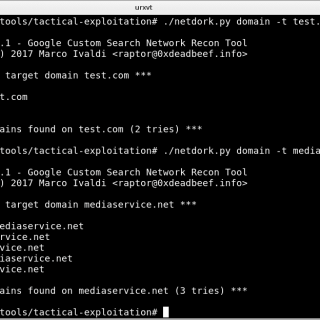
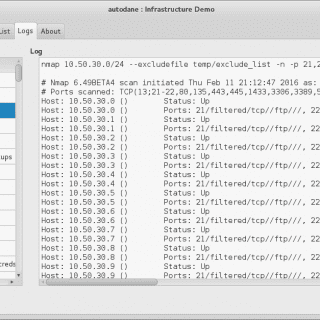
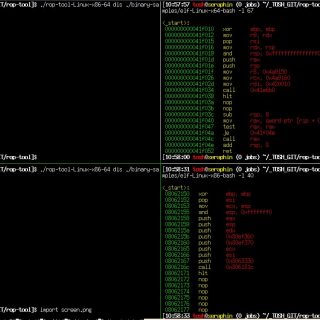
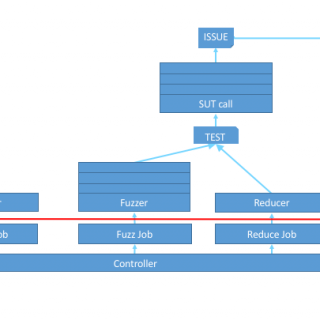
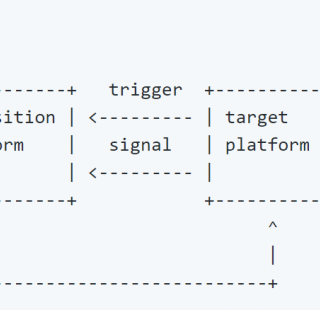
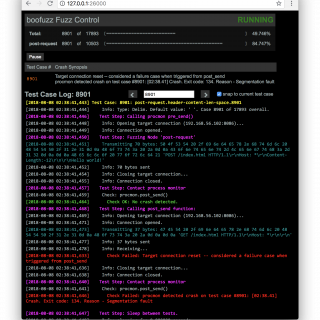
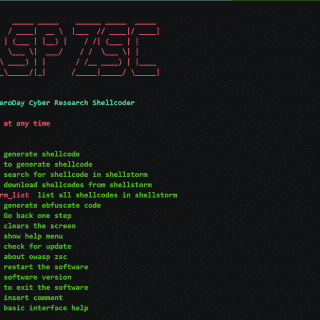
tactical-exploitation: Modern tactical exploitation toolkit
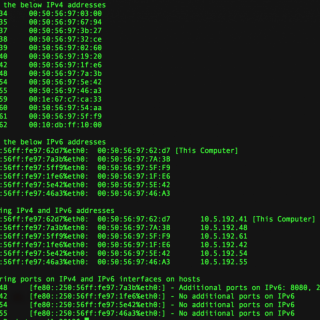
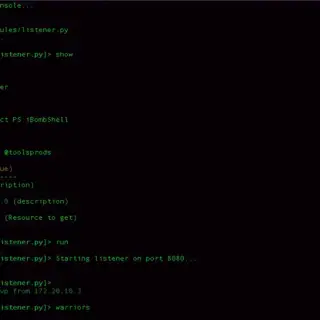
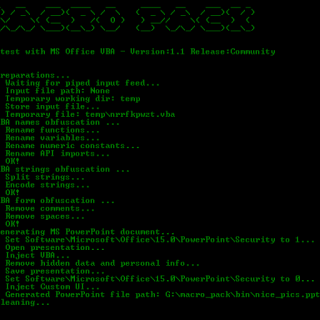
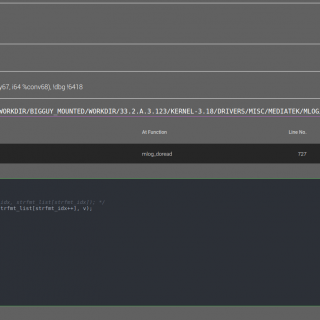
tactical-exploitation I’ve always been a big proponent of a tactical approach to penetration testing that does not focus on exploiting known software vulnerabilities but relies on old-school techniques such as information gathering and brute...