright (c) 2014-2015 Richard Moore <rich@kde.org>
Source: https://github.com/WestpointLtd/